What do hackers do in their spare time? They create jigsaw and other types of puzzles to hide their various attacks. That’s according to recent Microsoft reports, anyway. The software giant’s Security Intelligence team has stated it saw that in a recent attack, an “HTML attachment is divided into several segments, including the JavaScript files used to steal passwords, which are then encoded using various mechanisms…” But wait! There's even more!
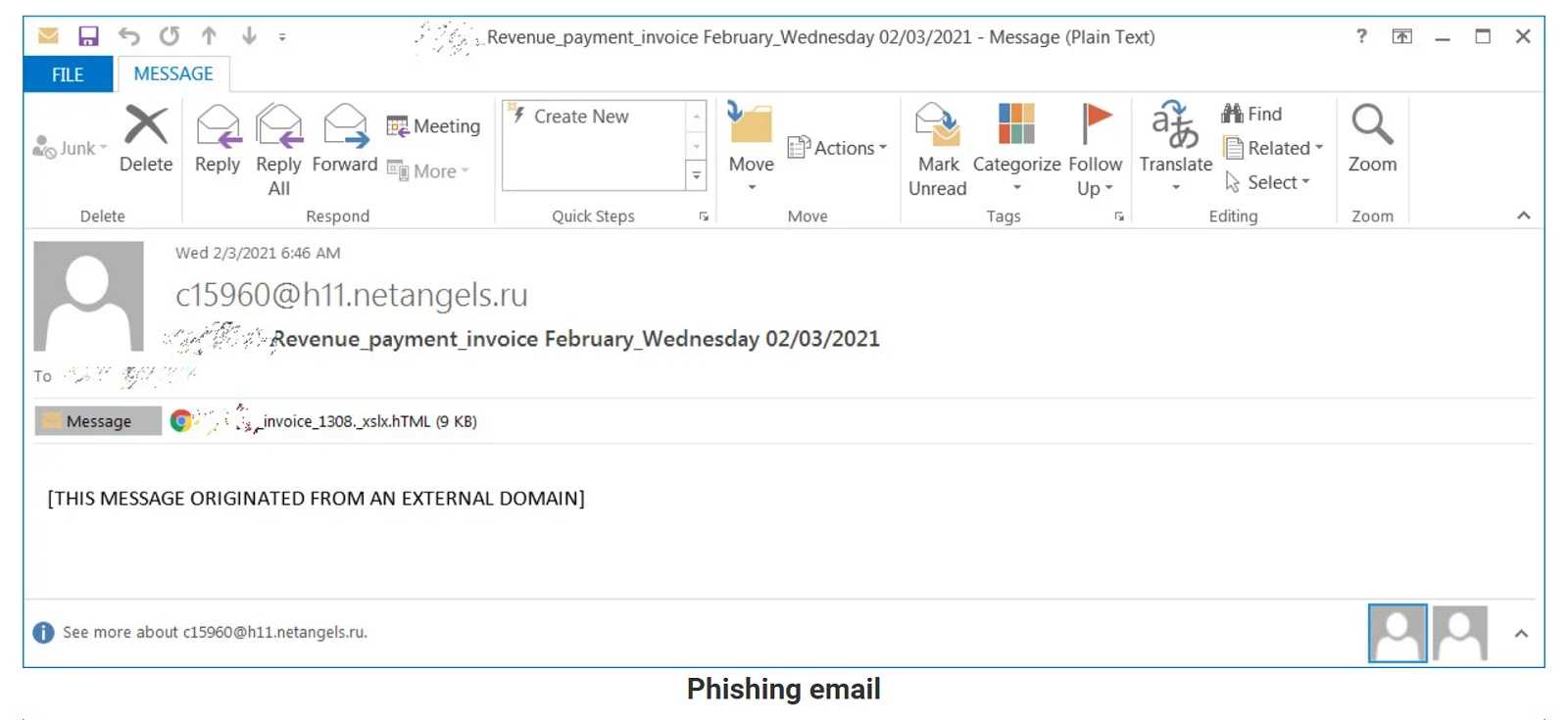
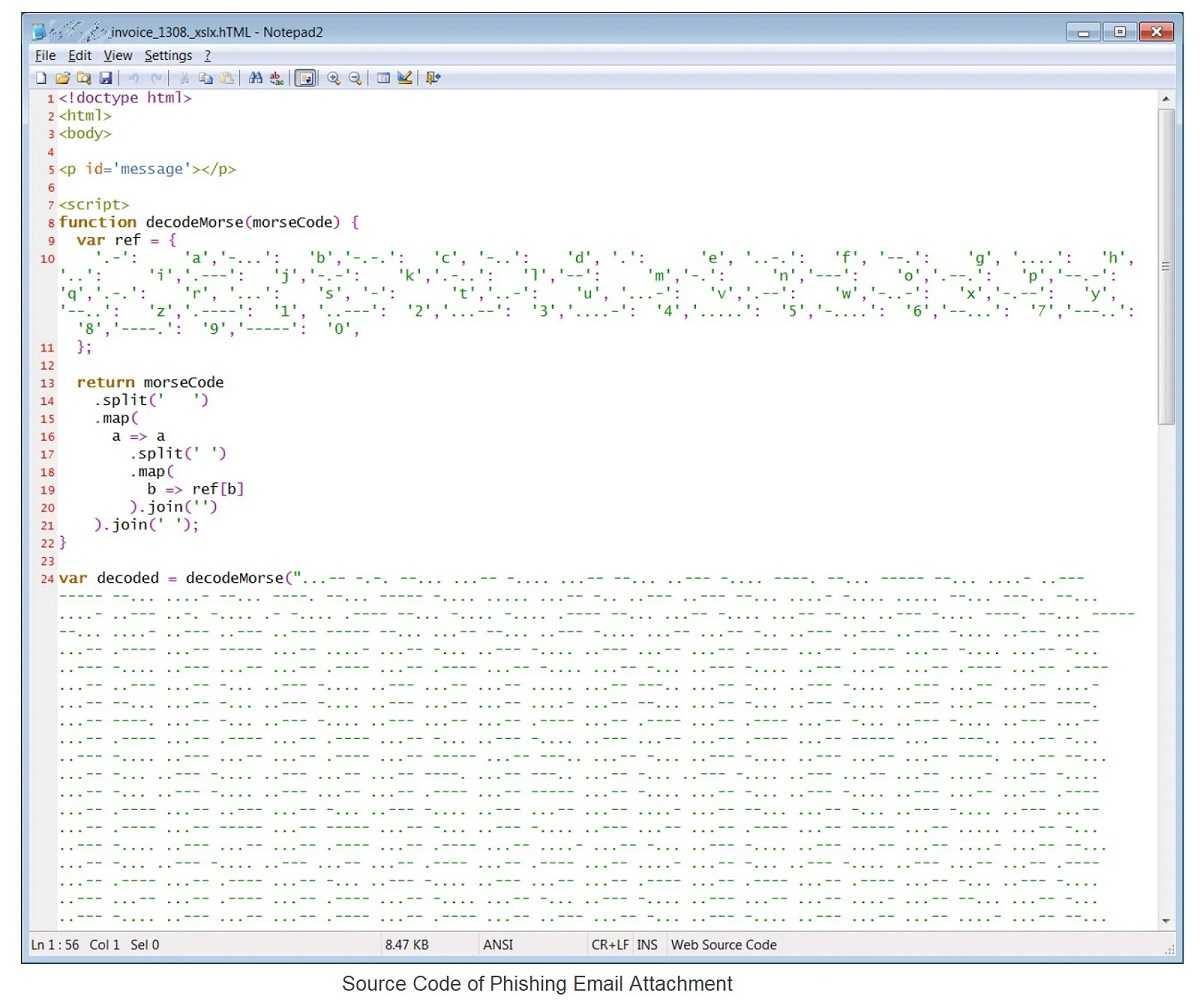
Apparently, the attackers migrated away from using plaintext HTML code to using multiple encoding techniques, to be clever. Some include, “old and unusual encryption methods like Morse code, to hide these attack segments,” the report continues. They liken it to a jigsaw puzzle, meaning that segments of the code are seemingly harmless and able to bypass the usual security measures. However, when all those pieces are put together, it becomes more like a clown wielding a chainsaw in a horror film.
It’s not after a teenager in this case, however. The idea is to collect login credentials, in particular, for financial accounts, likely with intent to perform business email compromise (BEC) attacks. Of course, the lures are in the form of good old phishing email messages, specially crafted to appear as something like vendor payment suggestions. The subject lines may contain accented characters, but there is also an attached Microsoft Excel (.xls) file with perhaps even the company logo, that is very enticing to click. But don’t do it! Just as in that horror movie, the outcome is predictable.
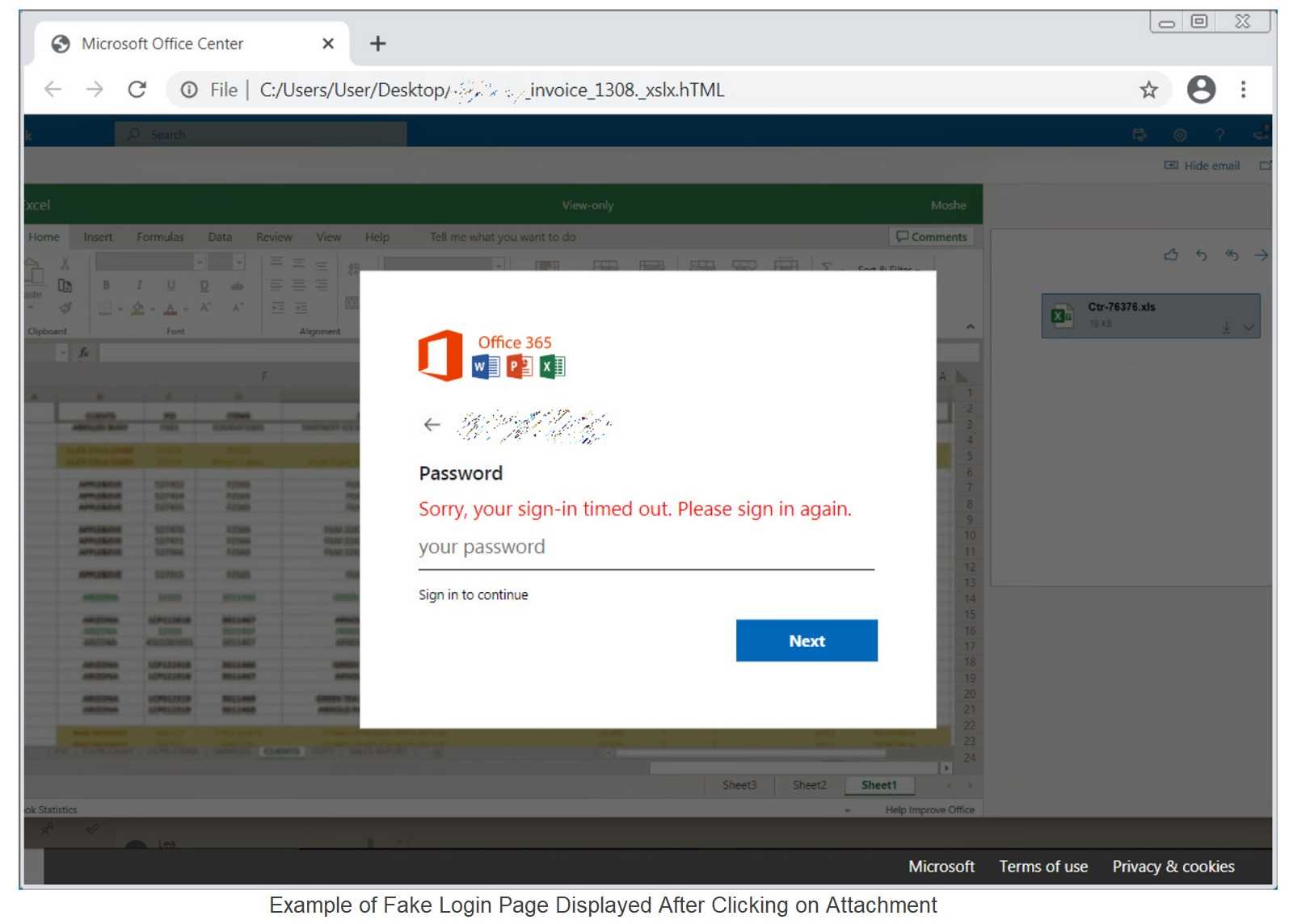
The changes look something like this, according to Microsoft:
February 2021: The Morse code method of encoding that uses dashes and dots to represent characters, was observed ("Organization report/invoice"). Links to the JavaScript files were encoded using ASCII, then in Morse code.
May 2021: "Payroll" also used Morse code, but differently. The domain name of the phishing kit URL was encoded in Escape. Then, the entire HTML code was encoded using Morse code.
Remember the cues for a phishing email:
- Poorly used language and punctuation, as well as poor spelling
- Blurry graphics or artwork
- Senders that are unknown to the recipient
- A sense of urgency that an action must be completed immediately
- Any attachments or links that are not expected or just make the hairs on your arms stand up