For those keeping up with technology news, it’s not often Macs make hacking headlines. And for those who are simply Mac lovers, it’s not wise to think hacks happen only to Androids since both are vulnerable. A recent finding linking bootleg Apple software, malware, and cryptomining is a lesson all users can learn from. After all, a successful attack on Macs can end up targeting Androids, too.
 Not detected until recently, security researchers at Jamf Threat Labs found a bootleg version of Final Cut Pro Apple software hiding cryptomining malware. Mac users who downloaded this unlicensed version of the $299.99 editing software found their device being used to mine cryptocurrency. Cryptomining needs immense power to work, and some miners choose to steal power from compromised devices.
Not detected until recently, security researchers at Jamf Threat Labs found a bootleg version of Final Cut Pro Apple software hiding cryptomining malware. Mac users who downloaded this unlicensed version of the $299.99 editing software found their device being used to mine cryptocurrency. Cryptomining needs immense power to work, and some miners choose to steal power from compromised devices.
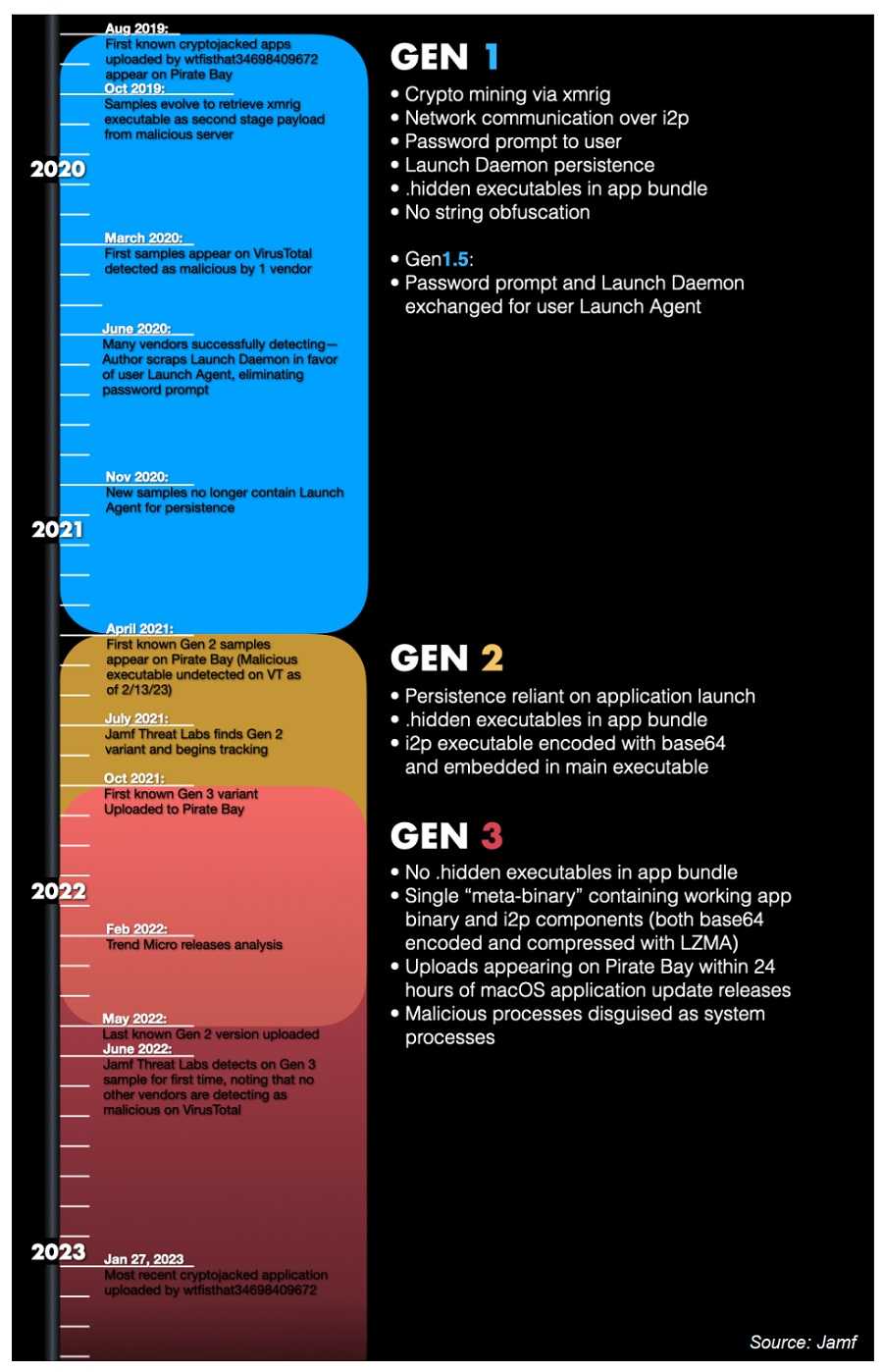
Jamf did some digging to find where this plagiarized version of Final Cut Pro was hiding. Their hunch led them to The Pirate Bay, a website infamous for offering bootleg software. Jamf found an uploader well-known for posting bootleg versions of Mac software for years, including malware-packed versions of Photoshop and Logic Pro software, is the culprit they were looking for. Otherwise known as “wtfisthat34698409672” they also learned this cybercriminal uploads variants of the malicious code in addition to posting the pirated Final Cut Pro malware.
It's All About Power, Cryptomining Power
In their research, Jamf learned the hacker began uploading pirated Mac software in 2019, and it’s been evolving ever since. They find the dozens of pirated downloads since then all have the cryptomining payload installed, but the author took steps to hide the mining from the infected device user.
Jamf says a Mac user who downloaded the pirated Final Cut Pro app may find their CPU is running hotter than usual, all the while unaware, Jamf says they are “…unwittingly mining crypto for the attacker, and opens the Activity Monitor to confirm their suspicion, the malware stops its activity and hides until the next time the victim launches the application.”
There’s a smart way to prevent a device from being infected by pirated software, and that is NOT downloading anything from third party sites. It’s well known these sites are often rife with malware-infused software apps and programs. Both Apple App Store and Google Play scan for malware before posting anything for download and should a third-party site claim they do the same, get out before it’s too late. Fixing a cryptomining-compromised device is a headache no one wants, so be smart and always avoid pirated software, mateys!