Executive impersonation attacks, also known as CEO fraud or whaling attacks, are a type of phishing attack where attackers pose as a high-level executive, such as a CEO, CFO, or other C-Level, in order to trick employees into revealing sensitive information or transferring money. Essentially, these are other ways attackers use Business Email Compromise (BEC) attacks.
These types of attacks, no matter which name you call them, are often very sophisticated and can be difficult to detect. Attackers may use stolen email accounts or create fake email accounts that look very similar to real ones. They may also use social engineering techniques to gain the trust of employees, such as by pretending to be in a hurry or by using urgent or stern language.
Once an attacker has gained the trust of an employee, they may ask for a variety of things, such as:
- Sensitive information, like customer lists, financial data, or employee passwords
- Money transfers, often to overseas accounts
- Help with a confidential project or task
Executive impersonation attacks can be very costly for businesses. In 2022, the FBI's Internet Crime Report found that these types of attacks cost businesses over $2.7 billion.
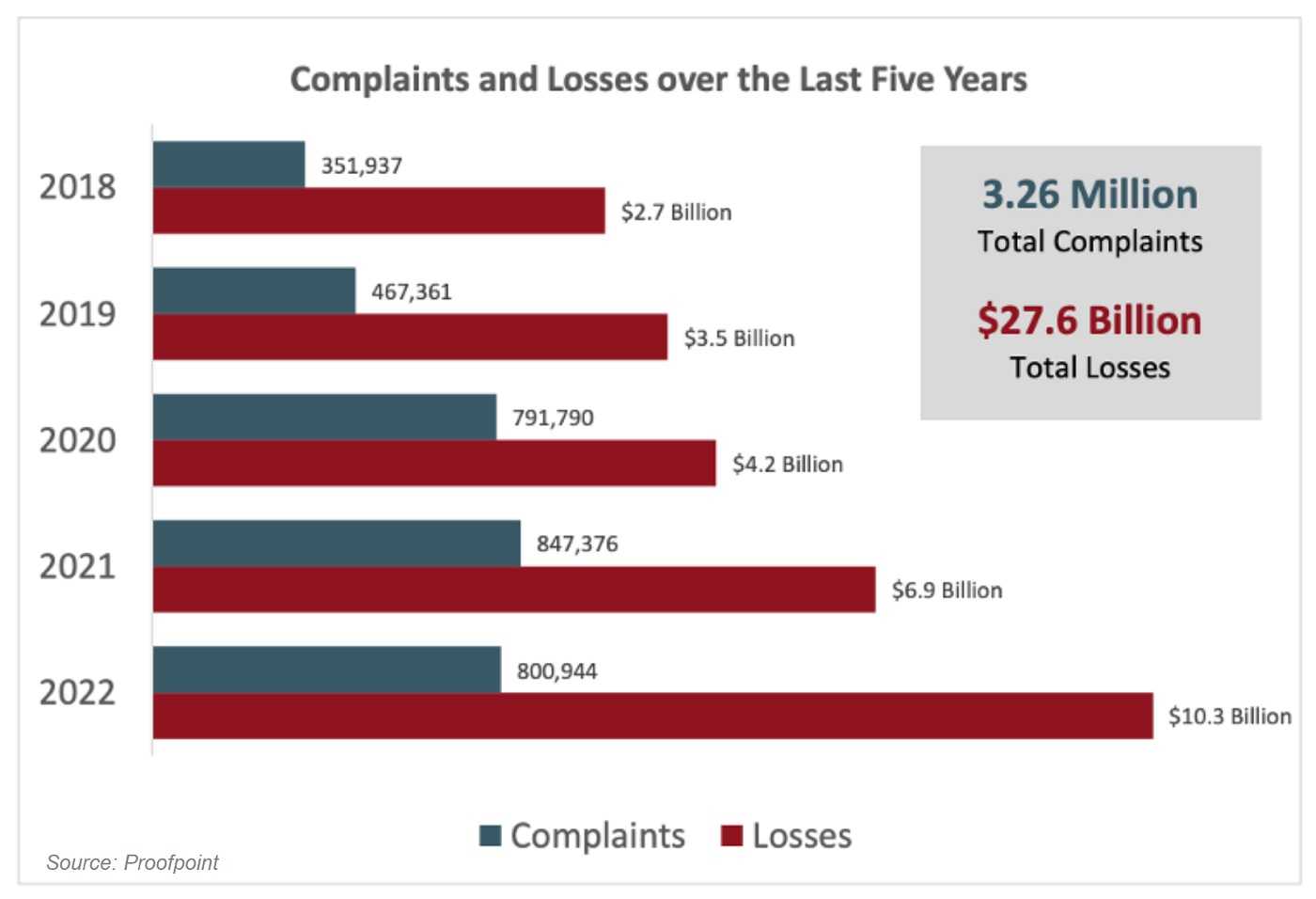
Connection to Business Email Compromise (BEC) Attacks
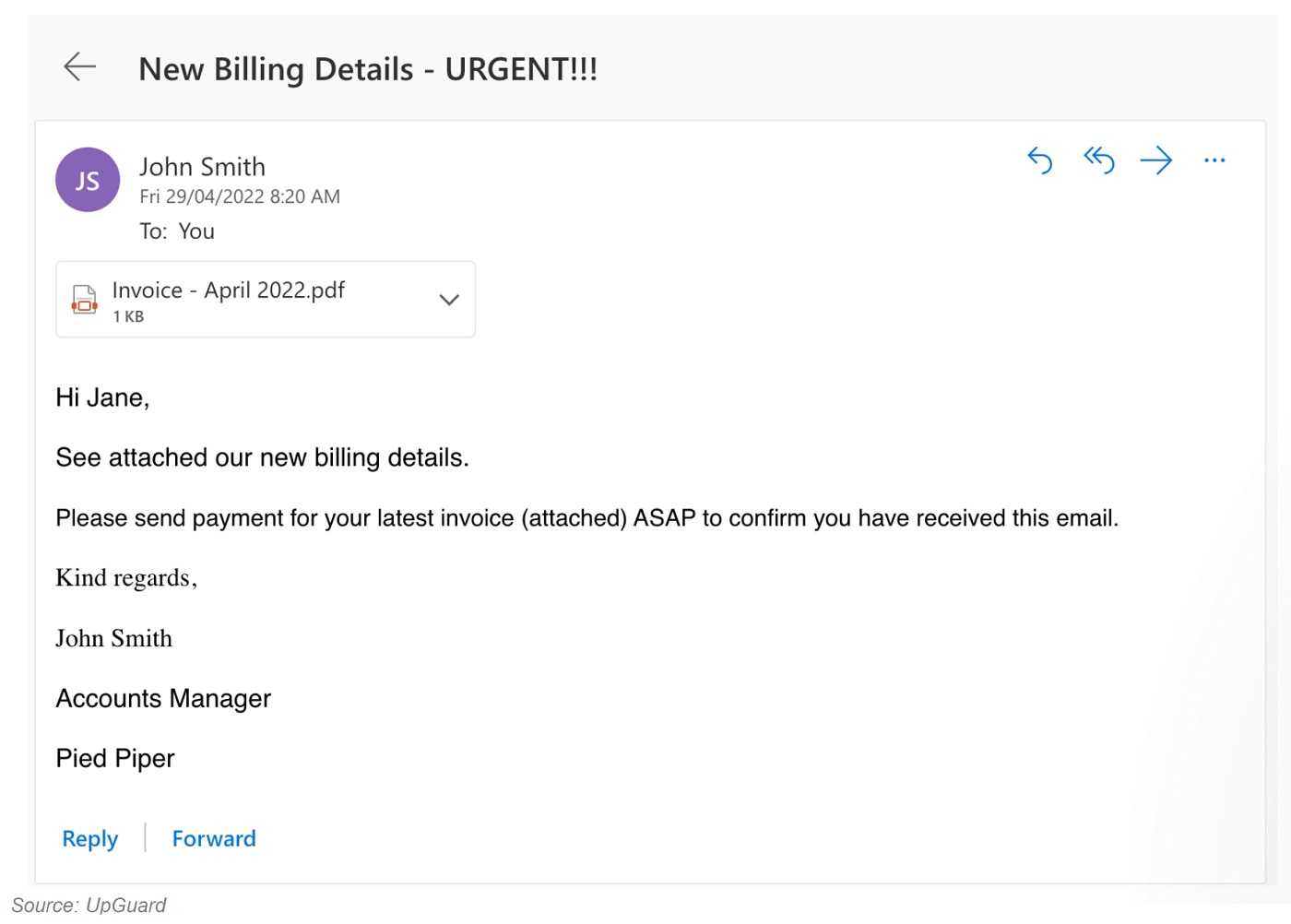
Executive impersonation attacks are often used in BEC attacks. BEC attacks are a type of phishing attack where attackers target businesses with emails that appear to be from legitimate vendors or customers. These emails may request payment for fake invoices or ask for confidential information.
Executive impersonation attacks can be used to make BEC attacks more convincing. For example, an attacker may pose as a CEO and email an employee asking them to approve a large payment. The employee may be more likely to approve the payment if they believe that it is coming from the CEO.
Executive Impersonation Attacks in Job Posting Scams and Social Media Scams
Executive impersonation attacks can also be used in job posting scams and social media scams. For example, an attacker may create a fake job posting on LinkedIn and pose as a recruiter from a well-known company. The attacker may then contact potential candidates and ask for their personal information or financial data.
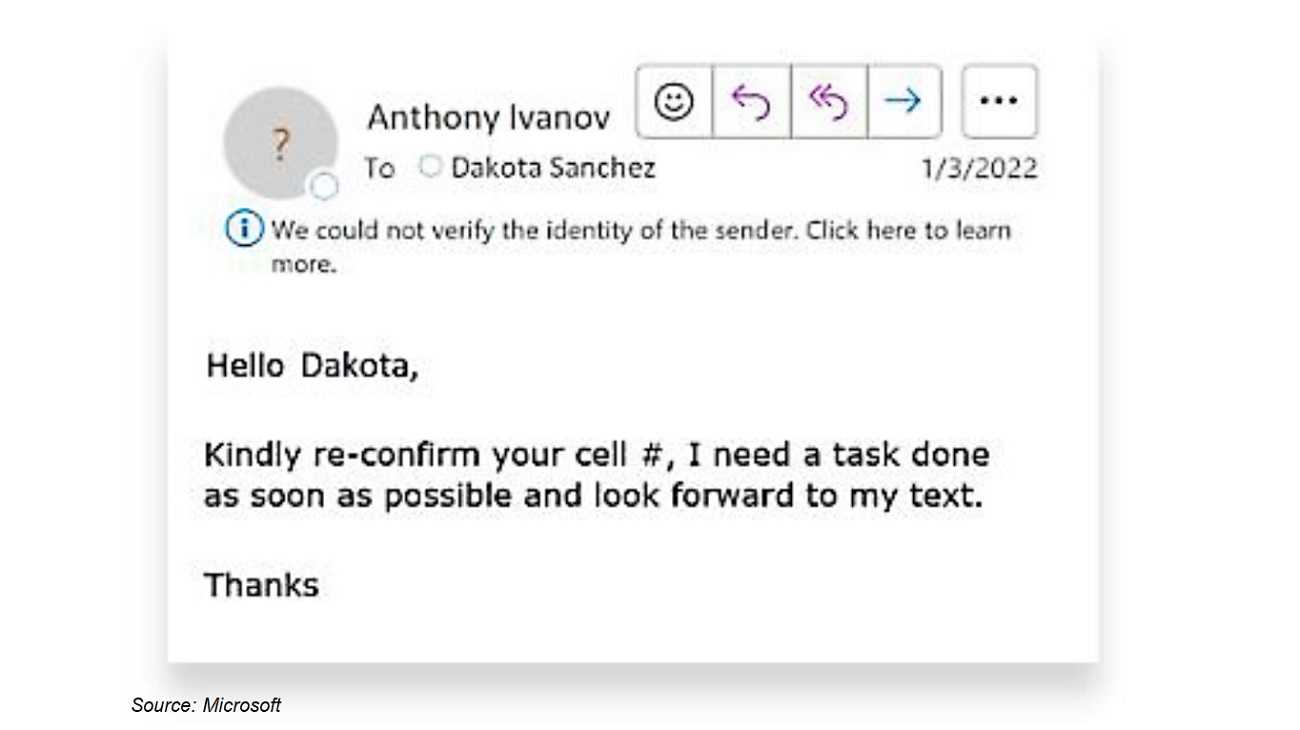
Executive impersonation attacks can also be used on social media. For example, an attacker may create a fake social media profile and pose as a high-level executive. The attacker may then contact people on that platform and ask for their help with a confidential project or task.
Prevention Tips
 There are a number of things that businesses and individuals can do to prevent executive impersonation attacks. Here are some tips:
There are a number of things that businesses and individuals can do to prevent executive impersonation attacks. Here are some tips:
Educate employees about executive impersonation attacks: Employees should be aware of the signs of an executive impersonation attack and know what to do if they receive a suspicious email or message.
Implement security policies and procedures: Businesses should have security policies and procedures in place to make it more difficult for attackers to succeed. For example, businesses should require employees to verify all payment requests with two people before approving them.
Use strong passwords and multifactor authentication: Employees should use strong passwords for all of their online accounts and enable multifactor authentication whenever possible.
Be careful about what information you share online: Individuals should be careful about what information they share on social media and other online platforms. They should also be careful about clicking on links in emails and messages from unknown senders.
Executive Impersonation Attacks are a threat to businesses of all sizes. By understanding these attacks and implementing robust prevention measures, you can shield your organization from falling prey to digital deception.