Ransomware's 4 Favorite Entry Options And How To Counter Them
February 17, 2024
The growing scourge of businesses worldwide, ransomware attacks are currently at historic levels. Always improving, always stealthier, ransomware is the number one malware threat that businesses need to protect themselves against. Ransomware is behind countless problems for businesses worldwide, including significant down-time, loss of reputation, and customers, and significant financial expense.
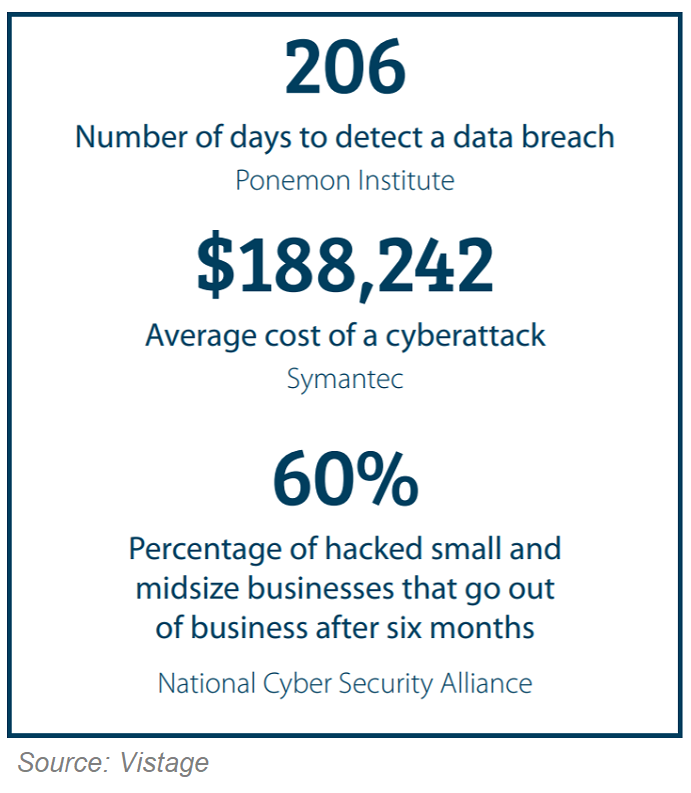
Studies show 41% of customers say they would stop buying from a business victim of ransomware. Attacks against small-to-medium sized businesses (SMBs) can be most catastrophic, with 65% closing their doors within six months of a ransomware attack. Knowing the four most prevalent ways ransomware launches attacks is something every organization leader and IT department should know, and that includes security tips to help avoid them.

46% RDP Compromise: Remote desktop protocol (RDP) is most common, bolstered by the current pandemic and the scores of employees now working from home. RDPs facilitate network connections between users, especially for those working remotely. Once an RDP is compromised, hackers are free to deploy ransomware attacks.
- Tip: Reduce access to RDP to only those who need it; use a VPN (virtual private network) as a protective layer for all network traffic.
26% Phishing Emails: Still going strong and always improving, phishing emails are like a mosquito you can’t get rid of. Always annoying, email phishing and spam emails are a hacker favorite for entering a data system. They draw you in by exploiting emotions of all types from scare tactics to great news! The ultimate goal of these emails is getting the recipient to open an attachment, download a file, or click on a link in the text.
 Tip: Don’t trust any email unless you are 100% positive you know and trust the sender is who they claim to be. Never open attachments, download files, or follow links from an untrusted source or that you are not expecting to receive. The files are sure to be malware-filled, including with ransomware, and the links often go to bogus websites designed to steal sensitive data.
Tip: Don’t trust any email unless you are 100% positive you know and trust the sender is who they claim to be. Never open attachments, download files, or follow links from an untrusted source or that you are not expecting to receive. The files are sure to be malware-filled, including with ransomware, and the links often go to bogus websites designed to steal sensitive data.
17% Vulnerability Exploits: These exploits take advantage of a software vulnerability or security flaw. They allow bad actors to remotely access a network through these weaknesses and gain elevated privileges allowing them to invade a network and launch an attack.
- Tip: Keep all systems and software patched and updated as soon as possible. They typically contain fixes for security and other software flaws. Limit access privileges to only those who need it for their work.
10% Account Takeovers: These attacks (ATOs) happen when a criminal gains access to a user’s account credentials, allowing them to login remotely as an employee, change settings, and launch attacks.
- Tip: Use 2FA (two-factor authentication) or MFA (multi-factor authentication) as additional security layers for logins. Use security questions and/or random codes and limit login attempts. Ongoing employee education can help stop any number of potential attacks as they are often the first line of defense against cybercrime.