Attackers Breach DropBox Sign Production Environment Accessing Login and Authentication Info
June 12, 2024
In April 2024, Dropbox reported a significant security breach involving its Dropbox Sign service, formerly known as HelloSign. The breach occurred on April 24, 2024, when a hacker accessed the production environment of Dropbox Sign through a compromised service account. This account, used for automated system configurations, allowed the attacker to infiltrate the system and access sensitive customer information.
The compromised data included email addresses, usernames, phone numbers, hashed passwords, account settings, and authentication information such as API keys and OAuth tokens. Importantly, while user data was accessed, there is no evidence that the contents of users' documents or their payment information were exposed. According to Malwarebytes, this breach was limited to the Dropbox Sign infrastructure, leaving other Dropbox services unaffected. However, even if users have never created a Dropbox Sign account, but received or signed a document through Dropbox Sign, those email addresses and names were exposed.
In response to the breach, Dropbox has taken several security measures. The company has reset all users' passwords, logged out all connected devices, and initiated the rotation of all API keys and OAuth tokens. For users with API access, Dropbox has required the generation of new API keys and temporarily restricted some functionalities. Additionally, the organization has hired forensic investigators to continue the investigation. They have reported the incident to law enforcement and regulatory bodies to comply with data protection regulations.
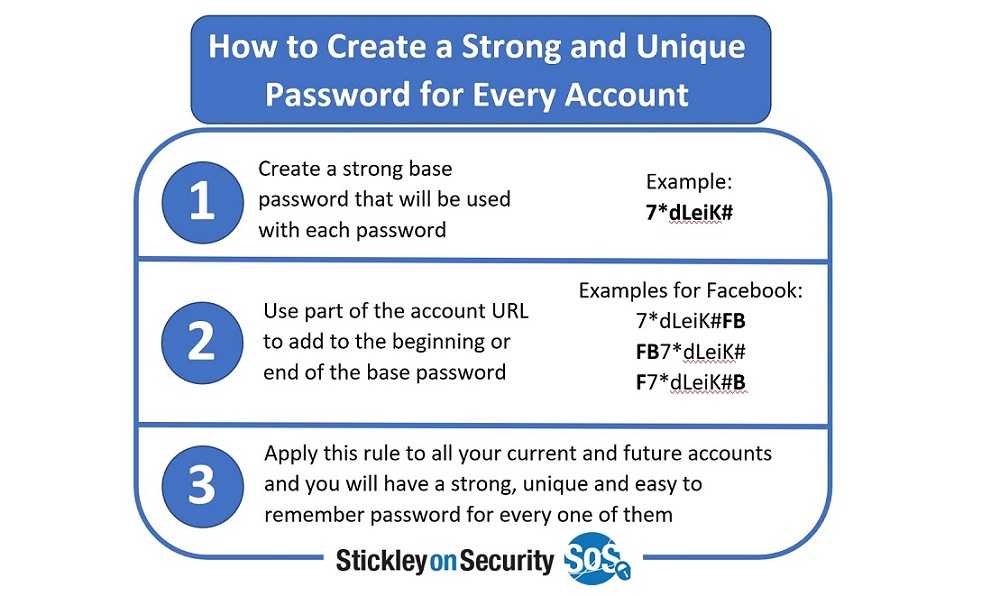
Dropbox is also in the process of notifying all affected users. Should you receive a notification that your information was accessed, be sure to reset your password using at least eight characters including a good mix of letters, numbers, and special characters. In addition, enable multifactor authentication if it’s available to you.