The Quick and Dirty on QR Codes
December 14, 2024
QR codes, those little square mazes, are everywhere nowadays. From accessing restaurant menus to entering sweepstakes and registering new products, they’ve become a staple in modern convenience. However, like any technology, cybercriminals have found ways to exploit these codes, turning them into digital traps.
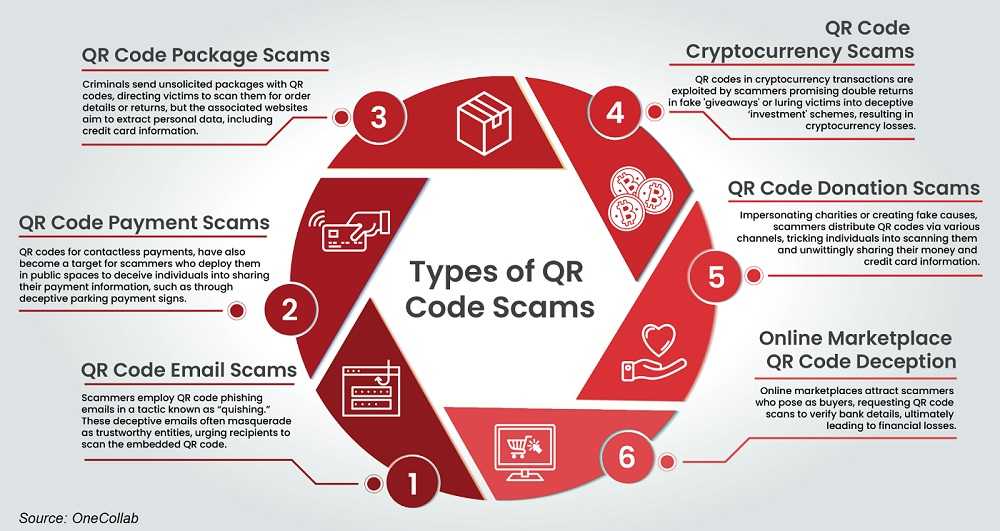
Here's how criminals might misuse QR codes:
- Overlaying Real Codes: Scammers might place fake QR codes over legitimate ones on parking meters, menus, magazines, or other public places.
- Phishing via Messages: They can send emails or text messages containing malicious QR codes, pretending to be from reputable businesses.
- Credential Theft: Scammers might use QR codes to trick you into giving up login credentials or confirming personal information due to supposed "suspicious activity."
- Embedded in Ads: QR codes can be embedded in ads on social media or elsewhere, leading unsuspecting users to malicious websites.
To protect yourself, follow these tips:
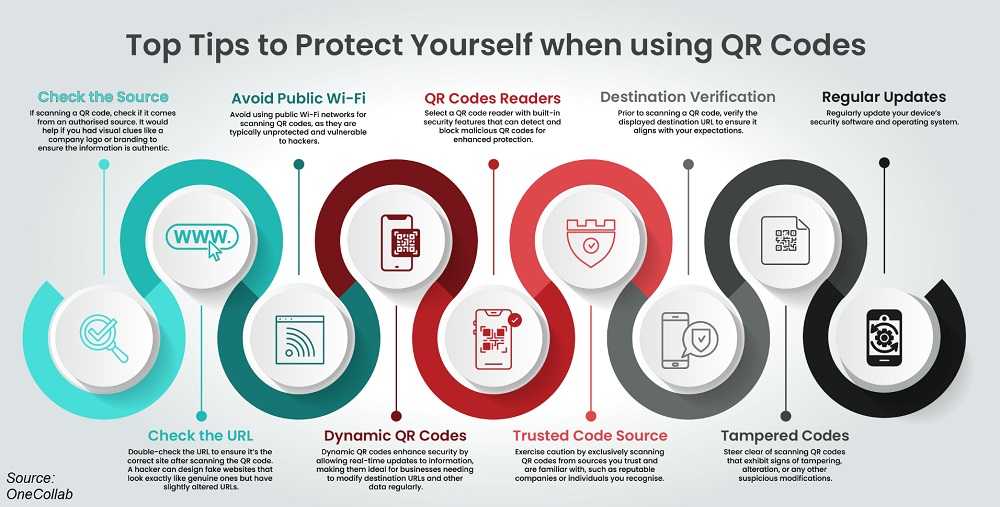
- Verify the Source: Treat QR codes like email links or attachments. Only scan codes from trusted sources. Even if a friend sends a QR code, confirm its legitimacy since their device or account might be compromised.
- Government Scams: Be skeptical of unsolicited QR codes claiming to be from government agencies. These institutions typically communicate via mail for official matters, not through QR codes.
- Check for Tampering: Examine public QR codes closely for signs of tampering. Fake QR codes might be slightly misaligned, oddly placed, or differ in size compared to the original.
- Scrutinize URLs: When a QR code directs you to a webpage, carefully check the URL for subtle misspellings or unusual characters, which are common in phishing attempts.
- Avoid Urgent Scams: If a QR code prompts urgent action, it’s likely a scam. Government agencies won’t demand immediate payments through QR codes; they send official notices by mail.
Using the camera on your mobile device to scan QR codes is generally safe, as it avoids the need for potentially risky third-party scanning apps. However, if you must download an app, ensure it’s from a reputable source like the official app store for your device.
Finally, stay vigilant by keeping your device's software updated and using reliable antivirus solutions. This helps protect against potential malware from malicious QR codes.
By following these precautions, you can safely navigate the world of QR codes without falling prey to cybercriminals.