Can Using The Same Password Lead To A Stolen Car?
January 2, 2026
In an age where cybercrime is increasingly sophisticated, it’s no surprise that criminals are using open-source tools to automate the process of cracking online accounts. This is especially true when it comes to mass password cracking or credential stuffing. This dangerous trend has allowed cybercriminals to make a lot of money with very little time or effort. They can deploy bots designed for data scraping and executing credential stuffing attacks on various websites and mobile apps. Their secret weapon? Exploiting the widespread tendency of users to reuse credentials across multiple sites.
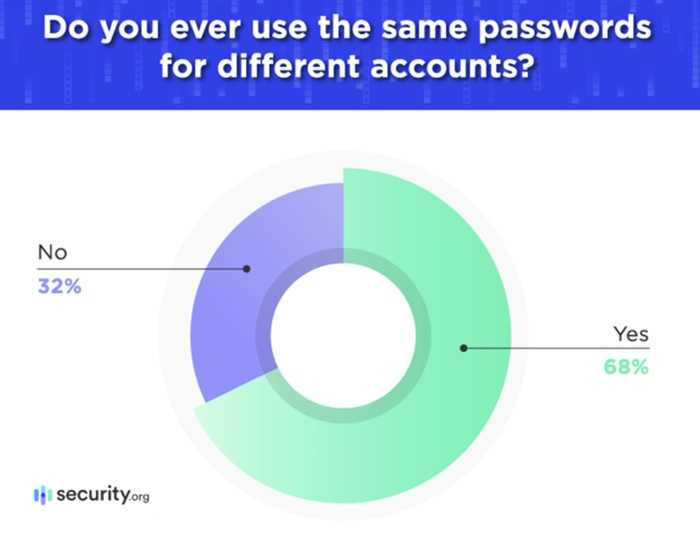
According to a 2025 survey by security.org, 68% of people still use the same password in multiple accounts. Recent attacks demonstrate why it shouldn’t be done. One in particular might surprise you.
Cybercriminals have begun shifting their focus to a rather unexpected target; one you may not think has any real risk – your vehicle information. Within one week, Kasada Threat Research found that there were 10,000 stolen auto accounts available on underground marketplaces; the next week they found an additional 5,000. These sold for a mere $2 each. Now, the question that naturally arises is: What could criminals possibly do with this vehicle information? Well, they can do a lot including:
- Clone your car
- Register your vehicle under their name
- Use information gained from the VIN to rob your residence
- Steal your identity
- Commit loan fraud
- Perform targeted phishing attacks against you
 As we know, any platform relying on user accounts and passwords is susceptible to these threats. To protect data from threats like this, consider the following:
As we know, any platform relying on user accounts and passwords is susceptible to these threats. To protect data from threats like this, consider the following:
- Use complex and unique passwords for each online account, no matter how unimportant you think the information in them may be.
- Keep an eye on your accounts for signs of ATOs and unusual login activity to identify compromised accounts early.
- Enable multi-factor authentication (MFA) to enhance security by making it significantly harder for attackers to gain unauthorized access. Remember to do this on your vehicle’s online accounts. There’s a lot of information in those.
- Always be on the lookout for phishing attacks. The more information someone has on you, the more specific they can be. If you’re not expecting a link, don’t click it.
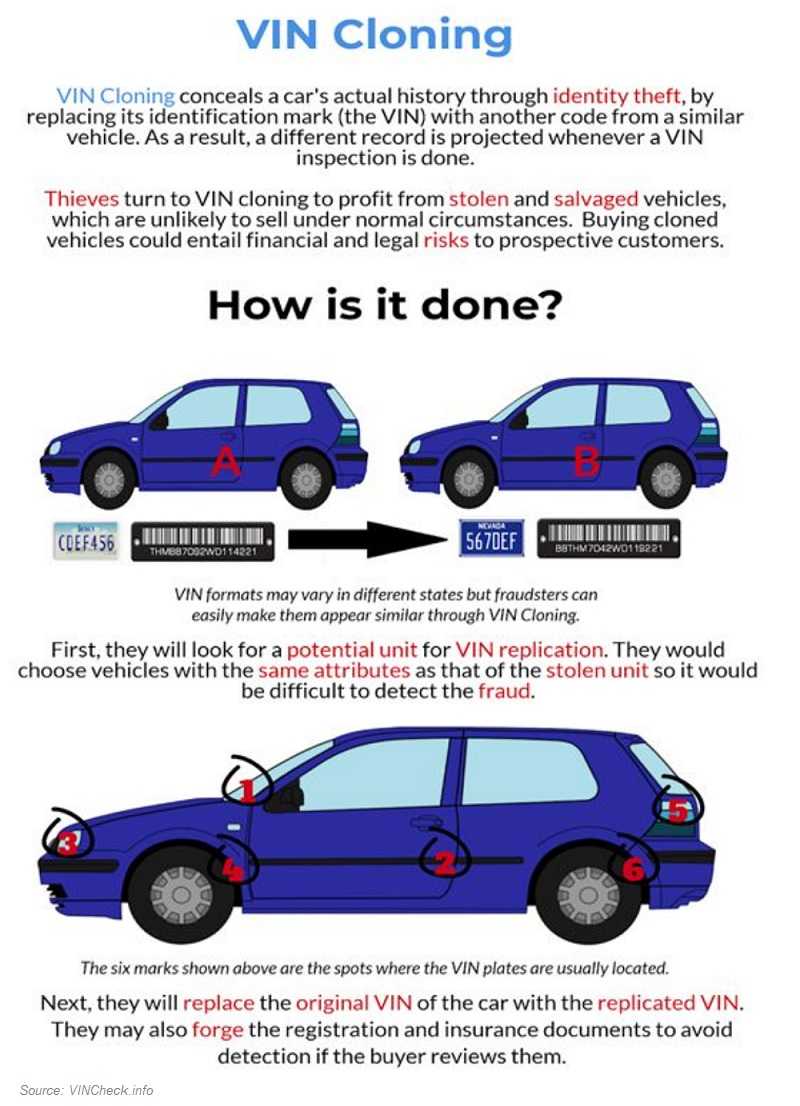
In 2017, a database was left open and unsecured for months. That database contained more than 10 million VIN numbers for vehicles from numerous manufacturers. There are numerous reports online about people who have been victims of VIN cloning. The FBI briefly outlined how it works.
- After stealing a car, thieves take off to a neighboring state. They find a large car dealership and look for a vehicle that’s the exact make, model, and color of the stolen one.
- They write down VIN stamped on the top of the dashboard and drive off.
- They make an exact replica of the new VIN tag and replace the legitimate one on the stolen vehicle.
- Finally, the thieves forge information to get a real title or other ownership documents from the DMV in the other state.
At this point, it’s not hard to sell the vehicle because it’s legally registered and not reported as stolen. And if you happen to buy one of them, it can be a big problem for you.