In recent weeks, a new phishing scam emerged targeting Apple users, dubbed the "Apple ID suspended" scam. This latest scam employs a deceptive tactic to trick users into providing sensitive information, such as their valuable Apple login credentials and other personal details. For this one, it creates a sense of urgency and fear if the user doesn’t take action; a hallmark for these types of threats.
How the scam works
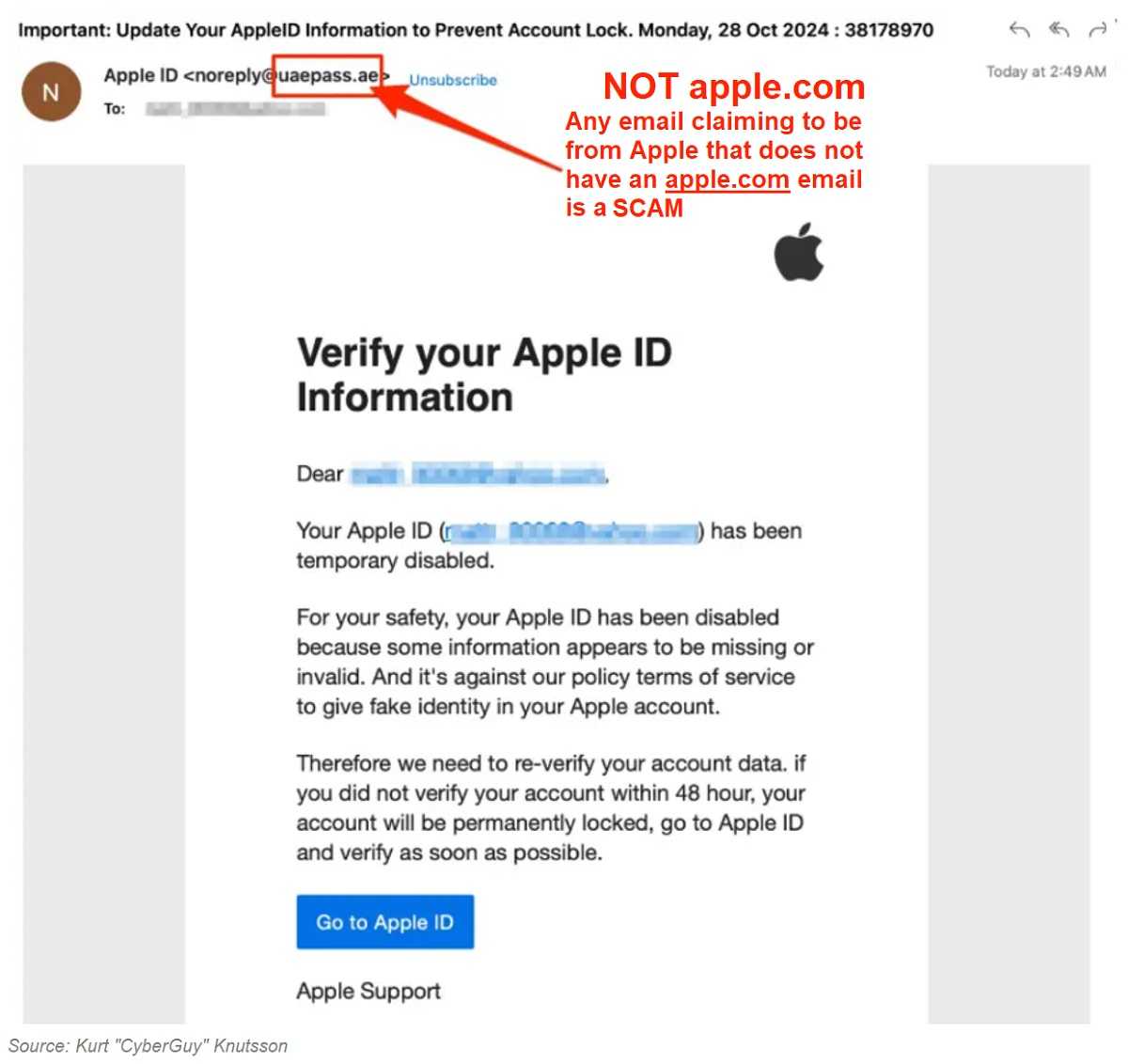
The tactics of this aren’t new to us. It typically manifests as an email that appears to be from Apple Support. It falsely claims that your Apple ID has been suspended due to "unusual activity" or outdated information.
The email often comes with an official-looking logo and professional wording designed to make you believe it’s legitimate. Typical for phishing. It also includes a blue button labeled “Go to Apple ID,” urging you to click it to verify your identity or reactivate your Apple ID. If you don’t act quickly—according to the email—you risk losing access to your account entirely within 24 hours. The aim is usually to make you panic so that you will take action without much thought.
Tell-tell signs
Here’s how you can spot this scam for what it is:
It asks for personal information via Email or Text. Apple never asks for this. Apple is clear about its policies: They will never ask you to provide account details, passwords, or payment information via email or text.
It comes from suspicious-looking email addresses. Scam messages often come from suspicious-looking addresses that closely resemble Apple's official email. For example, they may omit or include a single letter, or replace the “L” with a number “1.”
It contains generic greetings. Many scam emails start with "Dear Customer" instead of addressing you by name.
There are spelling and grammar mistakes. This is a giveaway for phishing. Apple prides itself on professionalism. If you spot odd language or typos, it’s a red flag.
What to do if you receive this message
 If you receive an email claiming your Apple ID has been suspended, here are steps you should take to protect yourself:
If you receive an email claiming your Apple ID has been suspended, here are steps you should take to protect yourself:
Do Not Click Links. Avoid clicking any links in the email. Instead, hover over them to see the actual URL. If it doesn’t look like an official Apple website, do not click it. In fact, don’t click it at all. Go directly to Apple’s website to login.
Verify the Sender: Check the sender’s email address carefully. Legitimate emails from Apple will always come from an apple.com address.
Report the Email: If you suspect the email is a scam, forward it to Apple at reportphishing@apple.com. This helps Apple track and combat phishing attempts.
Change Your Password: If you have already clicked on a suspicious link and entered your information, change your Apple ID password immediately by going directly into your account from a trusted, preferably previously bookmarked link.
Enable Two-Factor Authentication (2FA): This adds an extra layer of security to your account. Even if a scammer obtains your password, they won’t be able to access your account without the second authentication step.
Stay Informed: Keep yourself updated on common scams and phishing tactics. Awareness is one of the best defenses against these types of attacks.