Have you heard enough of the Trojan Qbot? Well, that sneaky bot is not going away, nor is it sitting back and being quiet. In fact, per a report by Check Point Research, it’s been hanging around making a cybersecurity menace of itself all throughout the year, thus far. It’s not the only malicious news for the year either. The mobile Trojan SpinOk made its debut and that pesky MOVEit zero-day vulnerability has not moved an inch to stay out of the news.
What’s a bot to do?
Qbot (or Qakbot) has been in the cyber news a lot. It was first discovered in 2008, but has been consistently reinvented over time. It went from “merely” a banking Trojan to being able to steal passwords, payment card details, email information, and other things. It can evade anti-virus software and bypass other security measures.
What you can do
Since this is mostly distributed via spam email, always keep those peepers open for phishing lures in your messages. While it’s generally is in email, that doesn’t mean you won’t or can’t see it come along in text messages too. If you don’t know who sent the message or are not expecting any sort of link or attachment, don’t click them. Your sixth sense works, so listen to it when it comes to phishing.
The spin cycle
SpinOk is mobile malware that the researchers said has been downloaded 421 million times. Yikes! It’s a software development kit that has been trojanized and has ruined many popular games and apps. Many of those were found in, and later removed from the Google Play Store. SpinOk can steal sensitive device information and check out what is on the clipboard. Since this is in the development kit, it’s considered a supply chain attack. Likely, there are many more of those to come.
Our spin for you
Always use caution when downloading apps to your mobile devices. Use their official app stores and do plenty of due diligence. Check reviews for any hint of trouble. If the app only has raving reviews and not many of them, give it more time before you download it. This is one time you don’t want to be the early adopter of the latest trendy mobile app.
MOVEit on up
In May of this year, the software developer disclosed a vulnerability in its MOVEit Transfer and MOVEit Cloud products that attackers exploited to the moon and back. It was particularly popular with the ransomware group Clop. It was initially a zero-day, but a patch was created 48 hours later. Sadly, many organizations didn’t get on that and it continues to be exploited today. It hit 108 organizations worldwide and keeps on moving.
Get a move on it
Whenever patches and updates are released for your systems and device, get a move on it and apply them right away. This is especially important with previously found zero-day vulnerabilities because the attackers have already been active, even before the patch was released. The longer you wait, the more likely someone will make a move on you.
Other notable findings in the Check Point report on a global level
- The most prevalent mobile malware was SpinOk (Android spyware), Anubis (banking malware for Android), and AhMyth (Remote Access Trojan for Android).
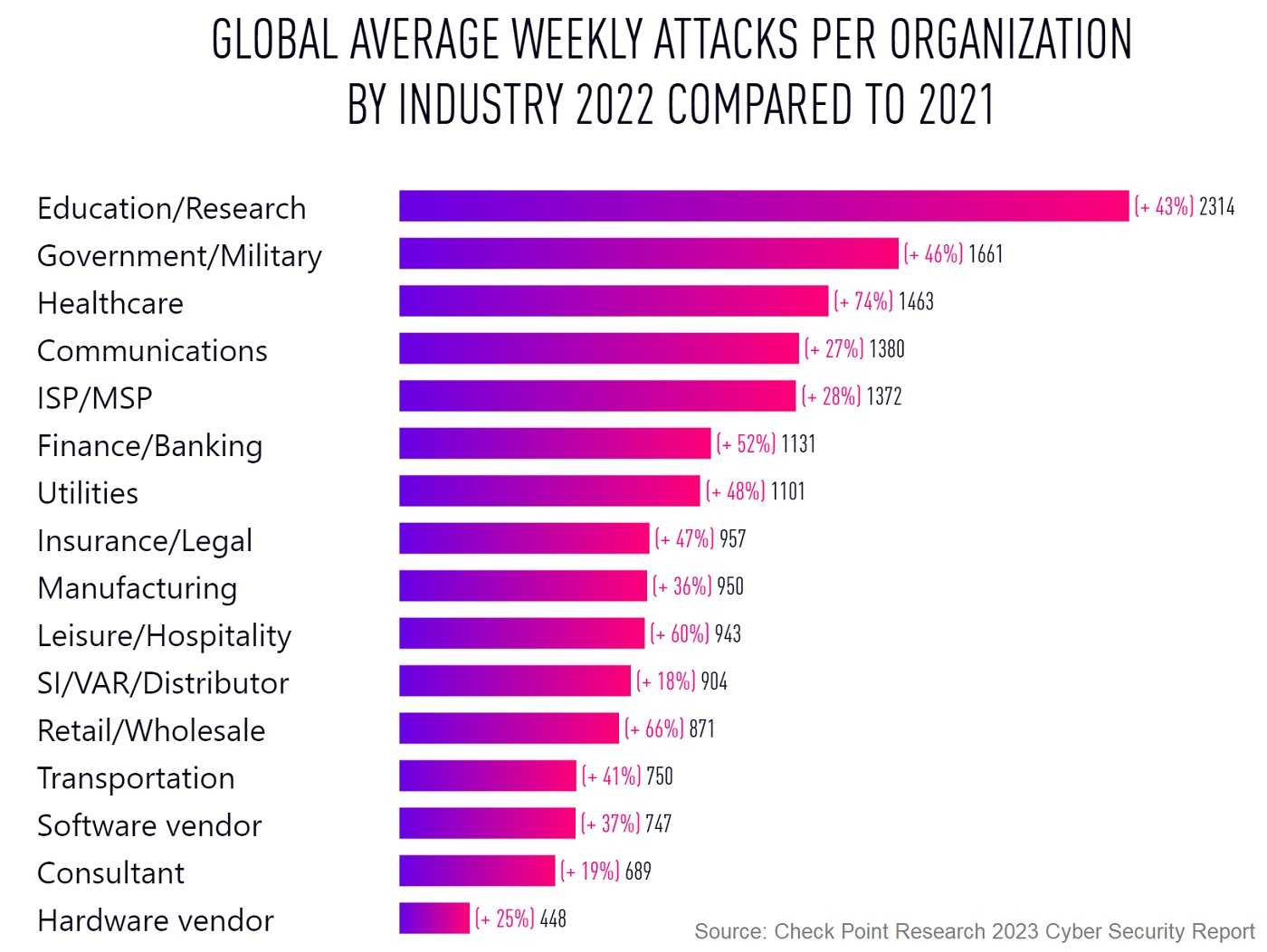
- The most exploited industries were Education/Research, Government/Military, and Healthcare.
- The top exploited vulnerabilities in organizations worldwide were Web Servers Malicious URL Directory Traversal, Apache Log4j Remote Code Execution, and HTTP Headers Remote Code Execution.