Overlays For Androids For Criminal Convenience
January 25, 2025
Android Overlays are a powerful feature in the Android operating system. Theses allow apps to display content over other apps or over the system user interfaces. Ultimately this results in the user experience being more, well, user-friendly. So why is it important? This is useful in many ways, such as for displaying persistent notifications, those cheeky Android chat heads that float around the screen, or for using accessibility features. You know what’s coming next. Those handy capabilities can also be misused by cybercriminals to create deceptive interfaces and put them in apps to trick users into performing unintended actions, such as entering sensitive information.
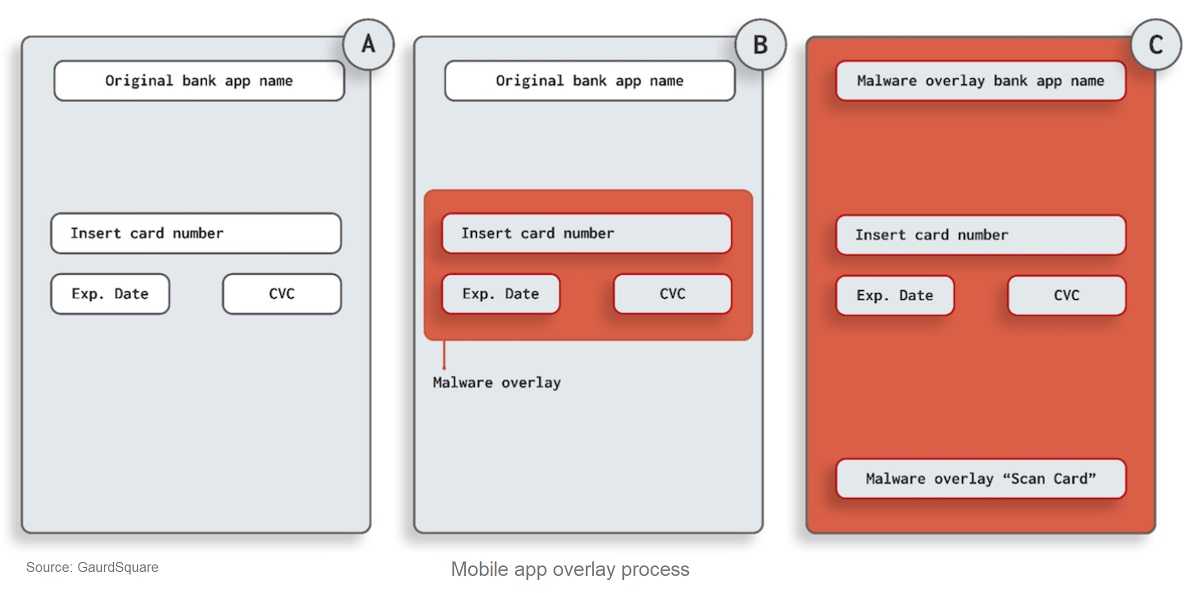
One out right now that is catching a lot of people is placing a full window overlay over another app's legitimate screen. This allows an attacker to capture every input into the device. So, if it’s a financial institution’s app, they’ll get the login credentials, for example. Perhaps a more nefarious use is to capture social media login credentials. You might think this is harmless, but many people use their social media usernames and passwords to log in to other accounts, making that combination quite useful.
It’s Secure, right?
The primary security concern with overlays is their potential to be used for phishing attacks. For instance, a malicious app can display an overlay that looks identical to a legitimate app's login screen, tricking the user into entering their credentials. This technique is more commonly known as “clickjacking, but is often referred to as "tapjacking" on Android apps. While you think you’re entering your information into your financial institution’s app, for instance, the overlay allows the criminals to capture that info instead of it going into your app.
Preventing Misuse
 Android has security features to help with respect to overlays. You can check your Android device by going to Settings >Apps > Options > Special access > Appear on top. This may be a little different depending on what version of the operating system you’re using. In any case, disable any special access feature that you don’t recognize or that don’t require the use of overlays. It might surprise you that some actually do. If you aren’t sure, disable it and find out if the app works without it. If not, go turn it back on.
Android has security features to help with respect to overlays. You can check your Android device by going to Settings >Apps > Options > Special access > Appear on top. This may be a little different depending on what version of the operating system you’re using. In any case, disable any special access feature that you don’t recognize or that don’t require the use of overlays. It might surprise you that some actually do. If you aren’t sure, disable it and find out if the app works without it. If not, go turn it back on.
Definitely use multi-factor authentication whenever available; and install an anti-malware service on all of your devices. And if you didn’t guess already, don’t use the same login and password combination for multiple accounts, especially social media or others that have a lot of information about you connected to them (think Apple or Google credentials).