Summer is nearly over, but cybercriminals don't really pay much attention to the seasons. The time of year, when the Cherry trees bloom, is also a great time for cybercriminals to pollinate Android devices with malware. But as we’ve recently found out, they don’t stop when summer begins. Their devious ploys continue year-round. Researchers at Trend Micro have recently found some malware called CherryBlos being distributed as the cryptocurrency mining application, SynthNet.
This tactic of stealing passwords to steal cryptocurrency and banking account information is old news. However, the way CherryBlos does it is creative, and as far as is known, it’s the first of its kind to do it this way. It uses optical character recognition (OCR) to scan images and steal passwords.
You might be wondering how it could get a password from an image on your smartphone. Well, as it turns out, even though it’s not recommended, there are some who take screenshots of their passwords and store them on their phones. Those are what this malware targets.
Trend Micro also found SynthNet running on money making scam apps in the Google Play store. Below are a couple examples:
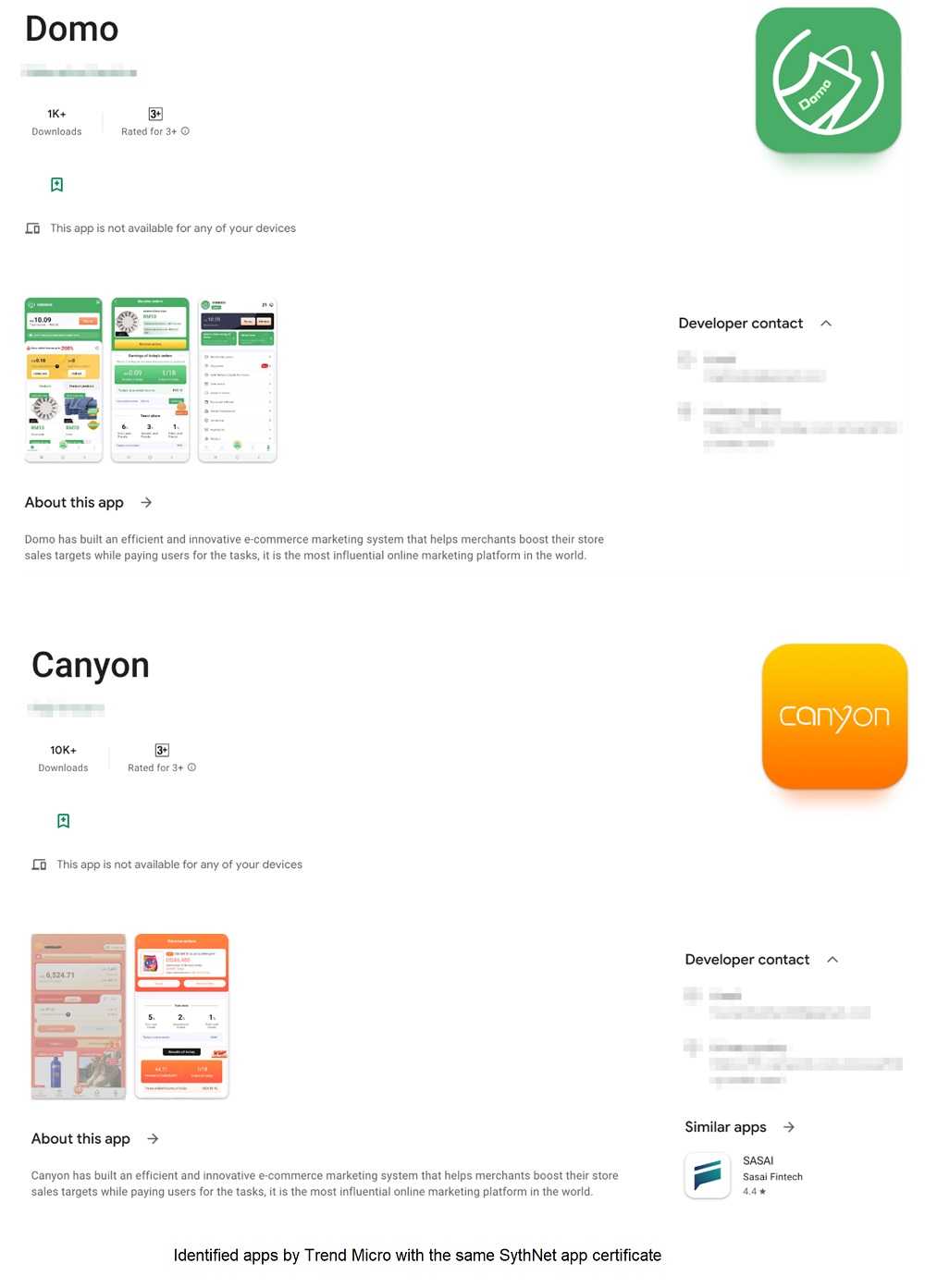
Of course, there is more to this. CherryBlos also uses fake overlays to imitate legitimate banking and crypto apps. The hackers install the malware in these to get access to usernames and passwords.
If OCR sounds familiar, it’s because it’s been around a while and is used in many PDF editors. It scans images and photos and pulls text from it so you don’t have to retype it all in order to edit it.
 Always keep a healthy dose of skepticism when downloading apps. Make sure you’re getting the right one. Use the official stores for your devices and do some research before hitting that “get” key. If the reviews are all stellar and there aren’t a lot of them, maybe wait a bit. If there is anything negative about an app, the early adopters will alert you in reviews.
Always keep a healthy dose of skepticism when downloading apps. Make sure you’re getting the right one. Use the official stores for your devices and do some research before hitting that “get” key. If the reviews are all stellar and there aren’t a lot of them, maybe wait a bit. If there is anything negative about an app, the early adopters will alert you in reviews.
The SynthNet app was previously available in the Play Store but was removed by Google before it went into full bloom. It was “only” downloaded a few thousand times before that; but remember…it only takes one time for a bad app to stink up your device.