Job Emails Offer Job Seekers New Malware
April 1, 2025
Even though the unemployment rate isn’t so bad right now, there are still those who can’t resist taking advantage of job seekers. There’s a sneaky scam that's been making the rounds lately—fake job interview emails designed to install cryptocurrency mining malware on your devices. Both Windows and MacOS users are in danger of this one. Cybercriminals are posing as recruiters to lure unsuspecting job seekers into their trap. But they get something less desired than a job offer from these so-called recruiters.
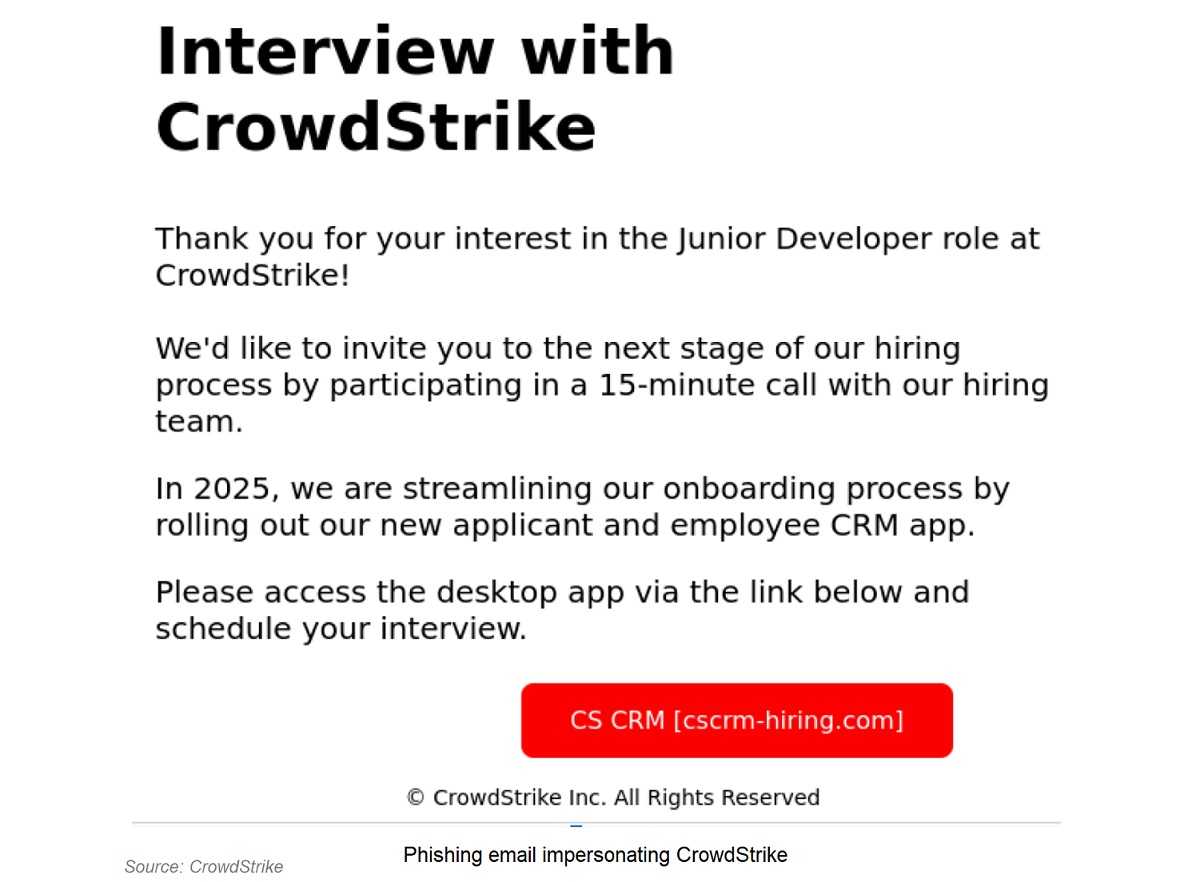
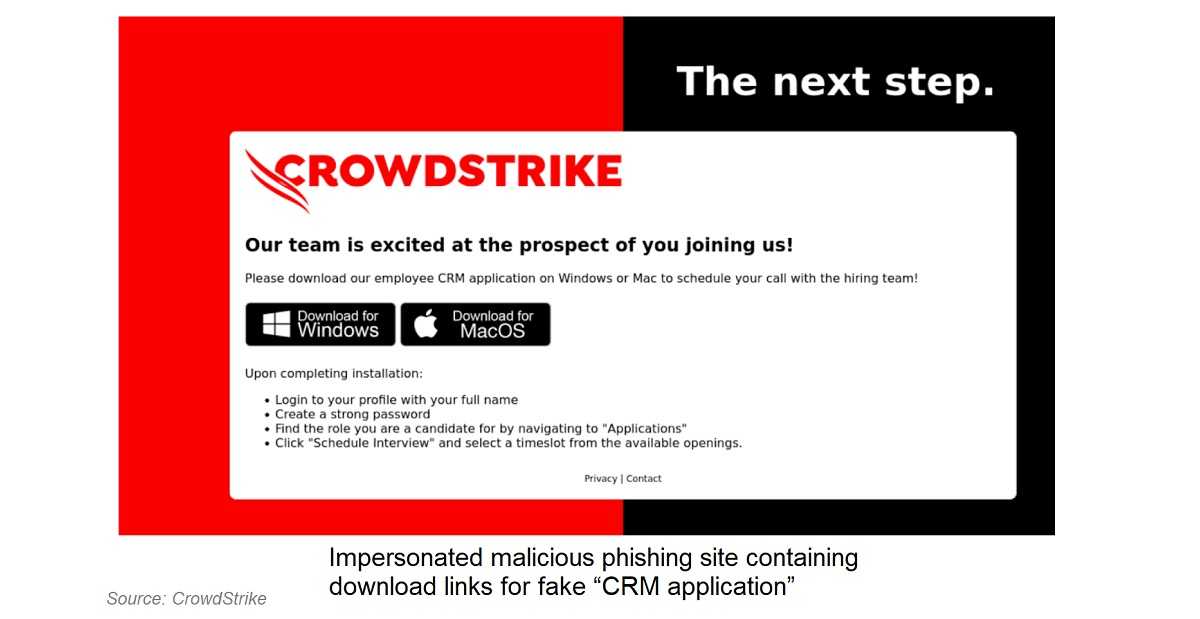
Here's how it works: You receive an email inviting you to schedule an interview. The email includes a link that supposedly leads to an application or scheduling site, often pretending to be from the company CrowdStrike. However, clicking on this link redirects you to a malicious website offering a download for a "CRM application,” which is the Customer Relationship Management software many organizations use. Once downloaded, this application installs the XMRig cryptominer onto your system. This malware hijacks your computer's resources—like the CPU and GPU—to mine cryptocurrency, significantly slowing down your device's performance.
What's particularly concerning is the level of sophistication in these attacks. The malicious executables perform various environmental checks to avoid detection. They scan running processes and check CPU usage to ensure they can operate stealthily. If your device passes these checks, the malware displays a fake error message while downloading additional payloads behind the scenes needed to run the cryptominer. You’ll probably just think your connection is slow.
To protect yourself, always verify the authenticity of unsolicited job offers, especially if you’re not actively seeking new opportunities. Be cautious with links and attachments in emails, especially from unknown sources or any that you aren’t expecting to get. Keep your security software up to date and regularly monitor your system for unusual activity.
Even though these attackers may not be initially after your account credentials, it doesn’t mean they aren’t doing damage or opening avenues for others to grab those. Remember, if something seems too good to be true—like an unexpected job landing in your email—it probably is.