SIM swapping, also called SIM hijacking, is when sneaky hackers get control of your mobile phone account and simply transfer your service to their own device, including your phone number. Once they manage to do that, they can access all your phone data and important accounts. Essentially, consider that if you can access it from your phone, so can they.
 Verizon has recently been warning of an uptick in this type of cybercrime. A SIM card, short for Subscriber Identity Module card, is a small, removable smart card that is used in mobile devices such as smartphones, tablets, and some other devices that connect to the internet. It stores essential information related to the user's mobile network subscription.
Verizon has recently been warning of an uptick in this type of cybercrime. A SIM card, short for Subscriber Identity Module card, is a small, removable smart card that is used in mobile devices such as smartphones, tablets, and some other devices that connect to the internet. It stores essential information related to the user's mobile network subscription.
What About the Various Types of Attacks?
As far as these attacks go, there are a few ways they can happen.
Sometimes the attackers physically snatch your SIM card. This is the less likely to occur option. Other times they pretend to be you and call up your phone company to request a SIM swap. They can also pull off a SIM hijack after tricking you with a phishing scam or buying stolen account info from the dark web. Sometimes, they even go into the stores and pose as you to perform the swap, though this again is less likely to happen that the remote options.
Phishing is when those bad guys try to fool you into giving them your sensitive info. So, before they go for the SIM swap, they might already have control of your email account. That means they can intercept messages from your phone company and make their evil plan easier. Remember that so many multifactor authentication (MFA) methods use your mobile number to send you a special one-time code. So, that makes this type of attack even more dangerous for you and more lucrative for a cybercriminal.
Keeping Your Devices and Info Safe
To keep yourself safe from SIM swapping attacks and other scams, you need to protect your personal info and follow some smart security tips.
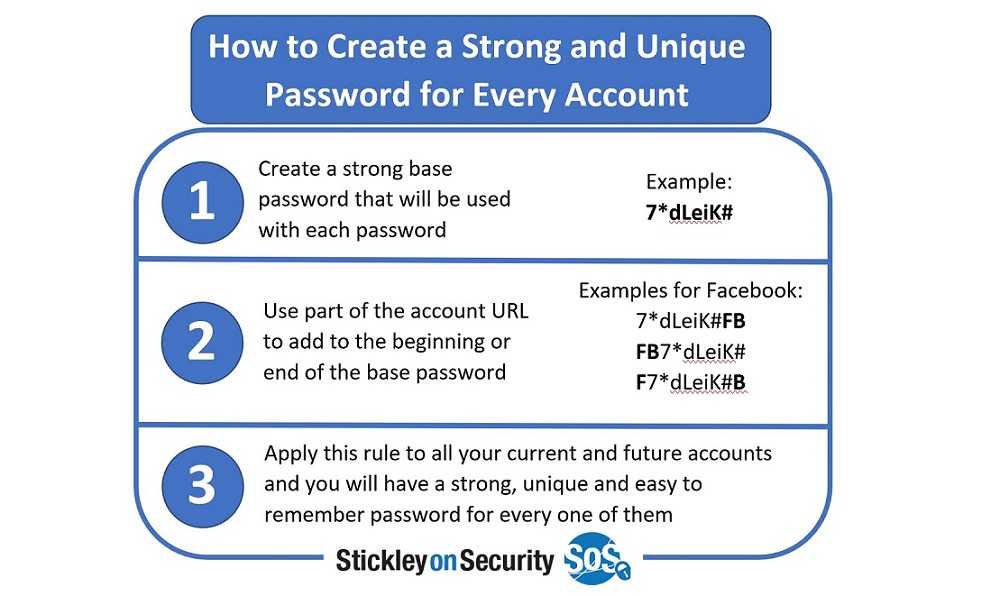 First, use strong and unique passwords. Don't be lazy and use the same password everywhere! If you can’t remember them, you can use clues to trigger your memory or even write them out with a pen and paper. Just tuck that away out of sight somewhere. If needed, you can use a password manager to keep track of them all. Keep in mind, though, that if someone manages to get their grubby paws on your master password, they will snag all of them…which won’t protect you no matter how random your passwords may be.
First, use strong and unique passwords. Don't be lazy and use the same password everywhere! If you can’t remember them, you can use clues to trigger your memory or even write them out with a pen and paper. Just tuck that away out of sight somewhere. If needed, you can use a password manager to keep track of them all. Keep in mind, though, that if someone manages to get their grubby paws on your master password, they will snag all of them…which won’t protect you no matter how random your passwords may be.
Next, turn on MFA or two-factor authentication (2FA) whenever possible. It's like an extra layer of security that asks for more than just a password—like a text confirmation, for example. While this is not foolproof, it is another layer of protection that everyone can use when it comes to cybercrime.
Be super careful about unsolicited texts, emails, and calls, especially if they're pushy and asking for your personal details, or making you think something terrible will happen if you don’t give them up immediately.
Legit companies will never ask you for your passwords, PINs, Social Security numbers, or payment info through those channels. If you think someone's trying to take over your SIM, change your passwords for online banking and email accounts right away. And keep an eye on your email provider's security dashboard to spot any weird logins from unfamiliar devices or places. Facebook and Google offer a way to do this, but other services do as well. Check the settings in those applications.
Stay on top of things and take these precautions to lower the chances of falling victim to a SIM-swapping attack. Keep your personal info safe, and guard those accounts!