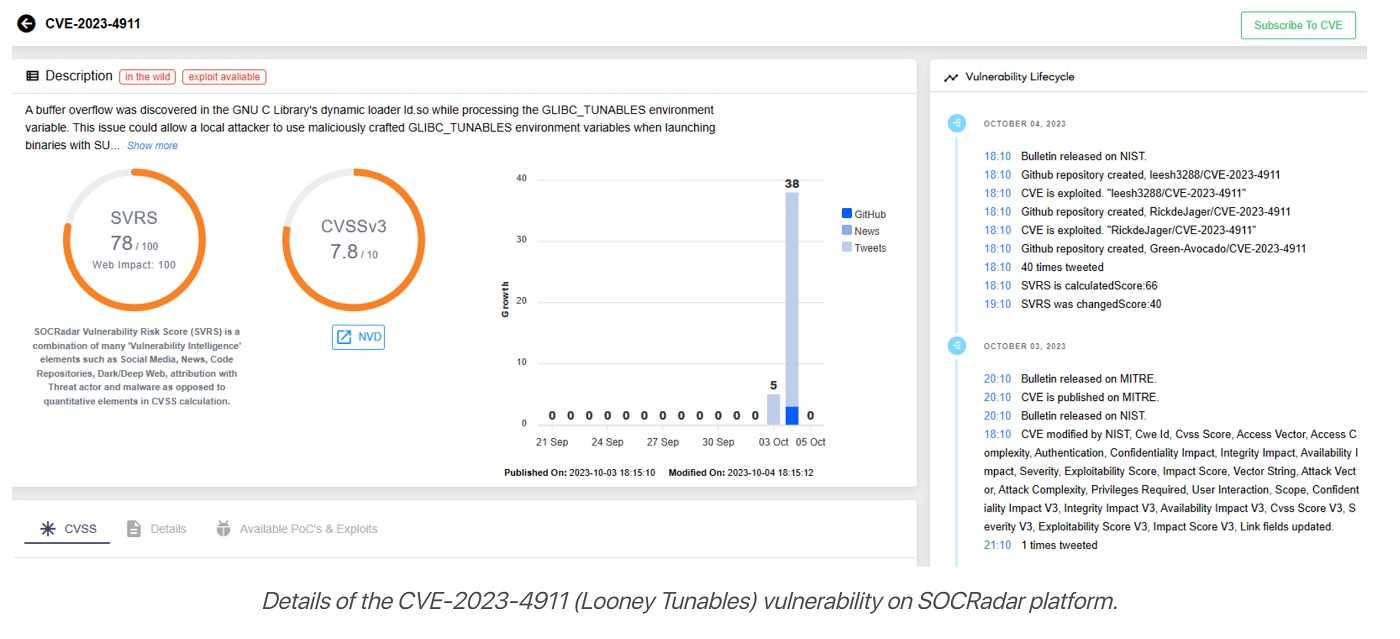
There’s a comical name for a serious Linux OS security vulnerability called Looney Tunables. This latest vulnerability exploit leads to elevated privileges, a dangerous outcome. Like other operating systems, a Linux OS directly manages software, memory, storage, hardware, and other critical functions. So, when a vulnerability exploit like Looney Tunables targets the largest open-sourced OS in the world, it’s time for a closer look.
Looney Tunables executes using a backdoor vulnerability (CVE-2023-4911) allowing it to sidestep authentication procedures and enter a system. It creates a point of access for the attacker, in this case, the cloud threat group known as Money Libra. The group, also called Kinsing, is known for cryptojacking attacks via the cloud and using their Kinsing malware.
Looney Tunables = Privilege Escalation
In general, privilege escalation attacks like that of Looney Tunables involve exploiting a system weakness to get unauthorized privileges, in this case for Linux operating systems. Escalation allows access within systems, networks, and software. Several major Linux system distributions vulnerable to Looney Tunables escalated privileges include Red Hat, Gentoo, Ubuntu, and Debian.
In particular, Looney Tunables privilege escalation allows attackers like this group to leverage the vulnerability and gain root access privileges, the highest privilege on an operating system. Root privileges allow administrative control and unrestricted permissions to change OS settings.
Kinsing’s Deviant Deviation
Tracking by Aqua Security shows Kinsing exploited the Looney Tunables vulnerability using a different method of attack from their “business as usual.” Using a publicly available PoC (proof of concept) exploit to show software weakness information, they leveraged Looney Tunables for system root access. Downloading other scripts for backdoor access to the server, they gained credentials having to do with the Cloud Service Provider, or CSP.
According to Aqua Security, putting their focus on information gathering is a first for Kinsing threat group, who typically focus on spreading malware to run a cryptominer. This change, according to Aqua Security, could mean Kinsing could be “planning to do more varied and intense activities soon” and those activities could mean “…a bigger risk for systems and services that run on the cloud.”
To help avoid an exploit like Looney Tunables and others, always keep system software updated and patched as soon as they’re available. Be on the lookout because one of those updates will be a fix for the totally “unamusing” Looney Tunables.