The time has come. Technology has finally appeared that all but eliminates the need to remember a whole bunch of different passwords. No more hint lists. No more trying to come up with yet another one for each site you use. All of that has finally become unnecessary, mostly. Now, you can use some other way to log in. Whew!
You’ve probably seen something on websites you log into that give you an option as to how you want to log in. Maybe it asks if you want to use a security key, your face ID, or a keychain. What you choose depends largely on your preference, your device, or on how you are logging in. For example, if you don't have face or fingerprint authentication on the device, well, you obviously can't choose that. The password and MFA combination is still a great way to do it, however, but you have options.

Passkeys: These take us one step further than traditional passwords. They use two-factor authentication and biometric verification. This is usually a login ID and a biometric ID, such as Face ID or fingerprint, to secure accounts. No one has your face or fingerprint, so this is a great option.
One-time passwords: The website will send you a one-time, unique password via text or email (for example). Once you use it, it won’t work again.
Hardware keys: These are tiny “keys” that you can plug into your computer or mobile device to authenticate to your accounts. They are compatible with USB-A, USB-C, Bluetooth, and NFC connections and are lightweight and very small. You can use them with many accounts such as Facebook, Gmail, Yahoo Mail, Dropbox, Amazon, and SalesForce, to name a few.
However, if you do use passwords, there are few ways to make it easier on yourself:
Use a password manager. While not foolproof, they can prevent the need to remember 100 passwords. Just keep in mind that if the password manager website is breached, so are your passwords. If they get your master password, they have all of your passwords and therefore ALL of them will need to be changed. Using a password manager that stores passwords on your device is far more preferable to a service that saves them in a cloud that could be breached.
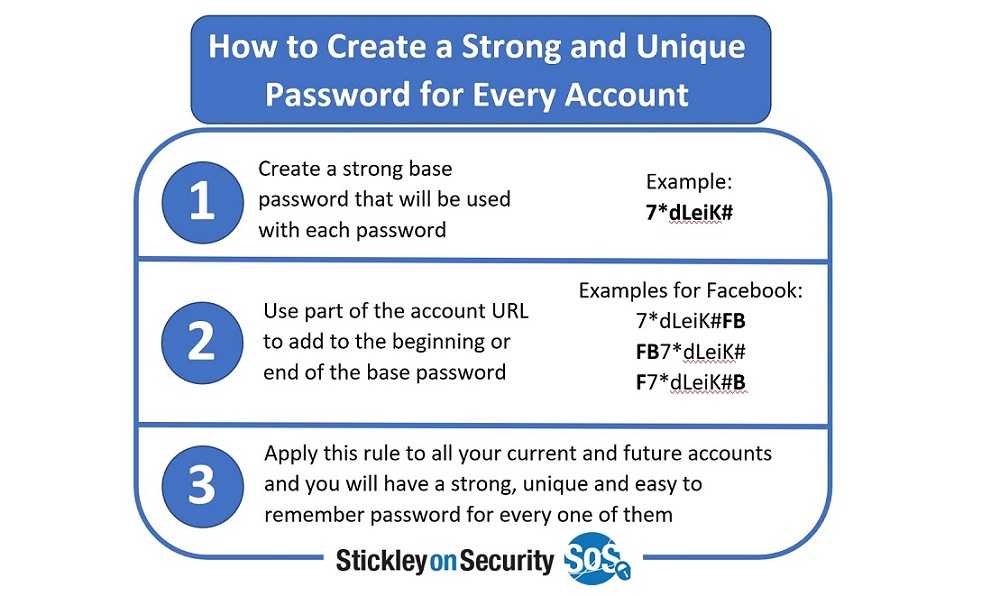
Use a base password and modify it slightly for each website. Think of a password or phrase of at least eight characters and use letters from the website to complete it. For example, if you’re going to Amazon.com, you could have a base as “Ryt1#” and add the first two letters to make a unique one. So, your password for that site is “Ryt1#Am.”
Make a clue. If you need to write them down, use it as a last resort and don’t write down the whole password. Give yourself a clue to trigger your memory. It’s best to write it on paper and lock it away. If it’s on your device and that is compromised or stolen, so is your password list.
Whatever you do, don’t make your password “123456” or “football.” Those are widely used along with other common ones. The hackers have your number if you use those. You can bet on it.