There are terms that are often mentioned in the cybersecurity world, especially when the topic of the dark web comes up that some may not exactly understand. The dark web may be confusing enough. However, another term is "tor" as in "tor site" or "tor network." Another is the "deep web." Fortunately, it’s not really that difficult to understand and we’re here to help break it down. So let’s take a deeper dive into the dark web to find out how scary it actually is down there.
A Tor site is a website or online service that is accessible through the Tor network. Tor, which is short for "The Onion Routing" project is a network that enables users to browse the internet anonymously and securely by routing their internet traffic through a series of encrypted relays. The connection goes through several layers to ensure privacy; as in layers of an onion. It was originally created at the U.S. Naval Research Laboratory to help intelligence sources communicate securely and safely, particularly in areas where the safety of personnel is critical. Now, it’s used for all kinds of things, but has gained that reputation for being used for evil.
Unlike regular websites that can be accessed through standard web browsers, Tor sites can only be accessed through Tor browsers and the websites end in “.onion.” The web addresses themselves are made up of a series of randomized characters, making them difficult to remember or guess. For example, a Tor site address might look something like "3g2upl00q6kufc4m.onion." That’s just a random set of characters and may or may not actually go to a dark website.
Tor sites are designed to provide enhanced privacy and anonymity to both website owners and visitors. Because Tor site connections are encrypted and routed through multiple relays, it is challenging for anyone to trace the online activity back to its origination. This makes Tor sites particularly appealing to individuals who want to protect their identity, bypass internet censorship, or engage in activities that require a higher level of anonymity, for example, undercover investigations by law enforcement.
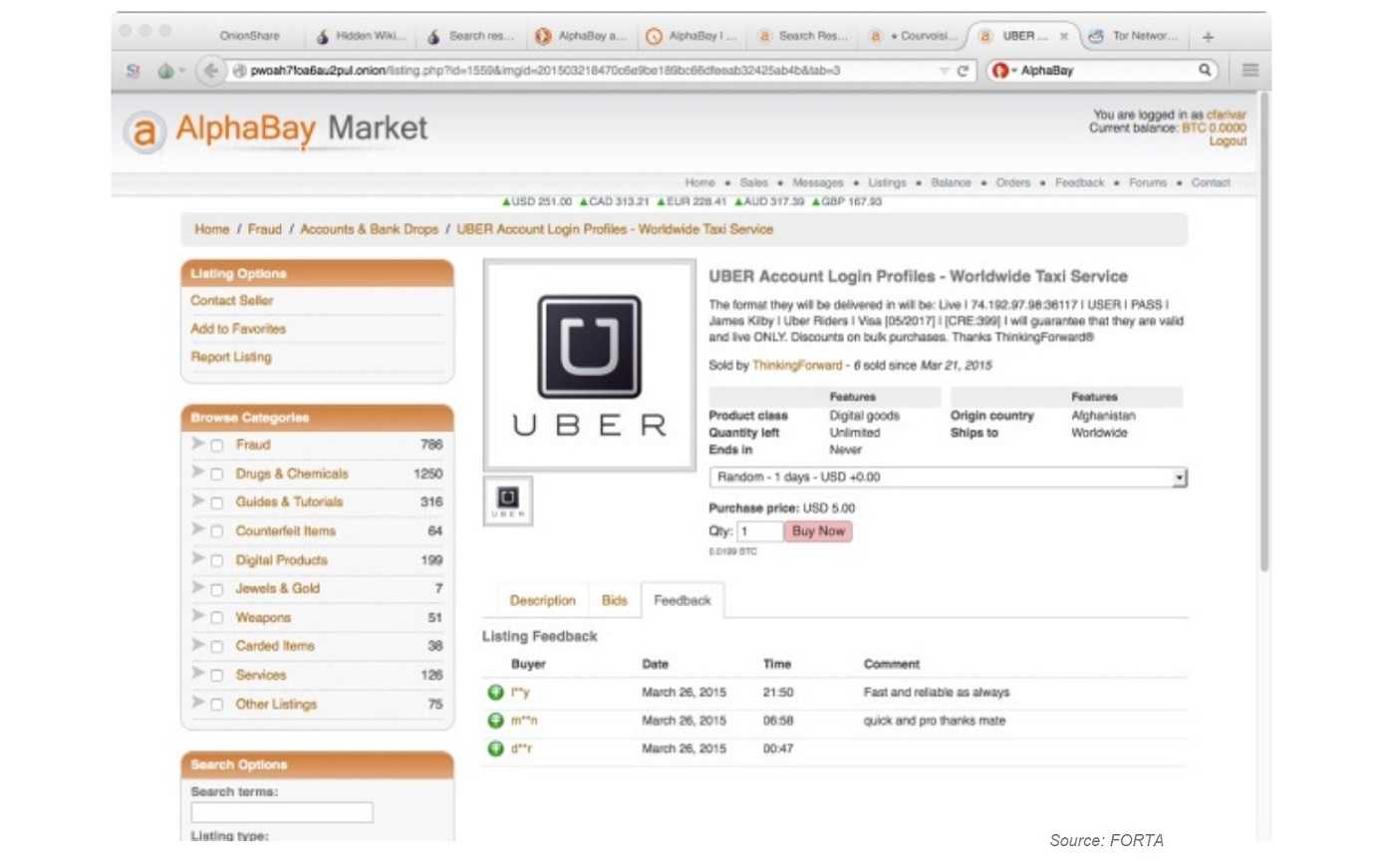
However, due to this anonymity, Tor sites have gained a reputation for hosting a wide range of content, including both legal and illegal activities. While there are legitimate Tor sites that offer services such as secure communication platforms, whistleblower platforms, or alternative social media networks, there are also Tor sites that may host illegal marketplaces, hacking forums, or other illicit content. In the United States, it isn’t illegal to access the dark web or go through a Tor site, but it is illegal in some countries.
It’s important to note that if you are going to dive into the Tor network, ensure you have anti-virus/anti-malware software installed on your device and that it is updated with the latest version. If you’re poking around in there, it’s likely you’ll encounter malware at some point.
Overall, Tor sites offer a unique and anonymous way to access online content, providing both advantages and potential risks depending on how they are used.
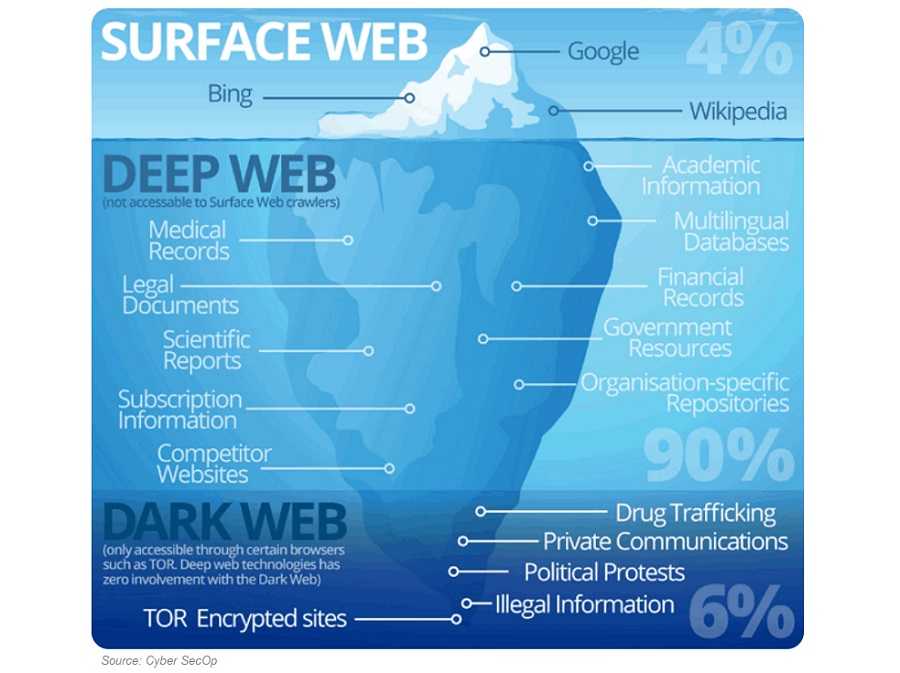
One final note, there’s also the “deep web.” Sometimes “dark web” and “deep web” are used interchangeably. However, they are not the same. The deep web goes even further and includes legitimate content that requires a fee for service. For example, while Netflix is accessible on the surface web, a lot of what is available is not. To get to it, you need to pay a fee and/or log in, therefore it’s part of the deep web. The dark web is also one part of this deep web.
This is only a very short introduction to the deep and dark web. If you want to know more, there is no shortage of information freely available to you on the surface web. Just type the terms into a search engine and you’ll find it.