Chameleon Malware Changes Its Colors Again
September 25, 2024
Android malware is constantly advancing and acquiring new frightening capabilities. Chameleon is the name of a trojan that was designed to infiltrate Android Operating Systems. This program can obtain data, with a particular focus on financial information, and carry out numerous other malicious activities; none that are in your favor.
Even more worrying is that the Chameleon Android malware received an upgrade making it new and improved from that of its former self. It is different from previous versions in that it uses a sophisticated technique to access and compromise devices. The changes include Device Takeovers (new term alert: DTO) and granting attackers the ability to bypass device biometric authentication. That sure is malware changing its colors!
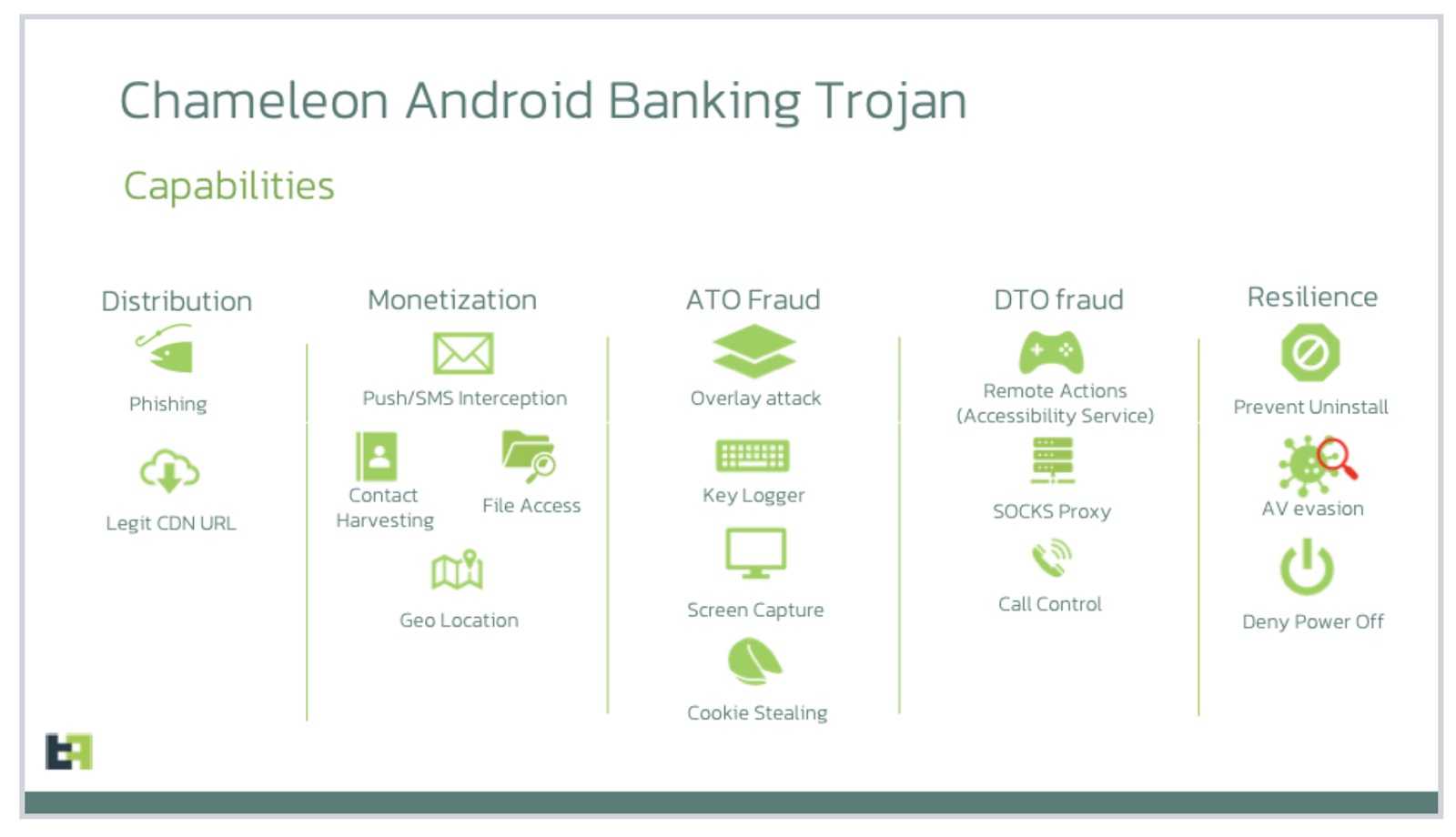
The updated Chameleon malware infects Android devices with an OS 13 or newer versions pretending to be legitimate browsers like Chrome or cryptocurrency apps, banking apps, ChatGPT, and other popular apps.
The Trojan works by first scanning your device to check whether it is Android version 13 or higher. It then will initiate loading of an HTML page and guide the user through a process enable the accessibility service, per ThreatFabric’s researchers.
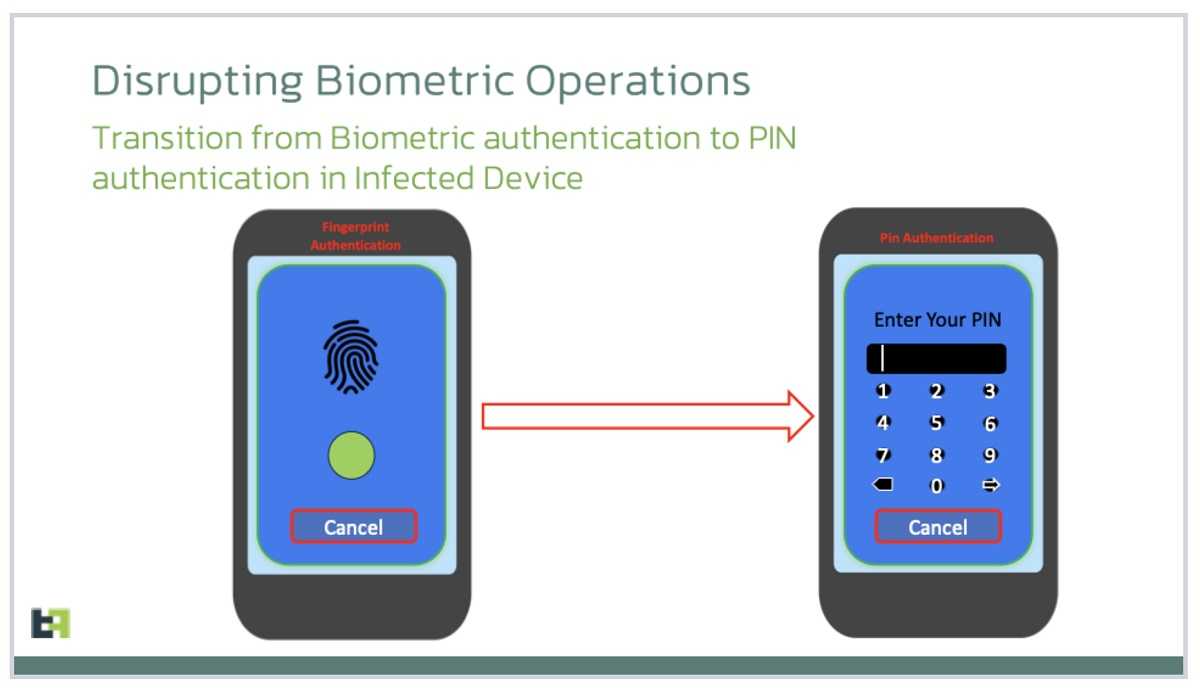
After that, it has necessary permissions to enable it to carry out unsanctioned actions like blocking its uninstallation. Once it’s there, you’re stuck with it. Chameleon will ultimately disable the biometric authentication capability and steal the associated PIN, allowing the malware to access the phone as needed with the stolen information.
The upgraded Chameleon Android malware version has extended its reach from unsuspecting users from Poland and Australia to other regions, such as Italy and the UK. It’s on its way to the U.S. as well.
So, be very wary when downloading programs from third-party sources. Get them from the official app stores for whichever device you have. And update your apps as soon as you see that red dot on your app screen. Not only will it help protect you from malware like this, but it’ll make that dot go away!