Attackers are getting more creative by the day. It's more important than ever before with so many bad actors out there to make all of your accounts ultra-secure. That means that using some method of multifactor authentication (MFA) is in order. Case in point: Recently, there was an elaborate scheme targeting unsuspecting users that would perhaps not have been victims, had MFA been enabled.
Essentially what these crafty hackers did was break into a Microsoft Exchange server, use administrator permissions, and use those to send out mass spam email messages.
You might be asking why they would feel the need to use someone else’s email server to do this. Well, because phishing email is more likely to be opened if it looks like it comes from a legitimate domain. Therefore, because the hackers were able to gain access to the Exchange server, they could make it look like the email messages were just that…from somewhere legitimate and perhaps less likely to be marked as spam. By doing this, it masked the real origin of the email, which was actually third-party email marketing services.
The spam email that was mass delivered was promoting fake sweepstakes where recipients were encouraged to put their credentials into a form. This is a common phishing scheme used by bad actors. However, what made it so effective is that by using a hacked server, they were able to gain privileged access to user accounts. The hackers essentially used these user permissions to grant themselves administrative permissions, which essentially gave them unlimited access. They used these permissions to craft messages and use the legitimate organization’s domain information, which allowed them to bypass spam filtering tools.
This attack could have been prevented, if only the administrator accounts had some form of MFA enabled. MFA requires users to not only input their passwords but also provide some other form of identification beyond that. For instance, once you input your password, you would be asked to then provide an authentication code or device that only the administrator has access to. This could be in the form of a hardware key that you physically plug into a device, an authentication app, or even an email verification.
Without this type of protection in place, the bad actor only needs to gain access to the account by hacking the password. This can be done through brute-force methods as well as in other ways.
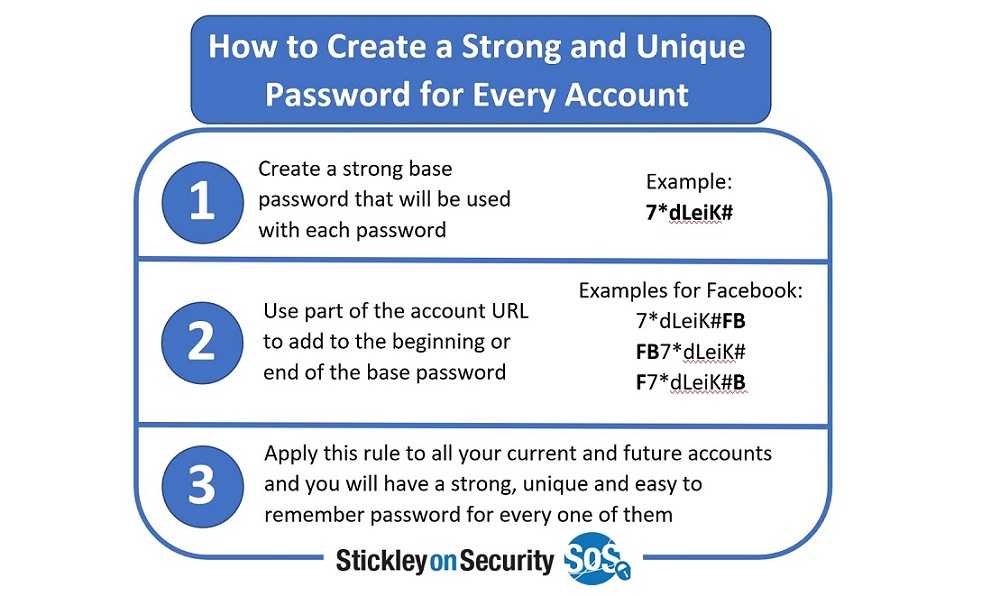
This is another reminder that having unique and strong passwords for each account is necessary. If they get one password, they won’t be able to use it on multiple accounts. When creating passwords, use at least eight characters, combining letters, number, and special characters. If you can’t remember all of them (yes, we know there are so many of them), try associating them with clues and use the clue to jog your memory. You can also consider password managers. However, there are risks to using those. There recently was a breach involving LastPass. Although that company claims master passwords were not accessed, there have been cases where those were and that meant all other passwords were also accessed and needed to be changed.
As a last resort, write them down on an old-fashioned physical sheet of paper and keep it tucked away out of sight; preferably in a locked drawer. The more you can do to protect your accounts, such as enabling MFA when it’s offered, the safer all of your information will remain.