SIM Swap Attack Transfers Mobile Numbers To Cyber Thieves
September 17, 2023
We haven’t talked about supply chain breaches much lately, but that doesn’t mean they don’t happen anymore. In fact, there was a recent such breach at Kroll, a firm specializing in risk and financial advisory services. This one had far-reaching consequences, affecting downstream customers and exposing the personal information of numerous claimants. These claimants were involved in bankruptcy proceedings linked to cryptocurrency trading firms like FTX, BlockFI, and Genesis. This incident serves as a poignant reminder of the persistent threat that organizations face from SIM-swapping attacks, because that’s what happened in this case.
A SIM swap, short for Subscriber Identity Module swap, is a technique used by cybercriminals to take control of a victim's mobile phone number. This scam has gained notoriety in recent years due to the ability of the criminals to not only steal your phone number but steal so many other things too, such as your bank account contents.
Here's how a SIM swap generally works:
- The Reconnaissance Phase: The attacker first collects information about a victim. This might include their name, phone number, and other personal details. They often obtain this information through social engineering, data breaches, or phishing attacks. Sometimes they just purchase it from someone on the dark web.
- The Impersonation: Armed with the victim's details, the attacker contacts the customer support line for the victim’s mobile carrier, impersonating the victim. They claim their phone has been lost or stolen and request a new SIM card with the victim's phone number.
- The Verification: The mobile carrier's customer support typically asks for some form of verification. But the criminals have that too. Attackers might provide stolen personal information or use social engineering techniques to convince the carrier's representative to proceed with the SIM swap.
- Time to Activate: Once the attacker receives the new SIM card, they insert it into a device they control. This effectively transfers the victim's phone number to the attacker's device, disconnecting the victim's phone.
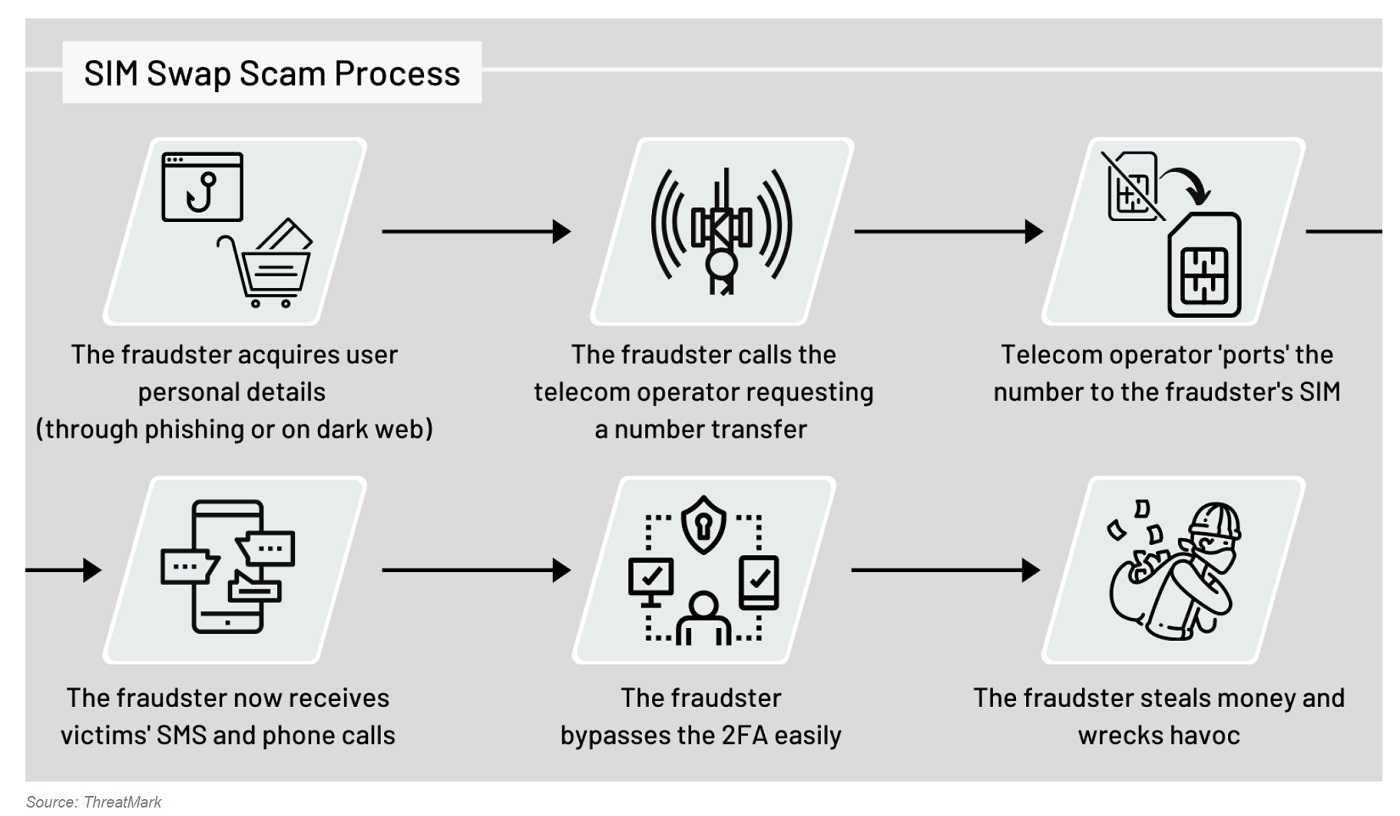
Once the criminal has control over the victim’s phone number, they can intercept text messages and phone calls, including two-factor authentication (2FA) codes sent via SMS. They can also impersonate the victim to gain access to email accounts, bank accounts, cryptocurrency wallets, and other sensitive information. Often, the first act they perform is to change the login information to the mobile account. Then they proceed to change passwords on other accounts so they can conduct financial transactions and/or lock the victim out of their own accounts.
 To protect against SIM swap attacks, individuals should secure their personal information. While 2FA or MFA should always be used when made available, text and email codes are not always the most secure option. It’s better to use alternative 2FA methods such as authenticator apps or hardware key fobs if given the choice. And as always, be cautious about sharing personal details over the phone or online.
To protect against SIM swap attacks, individuals should secure their personal information. While 2FA or MFA should always be used when made available, text and email codes are not always the most secure option. It’s better to use alternative 2FA methods such as authenticator apps or hardware key fobs if given the choice. And as always, be cautious about sharing personal details over the phone or online.
The security breach at Kroll unfolded when an assailant orchestrated the SIM swap of an employee's phone number to a device under their control. Subsequently, they leveraged this access to obtain sensitive data that allowed them to perform the swap and access the bankruptcy details related to the three crypto companies. They also managed to access email addresses, names, and balances of their accounts. All of this information can be used in targeted phishing attacks.