Mac users are in the crosshairs again. Recently, a new campaign distributing malware targeting them via malicious Google ads for the Arc browser was observed and reported by Malwarebytes. This is the second such instance in recent months, highlighting Arc's growing use in the Mac world. Cybercriminals are riding the Arc popularity wave and pointing their cyber-trident right at MacOS users.
It isn’t the first time this method has been used to distribute a Windows RAT. This latest campaign involves a macOS stealer, branded as "Poseidon," actively developed as a competitor to Atomic Stealer (AMOS). It shares much of its code with its predecessor, formerly tracked as OSX.RodStealer by Malwarebytes, which was cleverly named after its author, Rodrigo4.
The Poseidon malware isn’t the same old malware. It goes further and adds new features such as looting VPN configurations. It is distributed via malvertising. You’ve heard of this before, most likely. It’s when malware is inserted into those advertisements you see in your browsers or in email banners. And the ads can even be legitimate business that were hijacked by the malware.
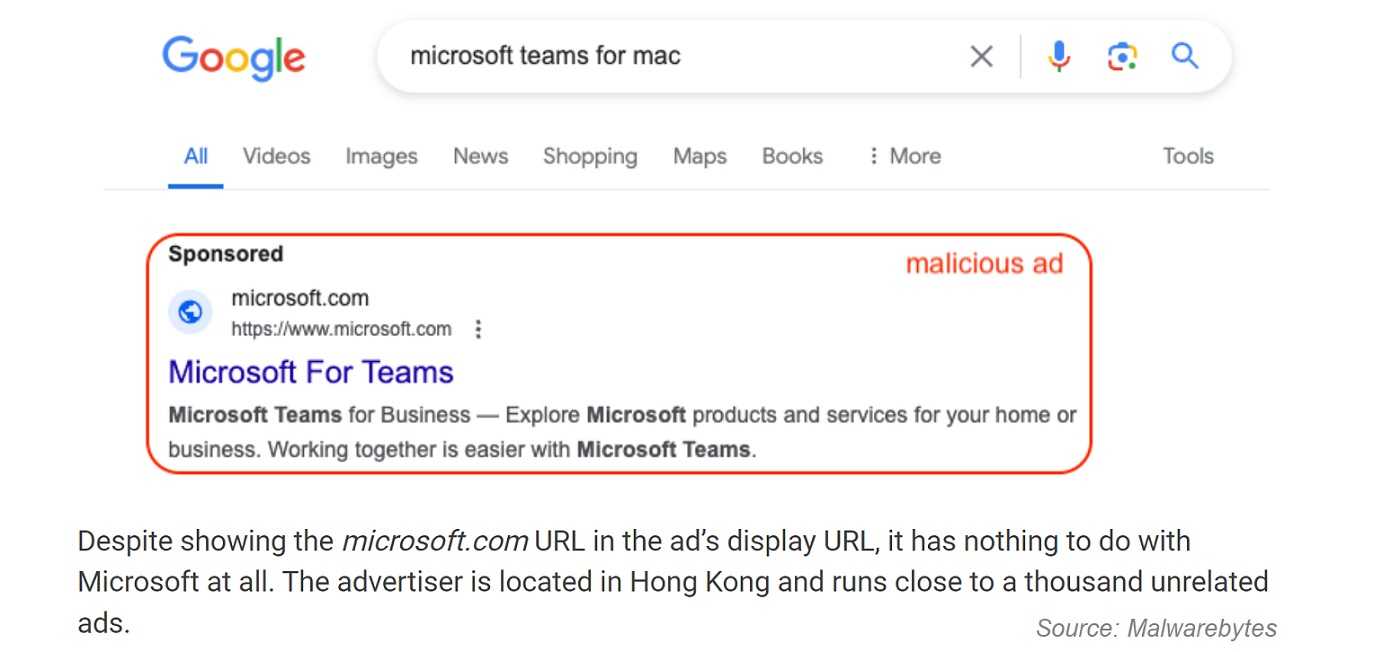
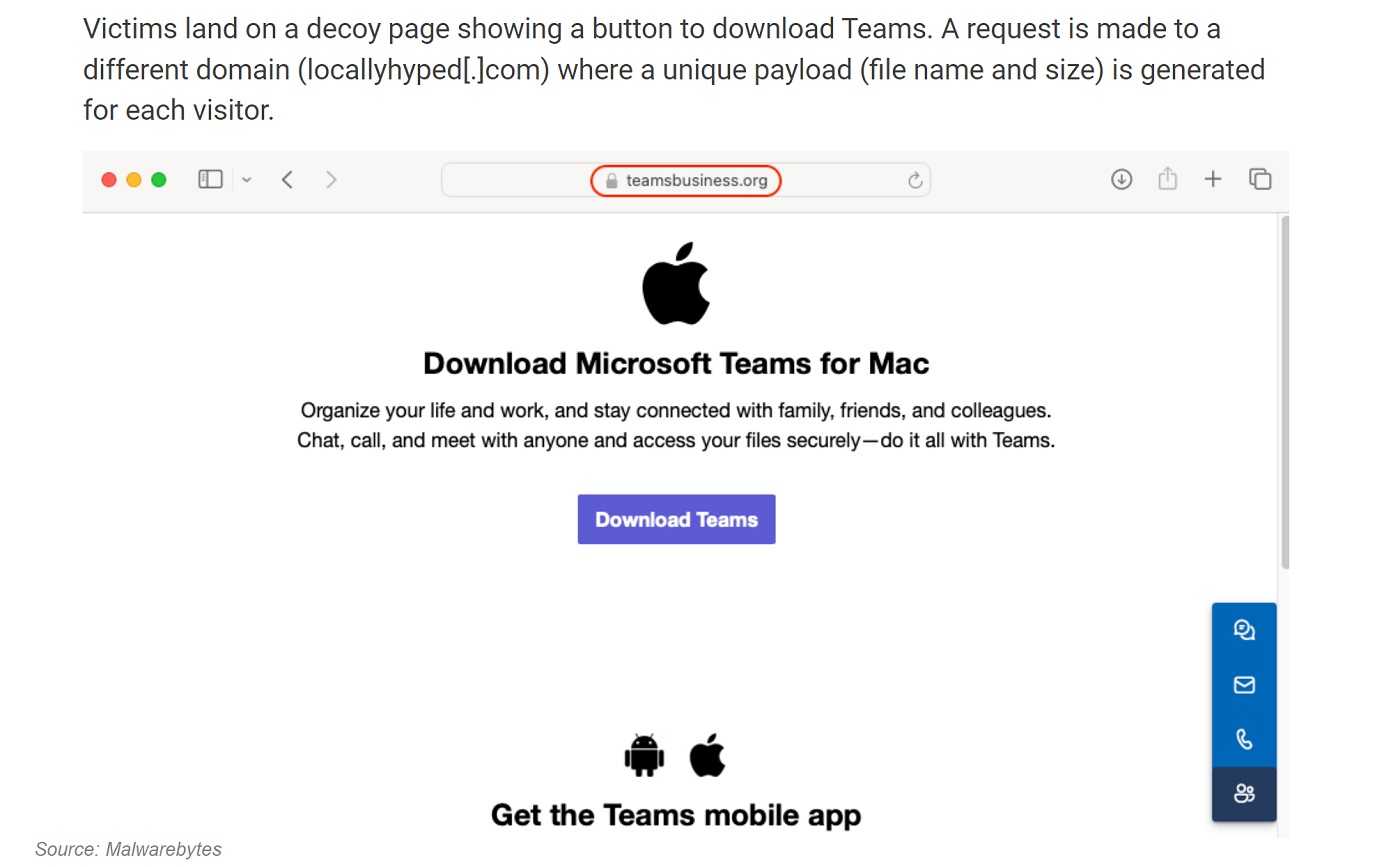
How can real businesses let their ads become compromised, you ask? Well, the advertisers don’t have control over the ads once they place them with the distributor, such as Google Ads. They are typically randomly placed, so even Google doesn’t know it’s happening until they are reported.
If you want to take a look at something you see in an ad, avoid clicking the ad, no matter how clever or flashy it is. Instead, go to the company’s website by typing it into the address bar of your browser and search for the product that way. If it is reasonable, consider using ad blocking software. Then you won’t be tempted to click on them in the first place. As always, make sure you have anti-malware software installed and it’s kept updated.
This campaign advertises Poseidon on cybercrime forums. Rodrigo4 is active on the XSS underground forum and offers a service that goes the extra customer service mile. It includes a malware panel with statistics and a builder allowing customization of the malware's name, icon, and AppleScript. Poseidon's functionalities are vast and include:
- a file grabber
- a browser data collector
- a password manager stealer
- a crypto wallet extractor
This campaign underscores the importance of vigilance against malvertising and the need for robust cybersecurity measures to protect against evolving threats, even for macOS users.