The FBI has issued a FLASH alert saying that two cybercriminal groups, UNC6040 and UNC6395, are actively targeting Salesforce instances. These attacks are about stealing data and extorting organizations — criminals steal sensitive information and then threaten to publish or otherwise misuse it unless paid.
Each group has been using different methods:
UNC6040 is using social engineering/vishing (phone-based scams). It pretends to be IT support in organizations’ call centers, claiming there’s some system or connectivity issue. During those calls, the attackers trick employees into giving up credentials, MFA codes, or approving malicious connected apps. They also used fake or modified tools like a tampered with version of Salesforce’s Data Loader to pull out large batches of data.
UNC6395 took a different route and gained access via compromised OAuth tokens tied to a third-party application called Salesloft Drift, which was integrated with Salesforce. By abusing those tokens, attackers could access victims’ Salesforce environments and exfiltrate data.
Salesforce and Salesloft responded by revoking those compromised tokens and disconnecting risky integrations.
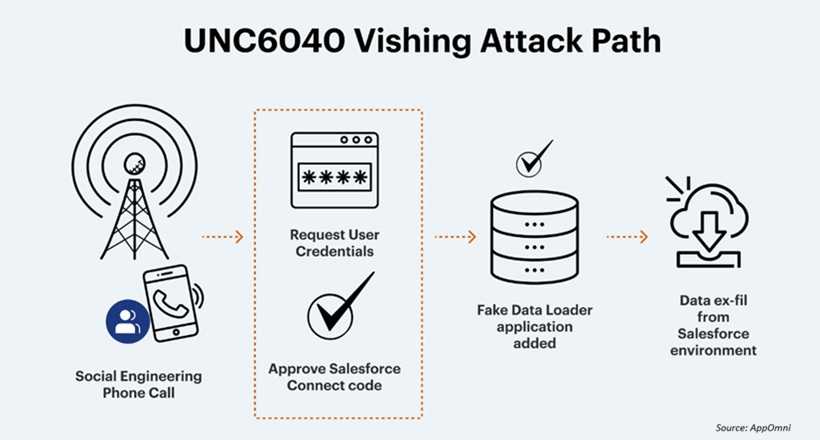
Be aware of vishing—If you are answering phones or attending to support tickets, be aware of vishing (voice phishing) techniques. Verify calls before providing credentials or making changes.
Use strong, phishing-resistant authentication—Where possible, use multi-factor authentication (MFA) methods that cannot be easily bypassed or shared. If an account allows MFA, enable it.
Implement the principle of least privilege. This may seem like it applies only to IT personnel, but it doesn’t. If there is any program or app that asks for permissions, give accounts only the permissions they need. Avoid giving administrative privileges unless absolutely necessary.
The FBI has a whole list of recommendations for IT organizations. Those can be found in the FLASH alert on the IC3 website by searching for FLASH-20250912-001.