Microsoft Warns of Growing Threat: New AiTM Phishing Techniques on the Rise
November 9, 2023
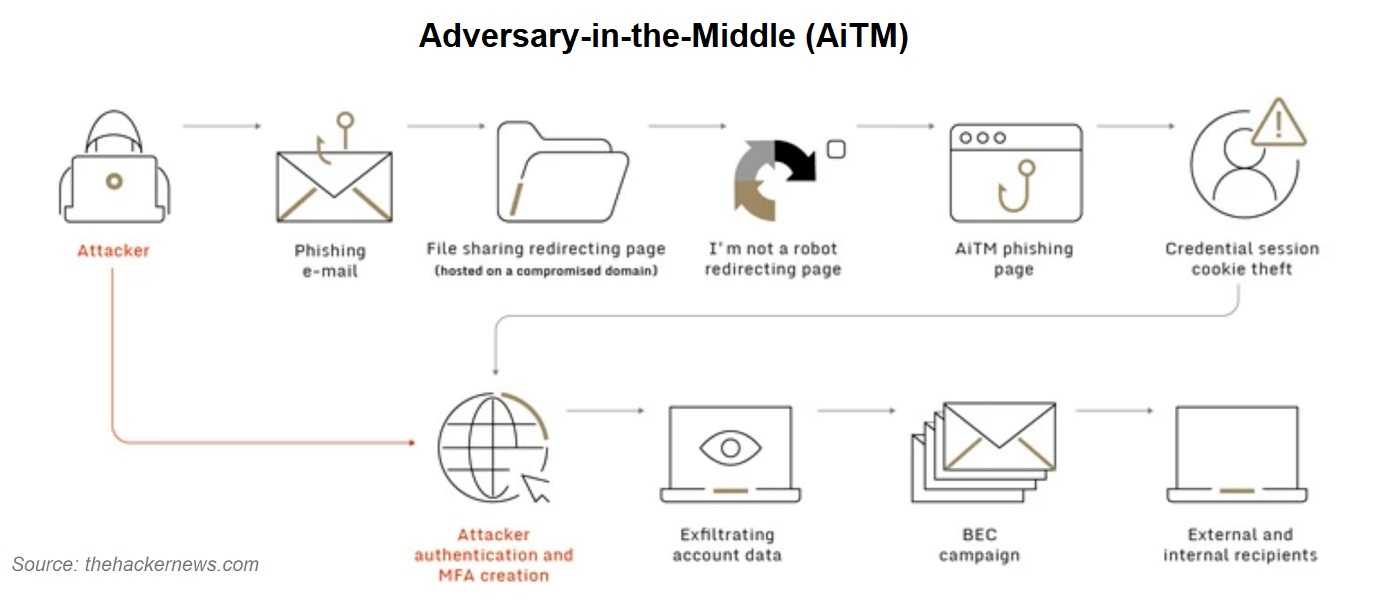
Microsoft recently issued a warning regarding the surge in adversary-in-the-middle (AiTM) phishing techniques, which have become increasingly prevalent in the phishing-as-a-service (PhaaS) cybercrime model. This worrisome trend is exacerbated by the incorporation of AiTM capabilities into existing phishing services. So, let’s figure out what this means and how you can avoid being in the middle of one of these attacks.
An AiTM, or man-in-the-middle (MiTM) attack, is a cyberattack where an attacker covertly intercepts communication between two parties who believe they are having a secure conversation. This interception allows the attacker to gain unauthorized access, eavesdrop, and pilfer sensitive information being exchanged. Often, those performing these attacks hijack the connection from those working in public locations, such as the café on the corner.
What to do, what to do? Well, one thing you can do is not perform sensitive actions from a public WiFi connection. Instead, use a VPN to secure that line or wait until you are using a trusted location to perform sensitive tasks. Next, always keep the peepers open for phishing. Don’t click unexpected links or attachments and don’t reply to the sender if you’re unsure what is in a message. Finally, don’t react to “urgent” messages without taking a second to consider if they’re phishing you.
In a recent X post, the Microsoft Threat Intelligence team noted that this evolution in the PhaaS landscape enables cybercriminals to conduct large-scale phishing campaigns aimed at getting around multi-factor authentication (MFA) safeguards. These campaigns are particularly concerning because they can target a wide audience; in this case specifically, those using Microsoft products, which is no small number.
This rise in AiTM-capable phishing services poses a severe risk to organizations and individuals alike. Microsoft's warning serves as a reminder of the evolving tactics employed by cybercriminals and underscores the importance of robust cybersecurity measures, user training, and ongoing vigilance by everyone to protect against these sophisticated threats.