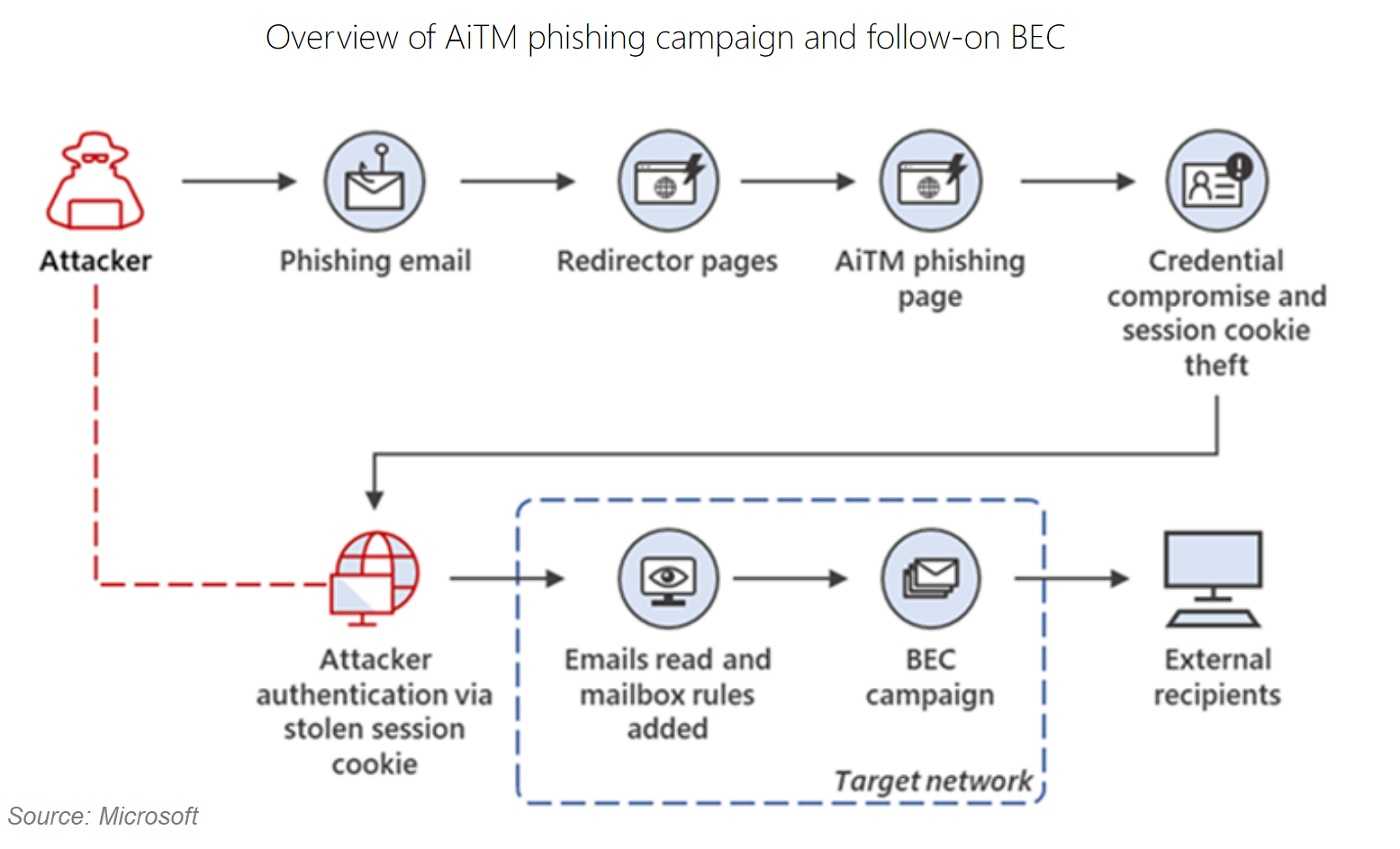
Microsoft has recently identified a series of sophisticated adversary-in-the-middle (AiTM) phishing and business email compromise (BEC) attacks aimed at banking and financial services institutions. It found that the attackers initially compromised a trusted vendor, subsequently launching AiTM attacks and follow-on BEC activities against multiple organizations.
Do you need to know the technical details? Not particularly, but you do need to know that it happens and what to do about it. Let's start with that part.
To mitigate the impact of these attacks, Microsoft recommends that affected organizations revoke session cookies and revert any modifications made by the threat actors within the MFA process.
For users, always be aware of attempts to steal personal and confidential information when visiting websites. If you have any inkling something is amiss, immediately close the webpage and delete the cookies from your browser.
But what are these terms?
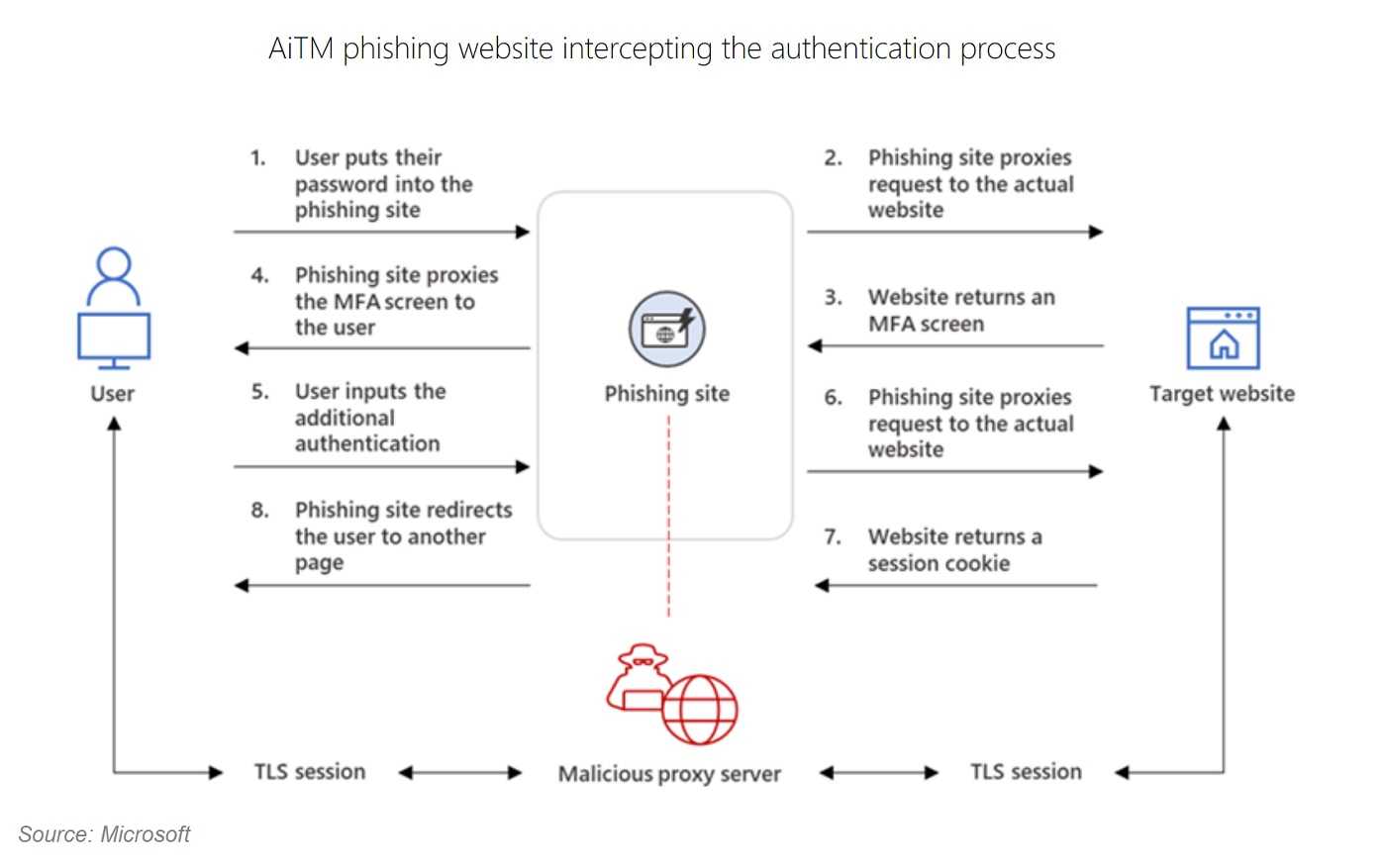
We’ve heard of Man-the-Middle (MiTM) attacks before. While the two terms, AiTM and MiTM may be used interchangeably, they are ever-so-slightly different. In MiTM situations, the attacker inserts him or herself into the connection between two parties making them believe they are communicating with each other directly, all the while stealing information that passes through.
In AiTM, there is still the person in the middle, but the attacker is mirroring the behavior of the end-user and steals credentials and session cookies so they can get into the account without full authentication, such as needing the MFA code. The threat actors set up a proxy server between the targeted user and the intended website, which in this case, is a phishing site under the control of the attackers. Through this proxy server, the attackers gain access to the user's traffic.
Cookies, in this context, refer to files containing identifiers sent by website servers to browsers for temporary storage. These cookies facilitate faster website loading and improved navigation. A common example is the shopping cart feature on e-commerce sites, which retains selected items during browsing. Without cookies, the cart would reset every time the user navigates away. They also allow you to go to a website multiple times without putting in your username each time.
In the subsequent phase of this attack, the attackers proceeded to send over 16,000 emails to the targets' contacts as part of a second-stage phishing campaign.
Phishing is often used for BEC attacks too. These involve exploiting email communication to deceive individuals in an organization, often finance or HR personnel, into transferring funds or sharing sensitive information. Attackers use targeted phishing techniques, leveraging known information to build trust and increase the likelihood of success.
According to the FBI's Internet Crime Complaint Center (IC3), BEC attacks result in financial losses for businesses worldwide, amounting to billions of dollars annually.