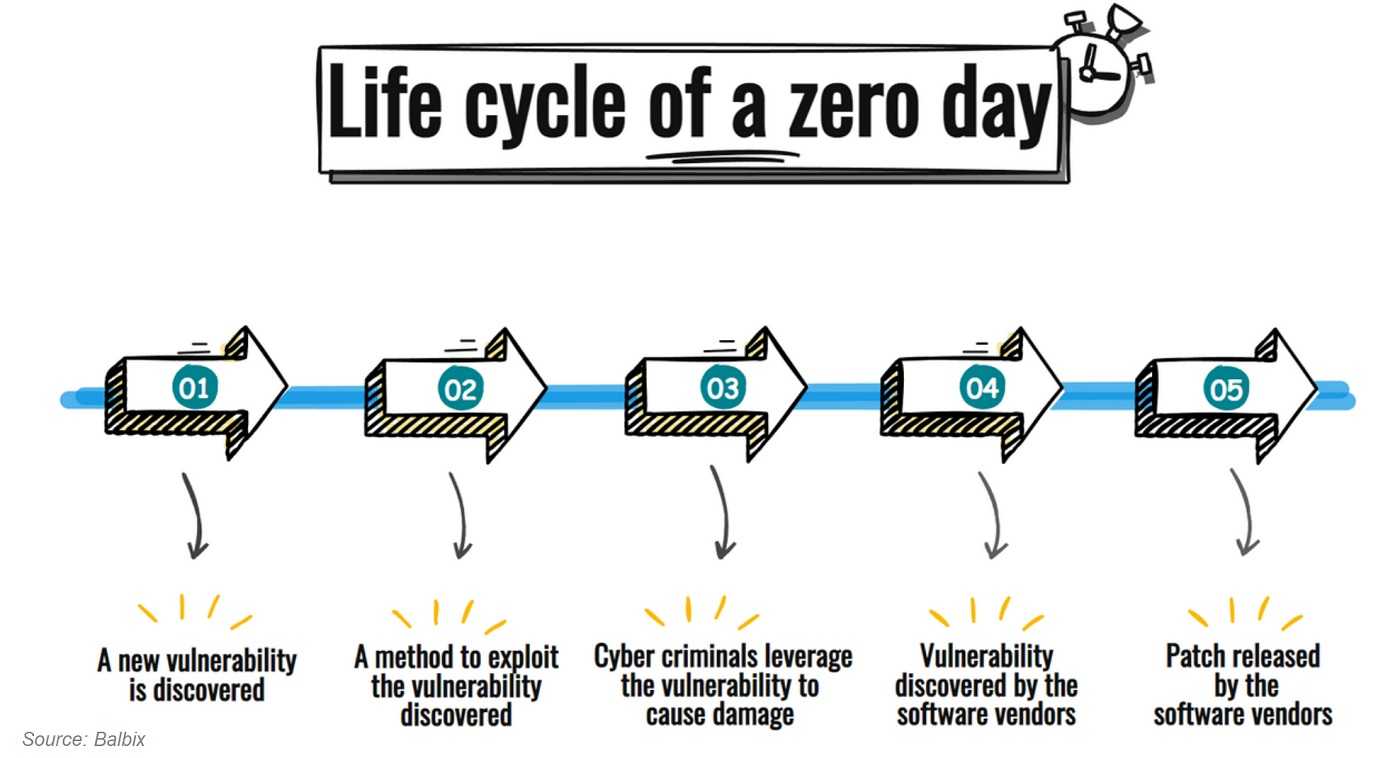
Sometimes we hear about an exploit that could cause potential harm to an individual or company and push it aside and perhaps briefly wonder if it ever actually did cause harm. If you have been paying attention to the technology news at all in the past weeks, you will know that they do indeed get exploited. One group is really busy and has made headlines a few times lately. In fact, every day there is a new story about an organization that has been attacked using the MOVEit zero-day. But no doubt, the other vulnerabilities are being abused too.
Let’s start with Clop (or Cl0p). There is a group named Clop that is a Russian-speaking group. It’s also known as Tempest, Lace Tempest, TA505, and FIN11. This group is notorious for performing large-scale attacks. It is also named after a ransomware attack, they tend to perform often, called Clop ransomware. For your cybercrime trivia night, Clop is from the Russian word “klop,” which means bed bug.
Recently, Clop has been busy exploiting a few vulnerabilities. It took advantage of the GoAnywhere zero-day vulnerability and stole the data of 489,830 individuals from the healthcare organization IntelliHARTx. The GoAnywhere MFT bug could be exploited to allow attackers onto the administrator console. A patch was quickly released for this and if you use this took and haven’t applied it yet, it’s wise to get on it.
In the case of IntelliHARTx, a lot of confidential data was accessed, including names, insurance information, diagnoses, medications, social security numbers, and other private details. Clop has also used this attack on the City of Toronto, Rubrix, Hitachi, and the Virgin Group to name a few.
But this group isn’t stopping there. It has also used the MOVEit Transfer MFT zero-day vulnerability to attack Aer Lingus, British Airways, the British Broadcasting Corporation (BBC), and the Canadian province of Nova Scotia. More recently, it broke into the State of Louisiana and stole driver’s license numbers, social security numbers, and other data for each and every license or state ID holder. That’s 4.6 million people.
This attack was also used in the recent Ofcom data breach. Clop claimed to access confidential information for many of the organizations that Ofcom regulates, as well as information on 412 employees. And the government is not off the hook. They also got to the U.S. Department of Energy. That’s a big one.
The MOVEit issues could be abused to allow attackers gain access to unauthorized access to unpatched MOVEit servers and remotely execute arbitrary code.
Not to be outdone, a Chinese-sponsored group has recently taken advantage of the ESXi zero-day vulnerability. This issue allows the attacker to gain elevated privileges and install a backdoor into the network. This group is being tracked as UNC3886. It favors government, telecom, and technologies for its targets. In addition to the MOVEit attack, this group has also been found in systems using the vulnerability against Fortinet products recently in the news for a vulnerability.
While it’s difficult to find named victims for this group, there are many reports that their attacks have succeeded.
These attacks and others like them have prompted the U.S. government to announce a significant bounty for anyone who can directly link a foreign government to the Cl0p ransomware gang. The program funding the reward is called the Reward for Justice program. That award? $10 million.
For those who are in charge of networks, please consider patching all systems right away. Stop what you’re doing and take care of it so you don’t make the news next week.
 For individuals who wonder what they can do, there are a few things:
For individuals who wonder what they can do, there are a few things:
- Check payment card charges often. Don’t wait till the monthly statement comes out. It’s easy to go online and check or use the apps to check often, if not daily. Report anything potentially fraudulent to your financial institution right away.
- Take a look at your credit reports regularly. No need to do this once a year now. They are available from each of the major credit bureaus at no charge at least once per year, per bureau. So, you can get one from one of them in January, from another agency in June, and another in November, for example, and keep better tabs on the numbers. Again, if anything is amiss, contact the credit bureau.
- Consider freezing your credit altogether. If you are not going to be applying for a loan, moving to a new rental property, or needing access to it for any other reason, consider freezing your credit. It’s free to do and even to undo for a temporary timeframe. Contact the bureaus individually to do this.
And a Pro tip: If you purchase a vehicle with cash, for instance, they still check your credit.