It’s no surprise that phishing is still prevalent in the cyber world. In fact, it remains the top way malware gets onto devices, and it still excels at getting people to give up their personal information. Phishing scams, and they are aplenty, aim to deceive individuals into divulging sensitive information such as passwords, payment card details, or all other kinds of personal data; some that you don’t even think is all that useful to someone trying to scam you.
The fact is, any piece of information a cybercriminal has on you can be put to use in some sort of scam. That’s why they are so persistent at attempting to get to all the information possible. And as we are staying on top of the attacks better now, they are also getting better at fooling us.
Most often, we see links in email or in text messages that encourage us to click them. However, in a recent scam, Check Point security is warning about the use of images to get those clicks going. It’s quite clever because we typically can call out phishing by finding errors in grammar, graphics, or use of the language. But if you get an image, those are not a factor. In this particular scam, the image may appear to come from a big retailer, such as Amazon or Target, promising special perks.
Here are some valuable tips to avoid falling victim to phishing scams:
Be Vigilant and Verify
Be skeptical of unsolicited emails, messages, or phone calls asking you to click a link or image or ask for personal information. Legitimate organizations typically do not request sensitive data via email or other insecure channels. Even if they do, log into your accounts to check for these notifications rather than clicking something in a message.
Verify the authenticity of the sender by checking email addresses, domain names, and website URLs. Cross-reference any suspicious requests or offers by contacting the organization directly using their official contact information. Don’t reply directly to any of the messages. The hackers are waiting on the other end.
Strengthen Password Security
Create strong, unique passwords for each of your accounts and change them regularly. Enable two-factor authentication (2FA) whenever available, as it adds an extra layer of protection by requiring a secondary verification method, such as a code sent to your phone. However, if you have the option to use a hardware key, an authenticator app, or key fob that generates random codes, choose one of those over email or text codes.
Educate Yourself
Stay informed about the latest phishing techniques and scams. Be cautious of common phishing red flags, such as poor grammar, urgent requests for personal information, or offers that seem too good to be true. These do still exist and aren’t slowing down.
Three well-known phishing scams
There are numerous phishing scams and endless versions of many of them. Following are a few that come around on a regular basis, albeit in various forms.
- "Nigerian Prince" or Advance Fee Fraud: This scam typically involves an email from someone claiming to be a wealthy individual or a government representative seeking assistance in transferring funds. The victim is enticed to provide their personal information or financial details in exchange for a promised share of the money.

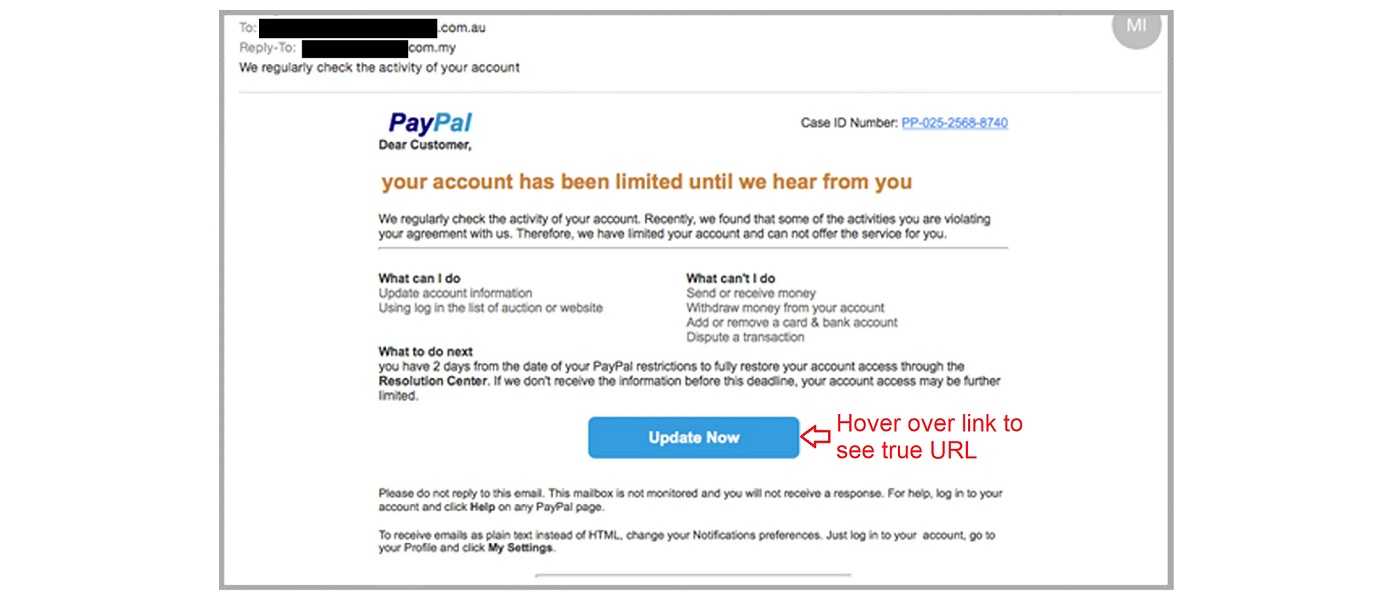
- PayPal or Financial Institution Impersonation: Scammers send emails impersonating well-known payment processors or banks, requesting users to update their account information or confirm suspicious transactions. Victims are directed to fraudulent websites that collect their login credentials and sensitive data.
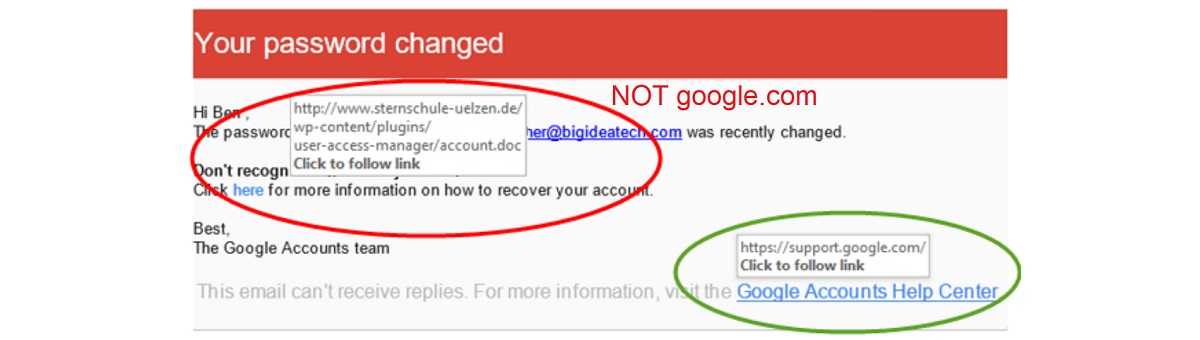
- Phishing Emails from Tech Companies: Cybercriminals send emails pretending to be from tech giants like Google or Microsoft, informing users of compromised accounts or the need to verify their information. These emails often contain links to fake login pages designed to harvest login credentials.
Never get in a rush. It’s never so urgent that you can’t take a bit of time to verify if it’s a real request. Actual urgent situations require a phone call to you or 911, not an email message. If it’s really that important, they won’t take time to wait on an email reply. Take the time you need to make sure you’re not getting snagged by a phishing hook.