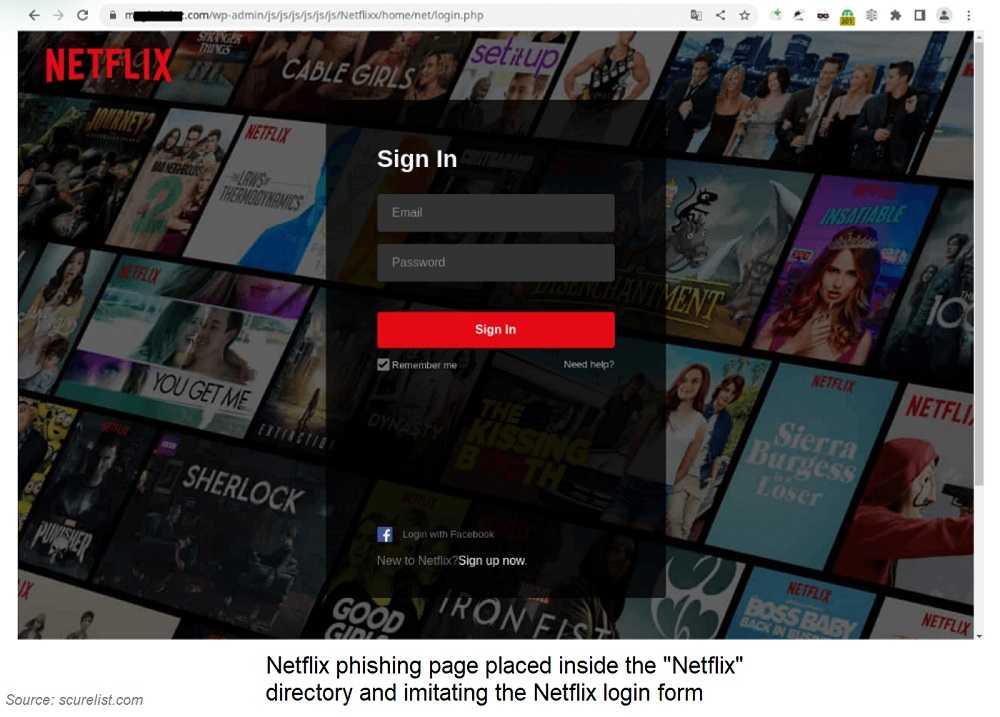
 According to a recent study by Kaspersky, there is a growing trend of attackers focusing on abandoned and minimally maintained websites for the purpose of hosting very legitimate-looking phishing pages. In fact, the research revealed a significant volume of compromised websites. Between mid-May and the end of July, it identified 22,400 distinct WordPress websites that had been compromised by threat actors to serve as platforms for hosting phishing pages.
According to a recent study by Kaspersky, there is a growing trend of attackers focusing on abandoned and minimally maintained websites for the purpose of hosting very legitimate-looking phishing pages. In fact, the research revealed a significant volume of compromised websites. Between mid-May and the end of July, it identified 22,400 distinct WordPress websites that had been compromised by threat actors to serve as platforms for hosting phishing pages.
The preference for targeting such websites is underscored by the researchers' observation that phishers are increasingly drawn to WordPress sites. This may be attributed to the considerable number of known vulnerabilities in this widely adopted content management system and its associated plugins. W3Techs reported that 43.1% of all websites have the WordPress content management system behind them.
The range of compromised websites encompasses instances where attackers easily accessed control panels due to inadequate security measures, as well as those where unauthorized entry required exploiting vulnerabilities, stealing credentials, and employing various other tactics. Notably, Kaspersky detected 200,213 user attempts to access phishing pages that were being hosted on these compromised websites.
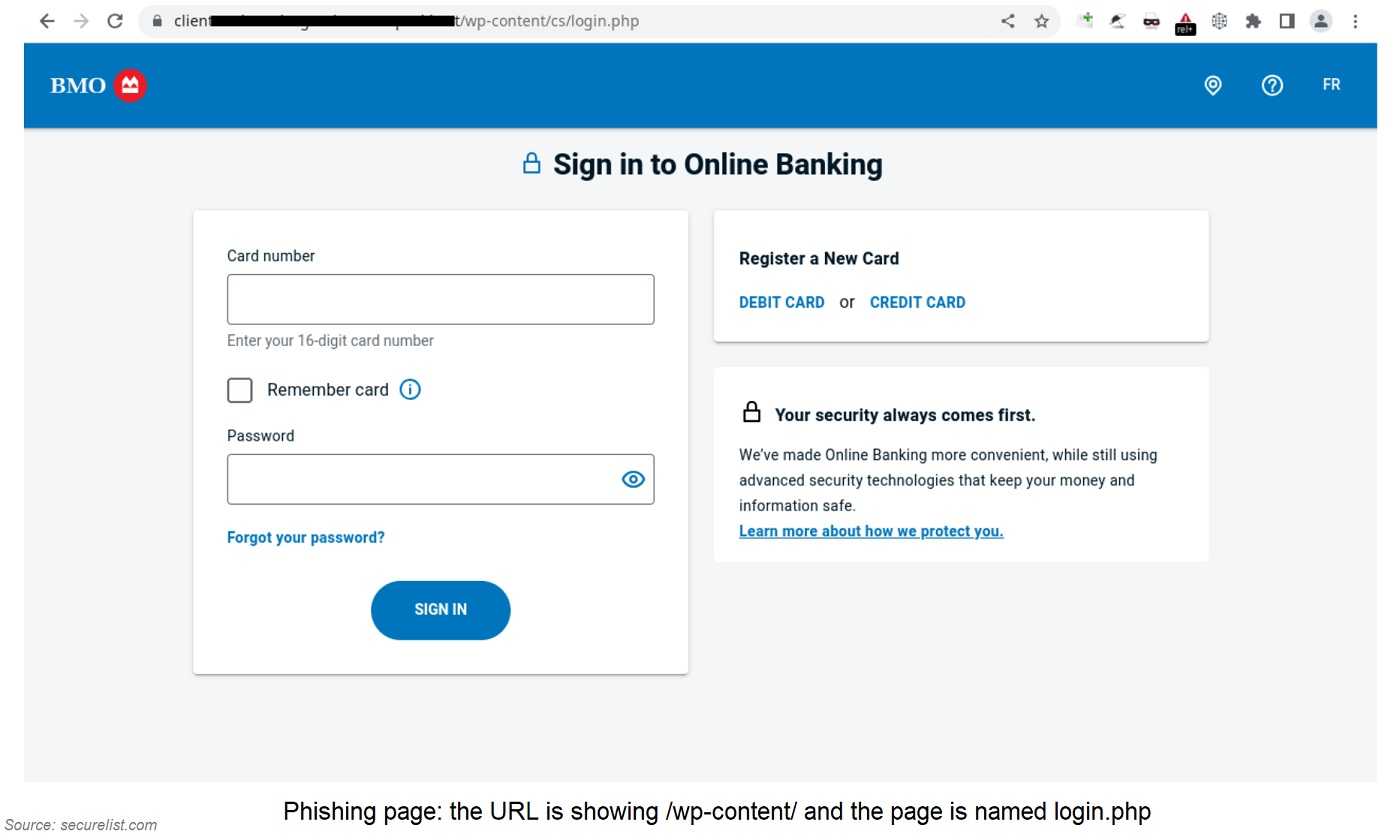
Neglected domains also appear to be attractive to attackers due to the extended duration that phishing pages can remain active on them. This is important to note, especially considering the relatively brief lifespan of phishing pages in general. A Kaspersky report from December 2021 stated that 33% of phishing pages became inactive within just a single day of being deployed. The same report noted finding 5,307 phishing pages, with 1,784 of those ceasing to function after the first day. In addition, a substantial number of them became inactive within the initial few hours of going up. Ultimately, half of the pages examined in the study disappeared within 94 hours of their creation.
What does this mean to you? Well, phishing is obviously prominent and new ways of doing it continue to appear. It’s important to always be on the lookout for all types of phishing lures. As we now know, phishing can come by way of email messages, texts and SMS, voice calls and voice-to-text messages, as well as via websites, advertising, and just about any way you can think up. And any type of attachment or link can be dangerous, including images.
Keep in mind a few clues:
- Blurry graphics and texts
- Mistakes in spelling and grammar
- Websites that are not secure (do not have the “https” at the beginning)
- Misspelled website names. Watch closely for a number 1 in place of a lowercase “L”, for example
Remember never to click links or attachments in messages that you are not sure are safe, come from unknown senders, or are not expected. Also, bookmark your frequently visited and trusted websites rather than typing them and risking making typos.
If you have a website you manage, be sure to keep it updated at all times with the latest patches. This will limit the opportunities criminals have to take advantage of known vulnerabilities.
And if you have a webpage, whether for business or personal use and are no longer using it, just remove it so it’s not left for a hacker to use against us all.