That tiny little card inserted into the side of your cellphone can lead to a heap of trouble. It’s called a SIM card and cybercriminals “SIM swap” it to clone your phone and steal your money. It’s sneaky, it’s unfair, and it’s a crime. Here’s what you need to know about this all-too-common fraud costing Americans hundreds of millions in losses and how you can keep yourself from becoming one of those victims.
SIM Swap Steps
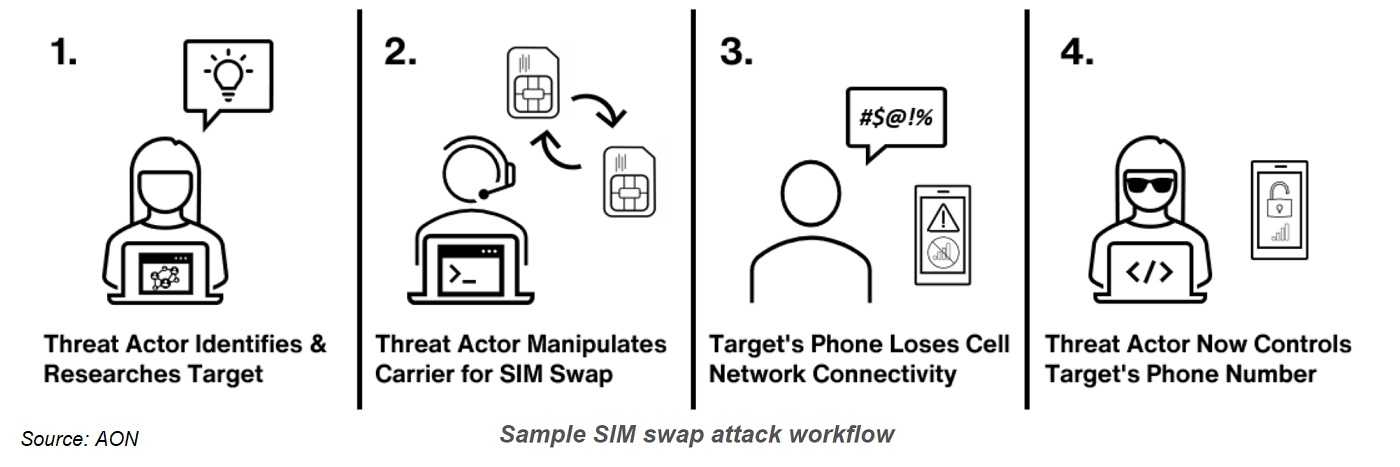
The letters SIM stand for Subscriber Identity Module. The SIM also includes a unique ID number for your cellphone account. Fraudsters start by getting your PII from the dark web and as we know, there’s a lot of it out there for them to abuse. With this information, they get to work cloning your cellphone via the SIM swap.
Armed with your PII, the fraudster contacts your cellphone company. By impersonating you, they convince the company to reassign your phone number to their own cellphone SIM card. After that happens, your phone is now cloned and ready to be exploited.
Fraudsters use your stolen usernames and passwords to log into banking and other accounts, and change the login information to lock you out. They also intercept multi-factor-authentication codes (MFA) used for identity verification. From there, they transfer funds to their own accounts, steal cryptocurrency, buy pricey gift cards, and anything else they care to do with your money.
SIM Swap Safety
If suddenly you can’t make phone calls, texts, and otherwise can’t connect with your cell service, it’s a sign a SIM swap is in the works. Below are actions to protect yourself in a SIM swap, but first, make sure you have a PIN or password on your account that you must provide to the carrier’s agent before they will make changes to your account.
 Act fast and freeze your phone number. Borrow a phone to call your cellphone carrier. Have them freeze your phone number and if you don’t have one, set up a PIN or password so they can’t make any changes to your account without it.
Act fast and freeze your phone number. Borrow a phone to call your cellphone carrier. Have them freeze your phone number and if you don’t have one, set up a PIN or password so they can’t make any changes to your account without it.
- Alert your financial institutions and find if your accounts have been breached. Consider placing a freeze on your credit, even if it’s temporary. It’s free to freeze and unfreeze your credit, so take advantage to protect yourself.
- Immediately change usernames and passwords to financial accounts. By doing this, you can prevent the fraudster from getting into the accounts since they would now have your “old” login information. Be sure the new passwords are at least eight characters and a mix of letters, numbers, and symbols.
- Don’t rely on MFA to verify your identity. If the fraudster has your phone number, they can steal the MFA codes if it comes via text or email you have set up on your phone.
- Don’t share PII on social media. Attackers troll these websites to steal any PII you post and use it in a cybercrime.
In a world where we rely heavily on our smartphones, protecting them means protecting ourselves. With SIM swapping, fraudsters turn our own phone into a weapon against us for their financial gain. So, remember, be aware and act fast. It’s the best weapon we have against a SIM swap.