In the world of business, cyberattacks against organizations can end in disaster. It's no secret that employees are constantly targeted by phishing and other attacks. In fact, it's expected. But when high-ranking execs are the target, it's something not-so-expected. These are specially designed hacks known as "whaling," and there's an ongoing malicious campaign targeting them by Russian and Nigerian hackers.
According to Proofpoint, this phishing campaign exploits Microsoft Azure, a cloud computing platform specializing in the business community. Data privacy, collaboration, and disaster recovery are just a few benefits of using this cloud. As such, hackers are using Azure to phish a range of high-ranking employees and whales, from CEO's and Vice Presidents to Finance and Account Managers. These types of targets provide a rich pool of those closely connected to a hacker's goals.
This particular phishing attack uses a malicious domain with a Microsoft lookalike subdomain, office360outlooksupport, to fool victims into clicking the link.
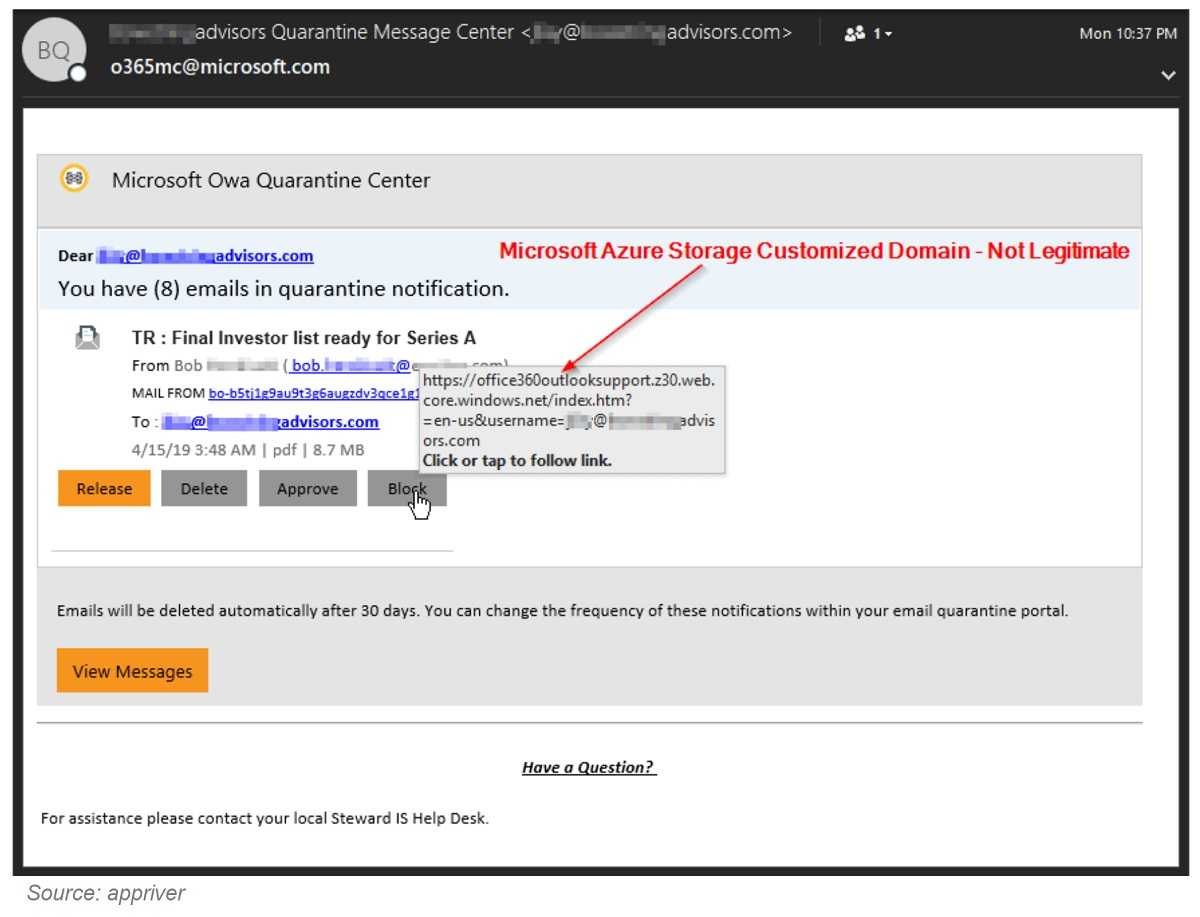
Clicking the link brings the victim to the phishing site that looks very much like the Microsoft login portal. It automatically pre-fills the recipient's email address, making the site look that much more believable.
Whale Phishing Made Easy
With whales being a more fruitful target than lower-level staffers and sometimes, they're also easier to catch. Cyber-educated staffers know they're a phishing target, so they keep a lookout for red flags. However, senior-level execs don't expect to be phished, so red flags often get overlooked. Hackers embed malicious links in emails and documents with a "click here" prompt, and a busy exec is likely to comply — especially when they think it's from a trusted source. From there, hackers are green-lighted for any number of attacks.
After gaining access to a whale account, some successful attack options direct hefty money transfers to the hacker's account, install backdoors, and orchestrate BEC (Business Email Compromise) attacks. All of these can cause lasting damage to an organization's finances and reputation, and all because a busy whale was phished.
Whale Cyber-Safety
 Phishing-smarts are something everyone should know, regardless of rank. And employee cyber-education should always include the whale population. Things like not clicking on links and attachments unless they're verified with the sender, urgent and unexpected requests, prompts to click, typos and bad grammar are all blinking red lights. Since hackers are good at impersonating trusted and high-level employees, fake wire transfer requests are a favorite. That's why important transactions, especially having to do with finances, should always have enhanced verification processes such as placing a separate phone call to the requestor or having multiple eyes look at and approve them. Anything slightly suspicious should be deemed just that.
Phishing-smarts are something everyone should know, regardless of rank. And employee cyber-education should always include the whale population. Things like not clicking on links and attachments unless they're verified with the sender, urgent and unexpected requests, prompts to click, typos and bad grammar are all blinking red lights. Since hackers are good at impersonating trusted and high-level employees, fake wire transfer requests are a favorite. That's why important transactions, especially having to do with finances, should always have enhanced verification processes such as placing a separate phone call to the requestor or having multiple eyes look at and approve them. Anything slightly suspicious should be deemed just that.
With attackers targeting high-level execs via Microsoft Azure, no matter how busy or how far up the food chain an exec may be, a cyber-smart whale and strong verification steps can stop an attack in its tracks.