Popular eSignature Service Customer Email Database Stolen and Used in Phishing Campaign
By: Jim Stickley and Tina Davis
May 19, 2017
A popular eSignature service has been tracking a breach, but just made it official after a week. After seeing a significant spike in email messages going out to its customers, DocuSign performed an investigative analysis and determined that someone broke into its system and stole a list of customer email addresses. They subsequently used those in a phishing campaign. Inside each message sent as part of this is a Word document that will release malware if it’s opened.
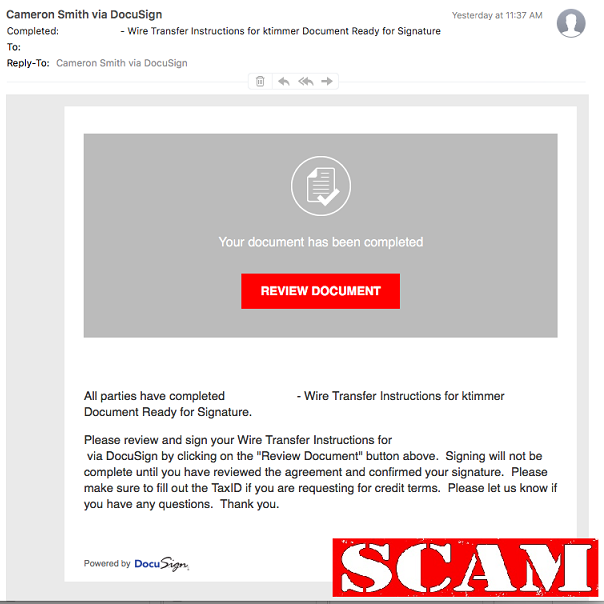
The emails spoof the DocuSign brand and have a few different subjects. Those include “Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature” and “Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature.” The company is advising anyone who may receive a message with either of those subjects to just delete them right away, as they are not from DocuSign.
 Those who use phishing to lure victims are becoming better at their craft. It’s more difficult to determine if an email is indeed a phishing scam or if they are legitimate. Look out for a few clues:
Those who use phishing to lure victims are becoming better at their craft. It’s more difficult to determine if an email is indeed a phishing scam or if they are legitimate. Look out for a few clues:
1. If you don’t know the sender, be suspicious.
2. Even if you do know the sender, but are not expecting links or attachments from them and there is no personalized explanation of what’s inside, be very suspicious.
3. If the sender is a business with which you have no current activity, it could be phishing.
4. If you do click a link or attachment and are requested to enter sensitive information, second-guess it.
If you already have opened or clicked on something in email and it did some damage or you entered sensitive information such as a payment card number or your social security number, be sure to follow up by diligently checking payment card charges and your credit report. If anything is suspicious follow up and get it resolved right away.
This is not the first time DocuSign has been used in a phishing scam. Another one went around in 2016 using the company’s name and branding.
DocuSign has contacted law enforcement and is keeping its security website, DocuSign Trust Center, updated with new information as it comes forth. As of May 15, 2017, it appears that only email addresses were stolen through a “non-core” system that the company used for service-related communication. At this time, the company believes that no other details were compromised.