It’s gotten rather stinky for Android users. Discovered and named by Trend Micro in June 2023, the MMRat trojan is a novel malware that is really making those devices smell ripe. It mainly takes advantage of a seldom-used communication method to steal data—particularly banking and financial data. And somehow, the victims are nose-blind and don’t smell a thing while it’s all happening.
Unfortunately, not a lot is known about this Remote Access Trojan (RAT). However, preliminary research by Trend Micro indicates that it is promoted via websites that mimic official app stores. The apps are mainly for dating and official government business.
Once the app is installed and compromises your device—which it does by abusing the little-used Accessibility Services—it monitors your activity and allows the hackers to collect the following information:
- The user inputs through key logs
- Screen, network, and battery information
- Contact lists
- Installed applications
- Live stream and camera data
- Real-time screen content
The functionality of MMRat malware relies on efficient data transfer. To achieve this, the MMRat authors have created a custom command and Control (C2) server Protobuf protocol to handle this. And that’s what this RAT uses. This custom protocol, as well as others, also makes it easy for hackers to evade detection by network security that looks for anomalies.
By monitoring the phone, hackers discover periods of idleness when they can conduct real-time bank fraud. Once it has completed its tasks, it can uninstall itself and delete evidence of malware compromise. And Bam! It just stole your cheese.
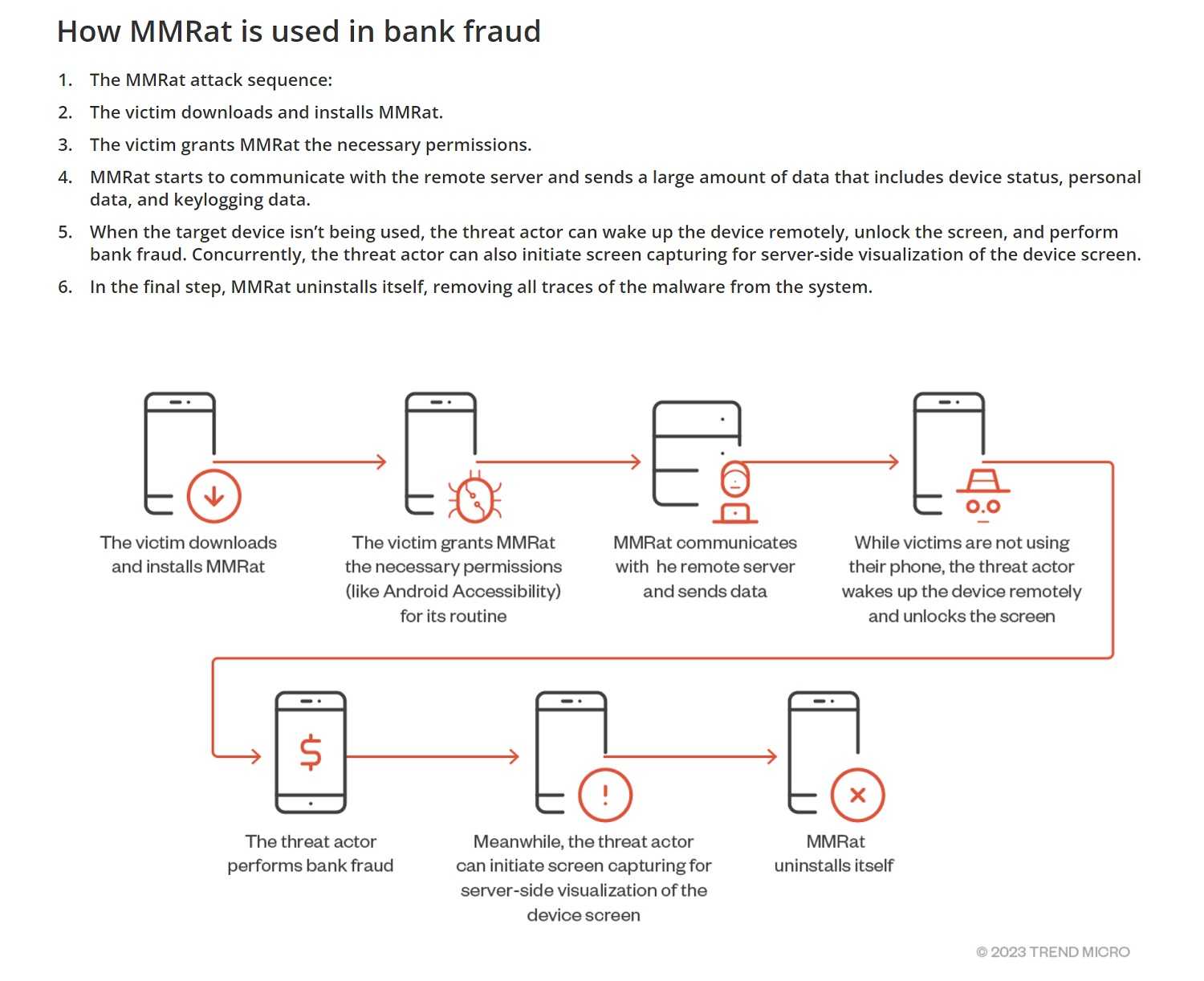
While this new Android trojan is mainly attacking consumers in Southeast Asia, it is bound to spread across the globe, considering how effective it seems to be at stealing banking data while remaining unnoticeable. With this in mind, you should take concerted effect to protect your private data from this and all other trojans.
 The best way to mitigate this is to avoid installing apps from unknown sources. Using a sideloading application or process can be convenient, but it is also risky as the apps are not rigorously tested and authenticated to be devoid of malware. Download applications from official stores such as the Samsung Galaxy Store, Amazon Appstore, and Google Play Store.
The best way to mitigate this is to avoid installing apps from unknown sources. Using a sideloading application or process can be convenient, but it is also risky as the apps are not rigorously tested and authenticated to be devoid of malware. Download applications from official stores such as the Samsung Galaxy Store, Amazon Appstore, and Google Play Store.
Make sure when you do download apps, you don’t give them more permissions than they need. It’s a very rare event that an app needs access to the accessibility services and it’s even more rare that they need administrator rights. So, don’t grant them.
Additionally, you can and should use antivirus apps with a database of viruses that are continuously updated. Such a product will help protect your phone from MMRat and any divergent versions of the malware moving forward, as well as other types of malware that are scurrying around out there.