Passkeys Make Passwords a Thing of the Past
December 23, 2025
Tired of creating and remembering passwords? Well, now there’s an easier option to do away with all those pesky passwords. They’re called “passkeys”, and the best part is, they’re easier to use and more secure (you can now jump for joy).
What Is A Passkey?
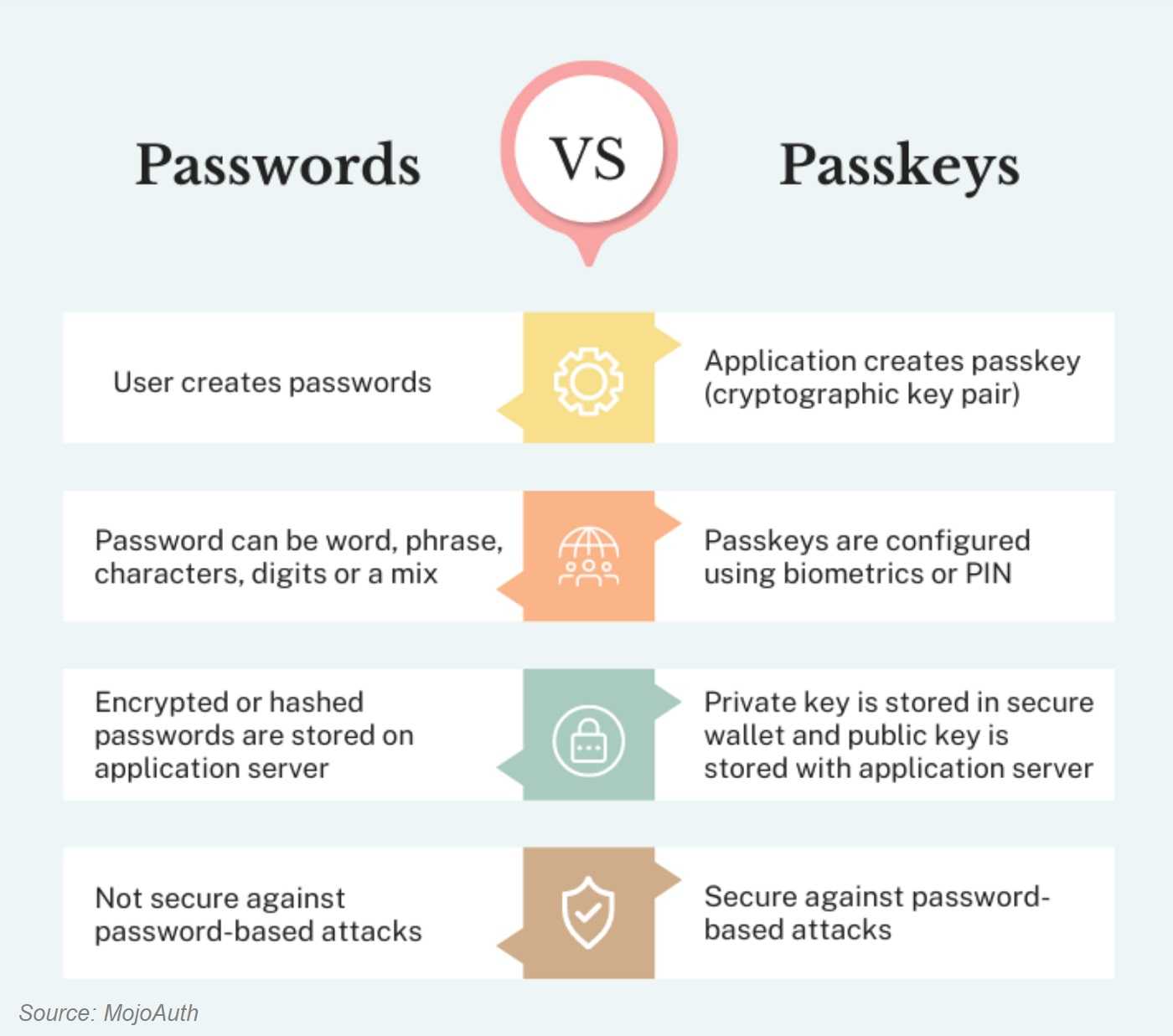
Passkeys are a type of authentication technology doing away with the risks of traditional logins. Using a passkey means no more logging-in with a password or username. It’s a kind of digital handshake between two forms of identity authentication.
The first authentication key uses your “biometric password” like facial or fingerprint recognition, called your “private key.” The second step uses a “public key” generated and stored by the website you’re logging onto. The private and public keys combine to create your passkey, assuring you are really you. The two keys “shake hands” to create a secure login.
Passkey Benefits
The following points to the ease and security of using passkeys.
- Passkeys are convenient, with most systems syncing keys across all of your devices. No more guessing where your password is stored, using the same from phone to laptop.
- Passkeys are site-specific. Hackers can’t trick you into using your passkey on a fraudulent website.
- In a data breach, a hacker can’t steal the passkey to your account, keeping your data safer.
Not all websites use passkeys yet. You’ll still have to go the traditional password route, but more websites are signing up every day. However, cybercriminals love finding ways around password safeguards, and passkeys are not immune. Cookie hijacking is trending at the moment, so here’s what you need to know.
Cybercriminals use malware to hijack a user’s valid browser cookies and get past a passkey. Always choose for cookies to expire after a short time, or periodically delete them from your browser. It’s a small price to pay for using passkeys and the strong security they provide. So, say goodbye to passwords and hello to passkeys!