Microsoft Teams Users Targeted In Impersonation Sophisticated Fraud Scheme
December 7, 2025
Cybersecurity researchers at Check Point Research have uncovered multiple critical vulnerabilities in Microsoft Teams that allow hackers to impersonate executives, edit messages without detection, and manipulate notifications, putting millions of users at risk of financial fraud and data theft.
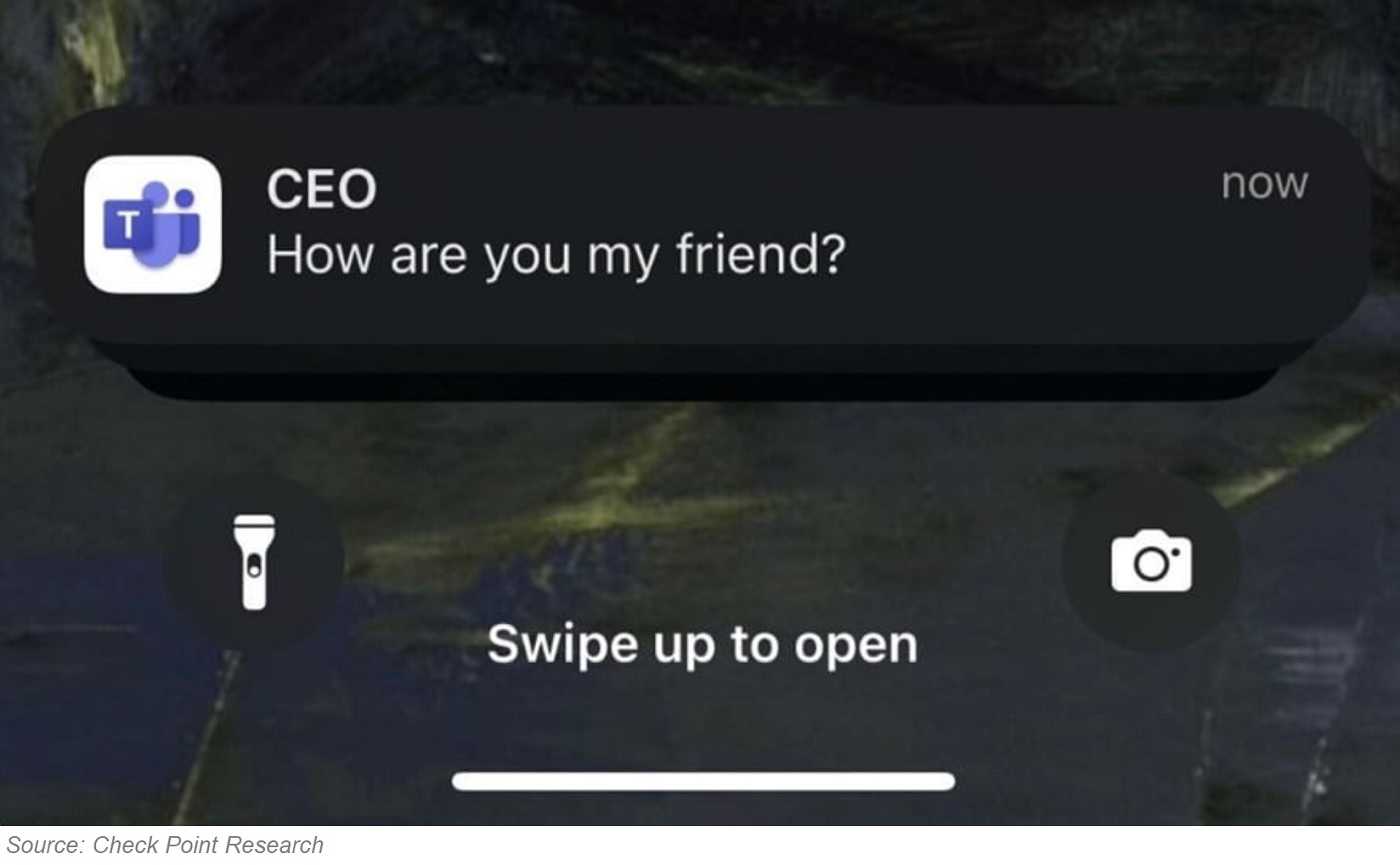
The flaws enable threat actors to change usernames, spoof notifications from trusted colleagues, and alter previously sent messages without triggering the “Edited” label. Attackers can send notifications appearing to originate from senior leaders like CEOs or finance directors, exploiting the trust employees place in authority figures.
How They’re Succeeding
The vulnerabilities work by allowing attackers to manipulate the platform’s messaging system through unique identifiers and API endpoints. Both mobile and desktop notifications can be manipulated, and display names in private chats can be changed through conversation topic modifications. Even caller identities during video and audio calls can be forged. That’s a lot of “WOW!” factor
Protection Tips
Verify urgent requests through alternative and independent communication channels, especially those involving financial transactions or sensitive data. Be suspicious of unexpected messages from executives requesting immediate action or making you feel like you cannot verify it. Enable multi-factor authentication on all accounts. Watch for unusual message behavior or unfamiliar notification patterns. Report suspicious activity to your IT department immediately.
Microsoft labeled the issues as CVE-2024-38197 and has reportedly fixed these issues. However, users should remain vigilant and update their Teams applications promptly.