Top Ransoware Groups Wreak Havoc Since 2020; Tips To Keep Ransomware At Bay
July 31, 2023
There are many ransomware groups lurking in the shadows these days. They may come out from time to time, hold a few businesses for ransom and then slink back into the abyss. Later, they may reappear and do it again. Some disappear but under a different name and others morph into a new group. One thing that stays consistent is that they are always there. Lately, a few have made their marks. Here is information on them and what you can do.
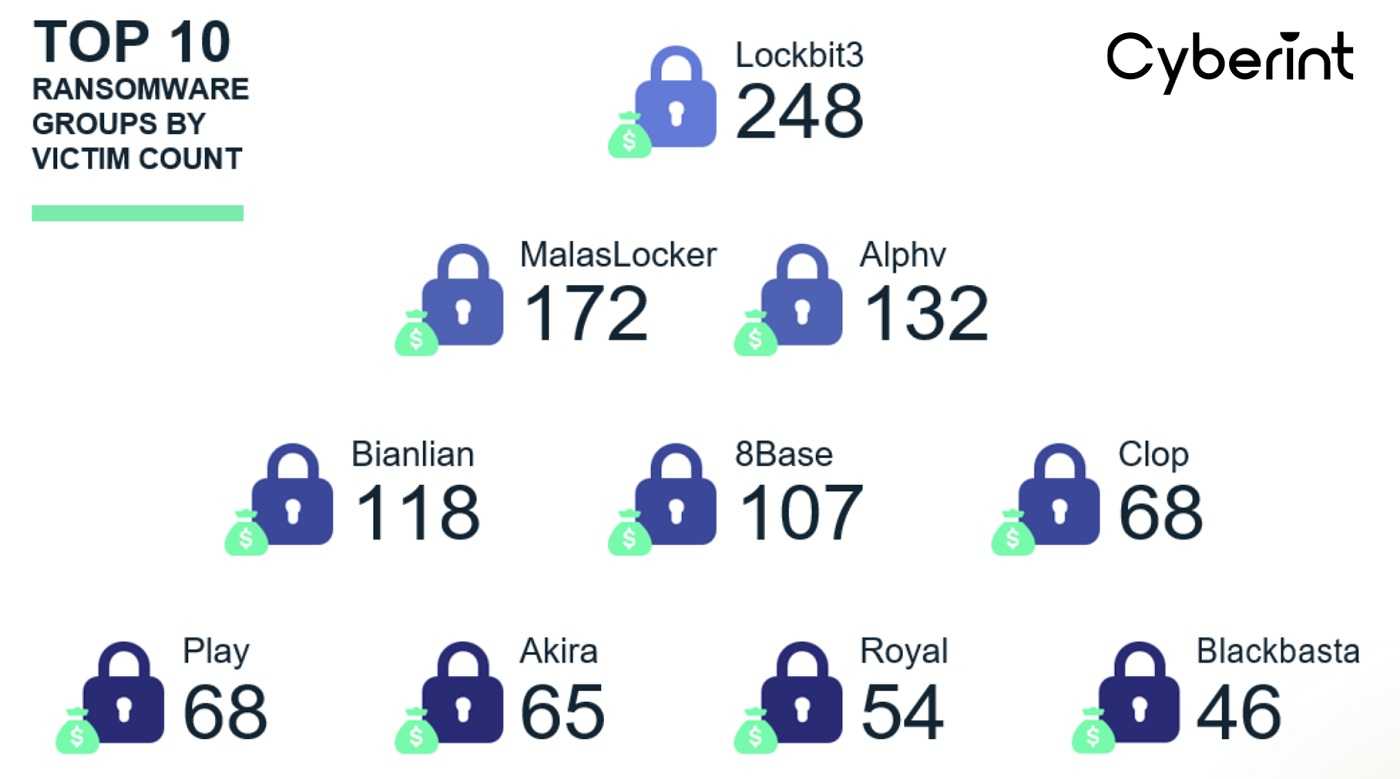
LockBit has established itself as a formidable force in the ransomware landscape and has been very active since 2021. There have been two versions of this group, LockBit 3.0 and LockBit 2.0. With an astonishing 892 and 869 documented attacks respectively, they have forced the cybersecurity community to stand up and pay attention. Many of their attacks are high-profile, such as the one on a children’s hospital in Toronto and the Royal Mail in the UK. According to the FBI, LockBit has been responsible for 1,700 attacks since 2020.
Conti, another notorious group, made its mark with 574 recorded attacks. However, in a significant turn of events in 2022, Conti experienced an implosion that led to its collapse. Despite its demise, the repercussions of Conti's activities continue to resonate within the cybersecurity community, as new groups have emerged from its ashes. Time will tell what these new threats will do.
In addition to LockBit and Conti, other ransomware groups have left their mark on the threat landscape. AlphV/BlackCat carried out 440 attacks, while Black Basta inflicted digital chaos with 228 incidents. Hive, Royal, and Vice Society have also made their presence known, each leaving a trail of ransomware attacks in their wake.
One notable group that has seen a significant rise in 2023 is Cl0p Ransomware. You may have heard of it, as it was connected to several attacks leveraging zero-day vulnerabilities in MOVEit and GoAnywhere MFT software. A couple of very recent attacks claimed by the group were against the cosmetic company, Estee Lauder and the largest U.S. airline, American Airlines. Currently ranking third for the year 2023, Cl0p's activities have caught the attention of cybersecurity professionals around the globe.
Despite the emergence of Cl0p and the rise of Medusa Team as a top threat, the overall rankings for the top groups have not undergone significant changes in the first half of 2023.
The sheer volume of successful attacks by these groups alone showcases the scale and magnitude of their operations, underscoring the urgent need for robust cybersecurity measures to protect organizations and individuals from their destructive activities.
What can you do?
Information like this is not merely for IT professionals or C-Level employees. Everyone plays a part in keeping information secure. While some ransomware gets into a network via vulnerabilities in the software, even more plants itself by successfully phishing employees.
Guidelines for keeping ransomware at bay:
 Don’t click links, attachments, or images in email that are unexpected or come from unknown senders.
Don’t click links, attachments, or images in email that are unexpected or come from unknown senders.
- Verify any requests for payments or money transfers independently of any email message received, especially if it isn’t expected.
- Back up important data on a regular basis.
- Make sure all systems and devices have cybersecurity software installed and it’s always kept updated.
- Enable two-factor authentication or multi-factor authentication on every account or system.
- Create strong passwords and change them regularly. Use a unique one for each account.
- Patch and update all software as soon as possible after they are released.