When it comes to damaging malware, Gootloader has made a name for itself. This is largely due to the impact it can have on some of the largest businesses in the world. But don’t think for even a second that it can only affect large companies. Any sized organization can fall victim to this or any other type of malware. Recently, it’s been law and accounting firms that are those targets.
To understand how risky this can be, it's important to know what Gootloader is all about and how it works within a system. Gootloader is a Javascript-based framework that has been used to steal sensitive data in the past. It works by delivering viruses into the heart of a system, causing it to start revealing sensitive data. It is quick, efficient, and has even worked against financial institutions in the past.
This is why many hackers implement this into their hacking strategy. It’s a surefire way for them to get a payday.
How it works
The main idea is that it delivers malware that causes the content management system to spiral out of control, giving it to the hackers. They can then manipulate the system and as search results are returned, the infected pages redirect the traffic right back to the attackers and their malicious websites. This is something that can be damaging to businesses that are relying on that traffic. It is malware that has long-term repercussions once it settles in.
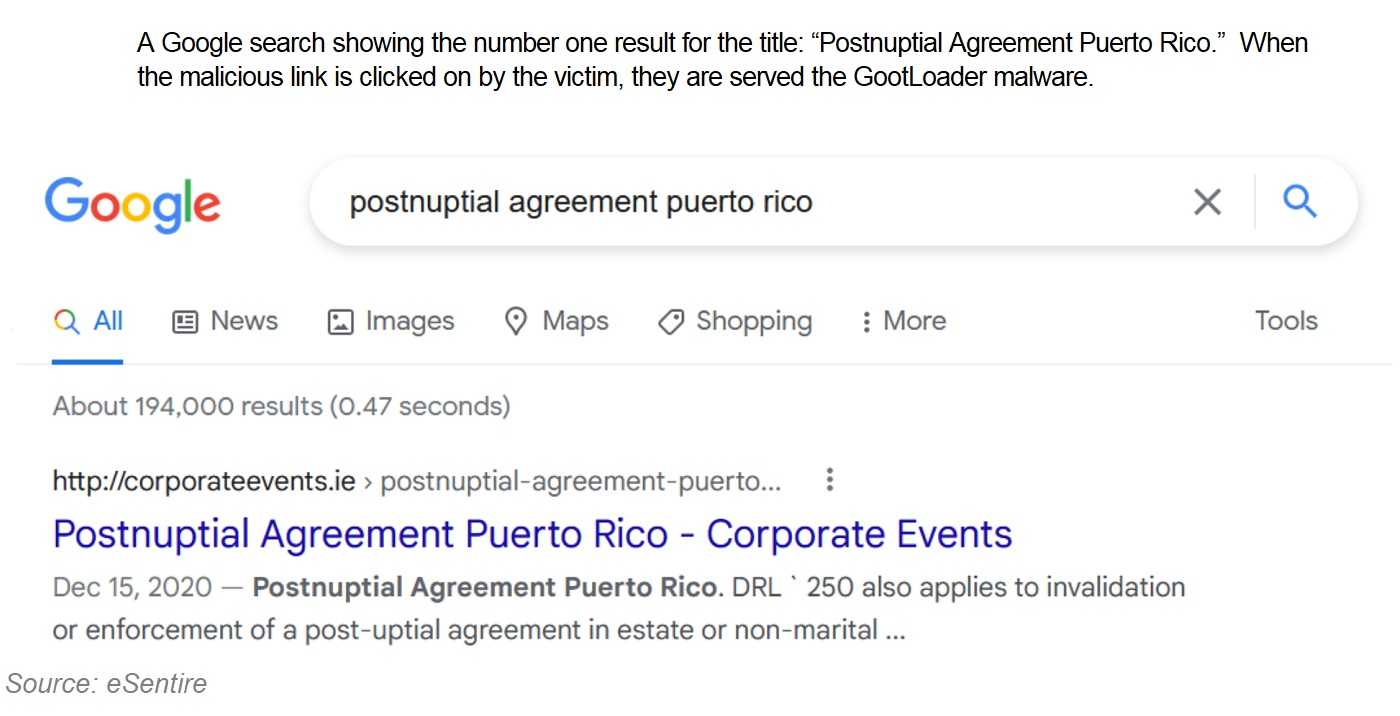
In March of last year, it was discovered that there is malware tricking unsuspecting victims into going to Gootloader-compromised WordPress websites that belong to actual businesses. The company, eSentire estimated that malicious web pages were set up in 2021 on websites in the hotel, retail, healthcare, educations, and retail sectors to the tune of 100,000 of them. In this case, the attackers attempted to employ social engineering tactics against users searching for legal agreements and documents.
What you can do
 On a personal level, always be on the lookout for attempted phishing. This goes for when at work or at home and on any device you use. If a personal device is infected, it can worm its way into the corporate network when you’re there and connect. If a link is suspicious, don’t click it. If it’s from an unknown source, don’t click it. Also, make sure your antivirus software is updated at all times.
On a personal level, always be on the lookout for attempted phishing. This goes for when at work or at home and on any device you use. If a personal device is infected, it can worm its way into the corporate network when you’re there and connect. If a link is suspicious, don’t click it. If it’s from an unknown source, don’t click it. Also, make sure your antivirus software is updated at all times.
For the IT staff, put all those perimeter security protections in place. Just remember that spam filters, firewalls, antivirus and all those other tools are not 100% effective. The in-box of the employee is still a weak point. Train everyone on how to spot phishing and do it on an ongoing basis. Once a year isn’t enough anymore. Threats evolve and change and what was once an easy to spot threat, may no longer be.