A ransomware threat group known by several names, one of them being Oktapus, recently made another name for itself. Thanks to its spree of high-profile attacks this summer, Microsoft researchers call them “one of the most dangerous financial criminal groups.” A closer look at this group explains who they are, who they attack, and why they’re so dangerous.
Call them what you will, Oktapus, Octo Tempest, Scattered Spider, or UNC3944, these threat actors mean business. Most recently, the group's top attacks were on MGM Resorts, Caesars Entertainment, and Clorox, just to name a few. So, who is behind this multi-named ransomware threat group?
What’s In A Name…
Whatever name this group is known by, the makeup of who’s behind it stays the same. First observed in 2022, Oktapus is a native English-speaking group made up of young threat actors. The industries their attacks are focused on are gaming and hospitality, financial services, and technology and manufacturing, among others. As a threat group known for using ransomware as the means to their goal, they’re targeting big money for their financially motivated attacks.
Other descriptions of Oktapus by security professionals include well organized, prolific, highly effective, dangerous, and capable of resorting to threats against a target’s employees and families. In other words, not exactly a group you’d invite to your next barbecue.
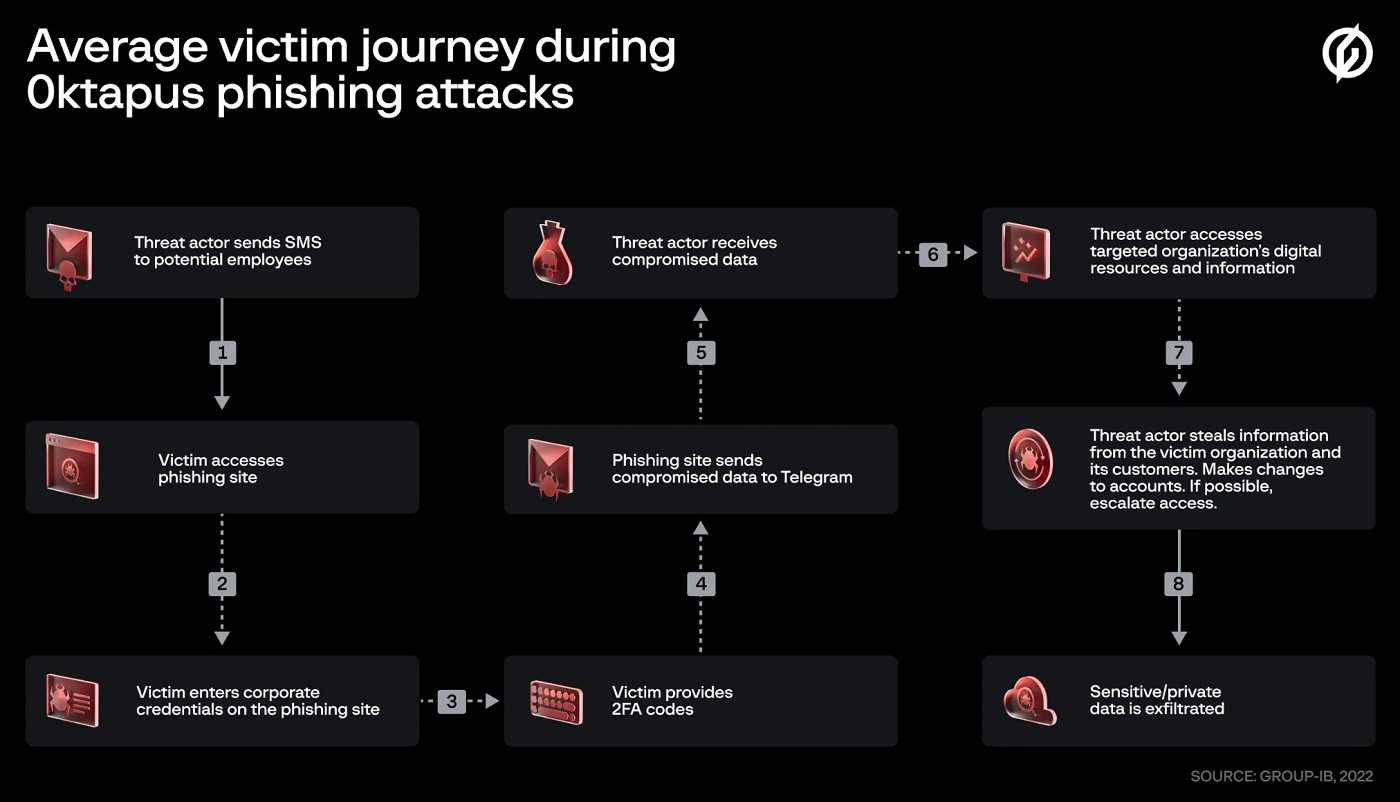
How Oktapus Attacks Unfurl
Microsoft Threat Intelligence reports Oktapus attacks begin by using socially engineering tactics to gain entry into an organization and its system infrastructure. From there, they hijack essential and confidential corporate information as bait for ransom payment extortion.
There’s a lengthy list of other Oktapus victims targeted this past summer. Among them were Okta, an authentication and authorization service. Following Okta was a string of attacks against its customers – Cloudflare, 1Password, and Beyond Trust.
In the ever-evolving online world where we work, shop and play, keeping one step ahead of cybercriminals is a worrying thought. While ransomware threat groups aren’t new, the continued success of Oktapus remains to be seen.