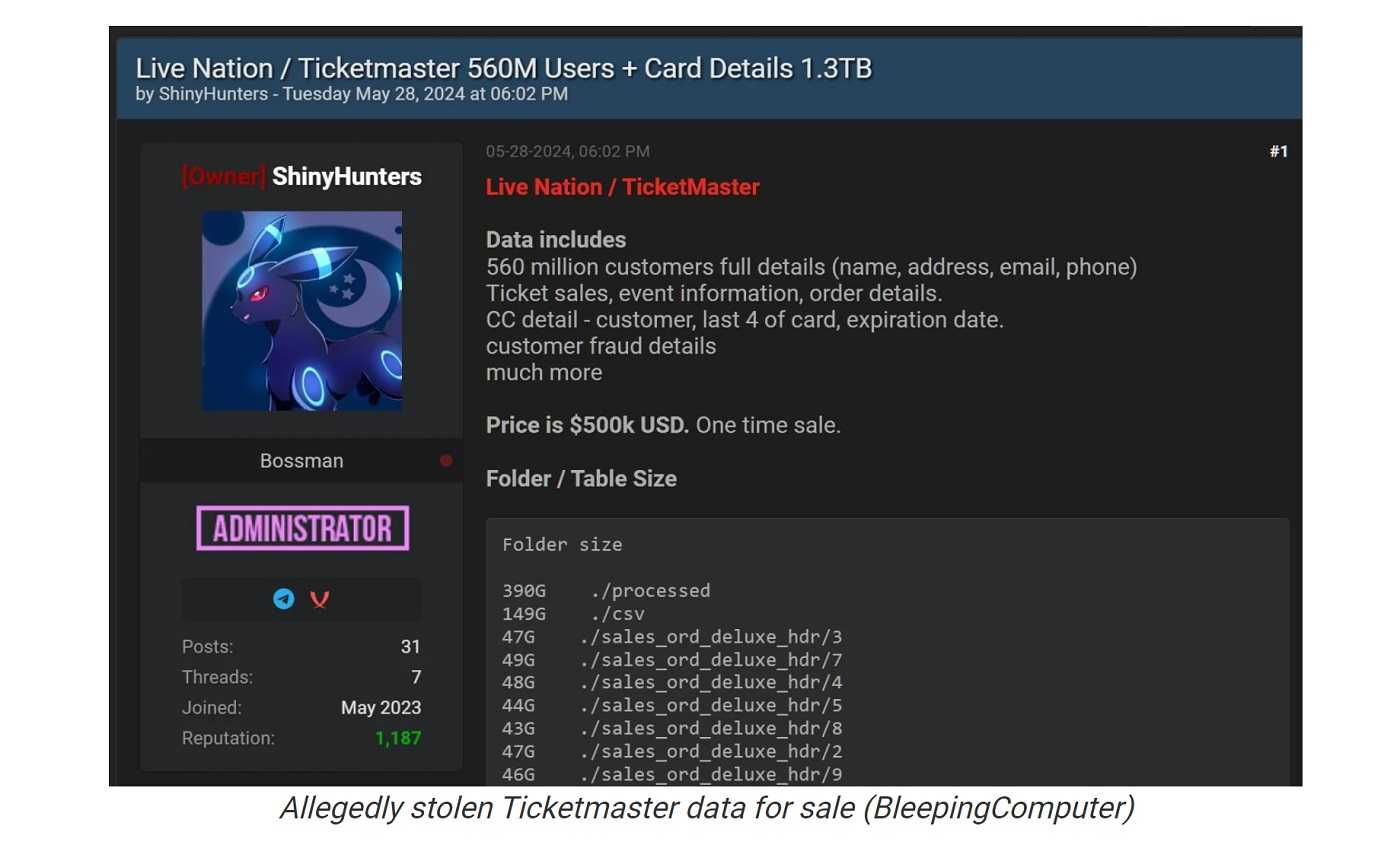
In late May 2024, Ticketmaster experienced a significant data breach that compromised the personal information of approximately 560 million customers. The breach was discovered on May 20, 2024, when Live Nation, Ticketmaster's parent company, detected unauthorized activity in a third-party cloud database, reportedly provided by the company Snowflake. While the attack occurred on May 20, it’s believed the attackers actually began their attack in mid-April. The breach was publicly acknowledged on May 27, 2024, after a threat actor known as ShinyHunters began selling the stolen data on the dark web for $500,000.
The data, amounting to 1.3 terabytes, includes names, addresses, email addresses, phone numbers, and partial credit card information, as well as details of ticket sales and transactions dating back to 2011. Although full payment card details were not exposed, the breach poses significant risks for social engineering and phishing attacks.
In a conversation with ShinyHunters, reporters from BleepingComputer found out that the group was interested in finding buyers for the data. They also said they believed one of the buyers that approached them was Ticketmaster.
The attackers mentioned they accessed the Ticketmaster data by stealing credentials from an employee of Snowflake. They then used that information to get into the employee’s ServiceNow account which ultimately allowed them to create session tokens and access customer accounts. Those were used to download data.
Ticketmaster is cooperating with law enforcement and has initiated an investigation to mitigate risks and inform affected customers and regulatory authorities. This incident highlights the vulnerabilities in cloud-based storage solutions and the need for robust security measures?. The responsibility for vetting third-party providers falls on the organizations using them. However, employees also bear responsibility for being on the lookout for attempted phishing attacks.
ShinyHunters also mentioned to BleepingComputer they used the same strategy to steal data from many other companies including Anheuser-Busch, State Farm, Allstate, and Nieman Marcus. They are known to gain access to accounts with stolen credentials via Microsoft Office 365 and GitHub, as well as others.
In a ddition to phishing attacks, those with Ticketmaster accounts should consider adding multifactor authentication (MFA) protection on their mobile accounts to prevent against SIM swaps. This happens when an attacker convinces a cellular provider to change a customer’s phone number to a new device controlled by the attacker. Typically, this is a PIN set up with the provider.
ddition to phishing attacks, those with Ticketmaster accounts should consider adding multifactor authentication (MFA) protection on their mobile accounts to prevent against SIM swaps. This happens when an attacker convinces a cellular provider to change a customer’s phone number to a new device controlled by the attacker. Typically, this is a PIN set up with the provider.
Phishing ID Tips:
- Unexpected links and attachments
- Messages from unknown senders
- Generic greetings
- Misspelled words
- Incorrect grammar
- Blurred graphics and logos
- Sense of urgency to take an action