Sneaky Email Phishing Uses Corrupt MS Word Files
June 27, 2025
Always looking for new ways to swindle us, hackers are using purposely corrupted Word files to hook unsuspecting users. The success rate of this email phishing attack is nearly 100%, so knowing what to look for before you get hooked can help prevent this latest cybercrime.
Sneak Attack
Any.Run, a malware hunting firm, found corrupt Word files attached to emails. Intentionally corrupted by hackers, they know the files will sneak past Microsoft’s malware checks. The files pretend to be from human resource and payroll departments, using bonuses and/or benefits as lures, making it even more difficult to determine if they should be opened. They even use legitimate company branding. Very tricky.
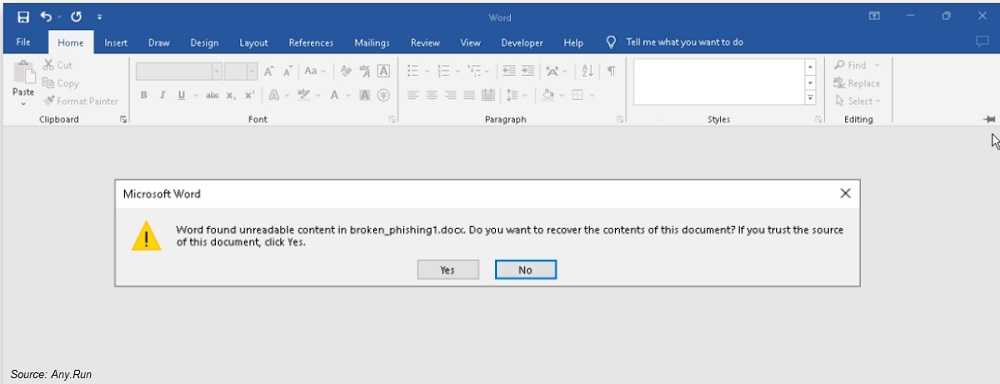
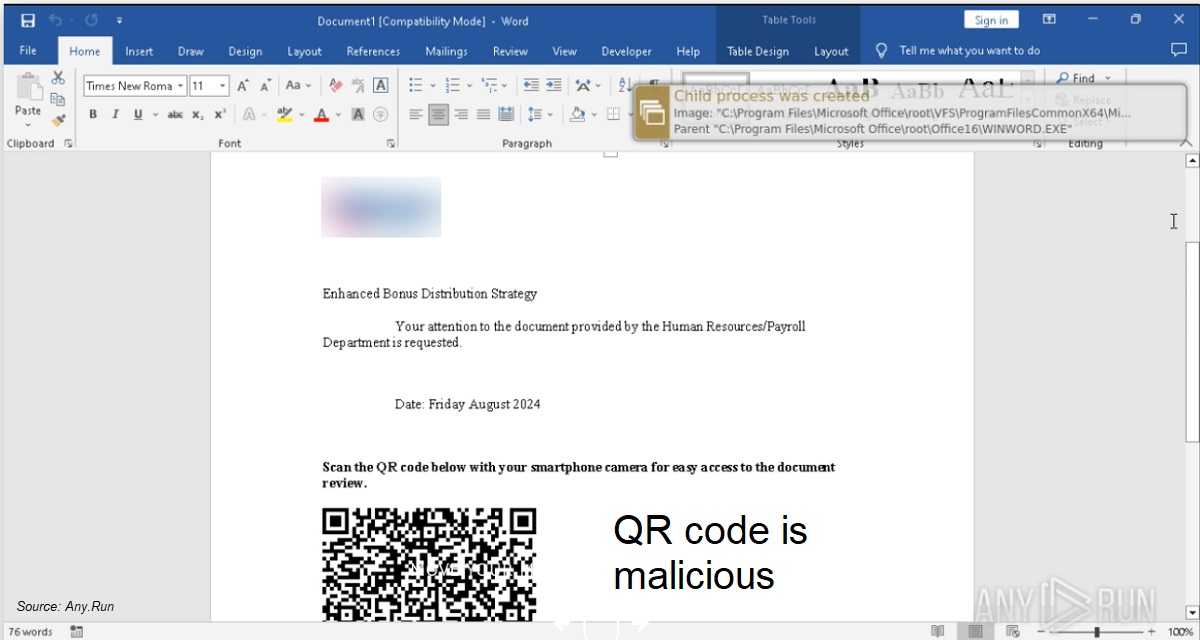
Even worse, this scam uses Microsoft’s own document recovery feature to open the corrupt file. Once it’s restored, victims see an embedded QR code. Scanning the QR code leads to a fake Microsoft login page or a phishing website, with both designed to steal your credentials.
Phishing Cyber-Smarts
With 91% of malware delivered via phishing, this latest scam shines a bright light on the importance of verifying the email sender before taking any other actions. Alerting a network administrator or human resources will verify if it’s for real. Below are more phishing cyber-smarts to follow.
- Verify the sender before clicking on attachments or links. A simple phone call will do.
- Be wary of generic greetings, misspellings, grammatical errors, or bad graphics.
- Pressure to act fast is a hacker calling card. Take the time to check it out.
- Beware emails requiring you to verify personal or financial information. When in doubt, don’t.
- Use common sense. If you have any second thoughts about an email, it's better off deleted.
With new phishing threats seeming to pop-up at the speed of light, it’s on everyday users to put up a defense. Not only do we need to protect against the scams we know about, but also those in the making. That’s where phishing cyber-smarts make a real difference with your online security—and peace of mind.